The US-based SOC 2 standard is starting to catch on in European businesses as well as other parts of the world. Although it’s a voluntary American standard, SOC 2 helps to raise cybersecurity maturity and increase business value.
While researching the latest trends and best practices in cybersecurity compliance, you may have seen increasing reference to the SOC 2 (System and Organization Controls) framework.
SOC 2 examinations were designed by the American Institute of Certified Public Accountants (AICPA) to help organisations ensure the protection of their data and the privacy of their client’s information. A SOC 2 assessment focuses on an organisation’s security controls that are related to overall services, operations, and cybersecurity compliance. SOC 2 examinations can be completed for many organisations of various sizes and across different sectors.
Although SOC 2 is typically a customer-driven compliance standard published by an American regulatory body, we are seeing a growing number of European organisations undergoing SOC 2 assessments. To help you determine if SOC 2 is right for your business, let’s examine why SOC 2 has started to catch on in Europe and the benefits it brings to non-American companies.
Why are SOC 2 assessments becoming more popular in Europe?
The rising use of SOC 2 in the U.S. over the past decade is largely due to the fact that many large companies wanted to be more proactive about their cybersecurity risk management. These organisations began setting forth requirements stipulating that their vendors must have a SOC 2 report ready as part of the due diligence process.
Over the past two years, a similar chain of events has started to play out in Europe: Increasingly, companies in certain key industry sectors want to review SOC 2 reports so they can determine that organisations along the supply chain have the necessary controls in place to protect the data of all parties involved. One example of this is in Germany with the C5 attestation, which has an over 80% overlap with SOC 2.
There are three primary sectors in Europe (especially within the UK) where there is an increasing demand for SOC 2: banking, insurance, and, most recently, central government. It makes sense that these sectors are some of the first to promote a more wide-ranging approach to cybersecurity compliance since they are among the most regulated fields in the world.
The rise in popularity of SOC 2 in the U.S., and now, increasingly, in Europe and other parts of the world, has undeniably been driven by the widespread adoption of cloud computing. According to Gartner, most organizations will leverage cloud as a business necessity by 2028.
Let’s explore two key benefits of leveraging SOC 2.
Moving from ISO 27001 to SOC 2
Right now, International Information Security Standard 27001 (ISO 27001) serves as the principal cybersecurity standard for much of the world, and is particularly favoured in Europe. However, we are noticing that an increasing number of European companies are embracing SOC 2 in addition to ISO 27001 to demonstrate a higher level of cybersecurity maturity. SOC 2 is even replacing ISO 27001 outright in some vendor contracts.
ISO 27001 certification is carried out against a strict controls framework that must be applied to the organisation, regardless of the size or sector, and the audit is pass/fail. With a SOC 2 report, the organisation gets to pick the categories of controls that are tested across five Trust Services Criteria (TSC): Security (required), Availability, Confidentiality, Processing Integrity, and Privacy. Ultimately, the independent assessor’s detailed SOC 2 report contains their expert opinion of how well the organisation meets the selected TSC to protect all aspects of its systems.
The SOC 2 report is more in-depth than an ISO 27001 pass/fail approach. In fact, the end result of a SOC 2 assessment (an extensive attestation report up to 100+ pages in length) tends to give a company’s partners and clients a higher level of assurance about their security posture compared to the end result of an ISO 27001 audit (a one-page certification letter). This is one of the leading reasons why the cybersecurity compliance norm in Europe is beginning to shift.
The SOC 2 historical lookback window
SOC 2 assessments can be carried out in one of two ways:
- A SOC 2 Type I assessment attests to the design and implementation of controls at a single point in time. The assessor reviews evidence from systems in their current state and produces a Type I report. This is not dissimilar to an ISO 27001 audit.
- A SOC 2 Type II assessment attests to the design, implementation, and operating effectiveness of controls over a period of time, usually between 3 and 12 months. In a Type II assessment, the assessor provides assurance that controls are not only designed and implemented, but that they have also operated effectively and as intended over the defined period.
The SOC 2 Type II report shows whether or not an organisation has historically been adhering to the controls they have in place. While a SOC 2 Type II assessment does take longer to complete, it offers an extra layer of trust to a potential customer or partner. A Type II report essentially says, “we didn’t have to scramble to reach this point. We’ve been taking cybersecurity seriously for some time now.”
Other benefits of a SOC 2 report
In addition to helping build trust with prospects, customers, and partners, there are other significant business benefits that a European organisation can unlock with SOC 2 compliance. Let’s take a look at a few of the biggest perks that should be considered.
A more competitive position
Possessing a SOC 2 report can give your European business a competitive edge over other organisations operating in your space. Not only can this help you increase revenue by closing more deals, but it can also help retain clients who may have otherwise explored a different company with proof of a more mature cybersecurity posture.
The ability to expand into the U.S.
As an American cybersecurity framework, SOC 2 adoption has become widespread in the U.S. over the past 10 years. SOC 2 is, in essence, required to do business with most large or well-known U.S.-based companies, even though it is voluntary and not required by law. In much of the same way that GDPR compliance (which is a law) has become key for American companies looking to sell in Europe, SOC 2 is now a unique selling point for European companies that want to expand into the U.S.
Future-proofing the business
The truth is that we are only going to see SOC 2 become more prevalent in Europe over the coming years. In addition to the three sectors mentioned above, the manufacturing and logistics sectors are starting to support SOC 2, especially in the UK. The assessment is also gaining traction in other parts of the world. Australia’s Consumer Data Right (CDR), for example, is now active in the country’s banking and energy sectors. The Australian government has acknowledged that SOC 2 reports can be used as a means to achieve CDR accreditation.
Does your business need SOC 2?
So, does your business need SOC 2? The short answer is that, if your clients are starting to ask for it, or if you are planning to expand in the U.S., then you should begin planning for SOC 2 without delay. However, even if that’s not the case for your business, you would be well-advised to initiate conversations with stakeholders in your organisation to discuss how SOC 2 could help facilitate future growth.
Why A-LIGN?
The best way to begin your SOC 2 is to reach out to a reputable, licensed auditor in the U.S. that will help you acquire a clearer understanding of where you need to start and what changes need to be made, as well as potential timelines. To make the entire process as efficient and convenient as possible, it’s also wise to choose a firm that has personnel operating in a European time zone, such as in the UK.
A-LIGN, the #1 SOC 2 issuer in the world, is proud to have 100 Europe-based auditors and more than 500 customers in Europe. A-LIGN is one of a few vendors with local offices and auditors in EMEA and APAC who can offer SOC 2 and other major U.S. cybersecurity frameworks, such as FedRAMP, CMMC and others. We are in a unique position to support companies headquartered in these regions but who also operate in the U.S. market.
Contact us today to get started on your journey to SOC 2 compliance.
It’s no secret that the cybersecurity compliance industry is in the middle of a big shift.
The demand for trusted, high-quality cyber assessments is skyrocketing, and organizations everywhere are looking for easier, more efficient ways to complete their audit cycles and leverage the process for increased security value at the same time. The opportunity for new ideas and innovation in the compliance industry is at an all-time high.
That’s why today I’m so excited to announce the next phase of our growth, as we welcome the team at Warburg Pincus on our journey. A-LIGN has always been at the forefront of cybersecurity compliance, relentlessly seeking ways to make audits and assessments more efficient while maintaining a high level of quality. The impact that the right strategic partner can have on a business like ours is undeniable. We experienced it over the last few years with FTV Capital – who remains an investor going forward – and we are fortunate to have Warburg Pincus at the table with us now.
Together, we will continue to innovate and meet the needs of this dynamic market by putting forward a bold vision for A-LIGN over the next few years. We will:
- Become the premier one-stop provider for fully integrated compliance solutions, from pre-audit readiness to final report.
- Leverage A-SCEND’s tech-enabled audit management capabilities to help organizations simplify and consolidate efforts.
- Expand our portfolio of cybersecurity assessments and services, including SOC 2, ISO 27001, HITRUST, FedRAMP, CMMC, penetration testing, privacy, and more.
- Reach more clients across the globe with the same customer-first approach that has always been at the core of A-LIGN’s recipe for success.
To our clients and partners: we are looking forward to finding new ways to help you navigate the complexities of cybersecurity compliance. This relationship will allow us to do even more for you, delivering new technologies and accelerating the value we can bring to your operations. Rest assured; we’ll continue to be committed to your success, providing the same services at the same level of excellence as we always have.
And finally, to our employees, or CLIMBERS as we call ourselves: I’m honored to work alongside you and proud of what we have accomplished together. I know you are all in on this adventure, and I appreciate the commitment you make every day to our clients and our team.
Let’s go climb together – the next mountain awaits!
Do you know the difference between FISMA and RMF? We’ve got you covered! Learn how FISMA is related to RMF, the certification process, and the benefits to your agency.
What is FISMA and how are the regulations related to RMF (the Risk Management Framework)? If your organization pursues federal contracts or works with a federal agency, the sheer number of security compliance certifications can seem overwhelming. Understanding the frameworks, processes, and benefits of these certifications can seem daunting. That’s why we’re here to help break down a well-known federal program, the Risk Management Framework (RMF), and the law that outlines the requirements that agencies must meet to achieve compliance, the Federal Information Security Modernization Act (FISMA).
FISMA requires federal agencies to develop, document and implement an agency-wide program to provide security for the information and systems that support the operations and assets of the agency. This includes assets provided or managed by another agency, contractor or other sources.
After its initial launch, FISMA was amended to include several modifications that modernize federal security practices to address ever-evolving security concerns. These changes resulted in less overall reporting, strengthened the use of continuous monitoring in systems, and increased focus on the agencies for compliance and documentation that is centered on the issues caused by security incidents.
What is RMF?
RMF was designed to effectively bring together all of the FISMA-related security standards and guidance to promote the development of comprehensive and balanced information security programs by agencies. According to NIST.gov, the stated goals are as follows:
- To improve information security
- To strengthen risk management processes
- To encourage reciprocity among federal agencies
More simply put, FISMA establishes the standards and requirements of an agency’s cybersecurity program and RMF helps determine how that program is implemented to meet those standards and requirements.
What is the RMF Process?
Essentially, RMF effectively transforms traditional Assessment and Authorization (A&A) programs into a more palatable six-step life cycle process that starts with preparation and consists of:
- The categorization of information systems
- The selection of security controls
- The implementation of security controls
- The assessment of security controls
- The authorization of information systems
- The monitoring of security controls
RMF has currently been implemented across the major sectors of the federal government, including:
- Federal “civil” agencies
- Intelligence Community (IC) agencies
- Department of Defense (DoD) components
If your agency falls under these parameters, it’s likely they rely on FISMA and RMF approved standards when it comes to your cybersecurity systems and procedures.
What are the FISMA Requirements within the RMF Process?
In order to comply with FISMA, an organization must go through the Assessment and Authorization (A&A) process with a Federal agency. To make this process as simple as possible, a Federal cybersecurity assessment can be divided into four general phases:
Phase I: Initiation Phase
- This phase includes preparation, resource identification and system analysis.
- This ensures that all senior officials are on the same page and agree with the drafted security plan.
- Testing should be performed before certain actions such as identifying key security officers, conducting an initial risk assessment, or an independent audit.
Phase II: Security Assessment Phase
- This phase includes security control Assessment and Authorization (A&A) documentation.
- Entities must verify that system controls are properly implemented as outlined during the initiation phase.
- Any discovered deficiencies in security must be corrected.
- At the end of the certification phase, risks to the agency, its systems and individuals will be obvious—which will allow for a clear decision-making process.
- When concluding this phase, the Authorizing Official will review any necessary security updates or adjustments.
Phase III: Security Authorization Phase
- This phrase includes a decision regarding authorization and documentation.
- Entities must determine if the remaining risks post-implementation of the security controls from phase 2 are acceptable.
- The information system owner, information system security officer, and security controls accessor (SCA) provide collaborative information to the authorizing official, who then determines if the final risk level is within the “acceptability of risk” boundary.
- The goal of this phase is to reach the required authorization to operate.
- A Federal agency may also issue an interim ATO at their discretion for a variety of reasons. Under this interim ATO, the agency outlines whatever actions must be completed to become fully authorized.
- If those actions are not completed by the agreed upon deadline, the Authorizing Official may deny authorization of the system.
- By the end of this phase, all documentation from phases 1 and 2 must be compiled into a final security authorization package—including an authority to operate decision letter.
Phase IV: Continuous Monitoring Phase
- This phase includes system configuration, security management, monitoring and reporting.
- Maintaining a high level of security through monitoring security controls, documenting any updates and determining if any new vulnerabilities develop is this phase’s focus.
- Detailed documentation is key, including tracking the current hardware, software or firmware version in use.
- Officers must also note physical modifications, like new computers or facility access changes.
The Benefits of FISMA/RMF Compliance
Although regulatory compliance is often viewed as a complicated undertaking for agencies, FISMA/RMF compliance is a completely different situation. RMF compliance by meeting FISMA requirements translates to heightened readiness for current and future cyber threats, with many benefits:
- Security: FISMA’s strict criteria and standards can greatly enhance an agency’s cybersecurity systems. Even physical disasters aren’t long-term setbacks—with FISMA’s regulations met, agencies can recover critical data almost instantaneously even after catastrophic damage to the tangible parts of their systems.
- Reputation Management: Reputation management and word-of-mouth are an integral part of business management. The general public is becoming increasingly knowledgeable on cybersecurity issues, such as data privacy, and a data breach could result in a negative outlook on your agency.
- Scalability: One of the benefits of FISMA is that it provides different implementation options depending on the levels of potential impact for an organization or individual if there were a security breach. A breach of security could be a loss of confidentiality, integrity, or availability. The three FISMA implementation levels are: low, moderate and high.
- Understanding the Competition. In the process of categorizing risks, you will gain a valuable understanding of the marketplace, giving you an advantage over your competitors.
Achieving RMF Compliance
For organizations looking to win government contracts, the RMF compliance framework provides clear requirements for the development, documentation and implementation of an information security system for its data and infrastructure.
Combine Multiple Audits to Save Time and Resources
Many organizations have a huge opportunity to combine multiple audits to save time and resources while completing compliance assessments.
Due to an increase in technology and the evolution of the cybersecurity compliance landscape, organizations of all sizes are finding themselves tasked with conducting various compliance audits throughout the year to show both their customers and their industry peers that they take the privacy and security of data seriously. In many cases, these audits are being conducted in a reactive manner, costing organizations time and resources.
There is a better way to conducting multiple audits.
In our 2021 Compliance Benchmark Report, we asked more than 200 cybersecurity, IT, quality assurance, internal audit, finance, and other professionals about their compliance programs. We learned that the majority of organizations, regardless of industry, do not have a strategy in place to reduce redundancies when completing multiple compliance audits over the course of each year.
In fact, 85% of respondents conduct more than one audit every year, yet only 14% consolidate audits into a single annual event. This means organizations are using their resources inefficiently and scrambling to execute on compliance programs.
Who Consolidates Their Audits? Not Many.
With so much revenue on the line, and so many compliance requirements in play, it seems logical that organizations would conduct multiple audits in a strategic, unified manner. But this is far from true.
Industry Can Drive Audits
It makes sense that many organizations look to industry-specific guidelines on which audits are required to ensure they remain compliant with industry regulations. When looking across every industry, we found that healthcare is the industry most likely to not consolidate audits. In fact, 94% of respondents within the healthcare industry stated they conduct multiple, individually-managed audits and assessments.
Companies in the technology sector not only conducted the highest number of audits, but also had the highest rate of consolidated audits at 26%. They were also the industry with one of the highest usage rates of technology, using software to help prepare audits and streamline the process 31% of the time, which plays a big role in the ability to consolidate audits.
Size [Also] Matters
The number of audits an organization conducts per year can be impacted by many factors including its size, industry, annual revenue, and more. In fact, we found that most organizations with more than $1 billion in revenue typically conduct more than six audits per year.
We found that 60% of organizations that surpass $5 million in revenue typically complete more than four audits each year. This far exceeds the 21% of organizations that earn less than $5 million in revenue and complete more than four audits per year.
Time & Resources Wasted
Did you know that 27% of respondents stated one of the biggest challenges associated with their audit process is evidence collection? When done as a manual process, it is tedious and takes up valuable resources, not to mention that teams or departments operating in a silo will often gather the same evidence to be used at various points over the course of the year. This not only creates redundancies in the efforts at an organization, but it wastes valuable time.
Organizations that work through multiple audits as disjointed projects often experience a stress-filled and frustrating audit situation for all parties involved. But this isn’t only felt during the audit process itself; it’s also felt during the preparation.
In fact, more than 50% of respondents stated they spend one to two months preparing for each audit or assessment, and 17% stated they spend six months or more preparing for an audit or assessment. The time spent preparing for every audit adds up quickly, especially when organizations are conducting more than one audit every year.
If, however, organizations consolidate audits into a single timeline, it can greatly ease the disjointedness of auditing. An added bonus? Because the audit is strategically planned and expected, it becomes less of a last-minute scramble.
Key Takeaways
The findings shared in our Compliance Benchmark Report illustrate the impact of not implementing a strategic, year-round approach to preparing for audits and assessments. Basically, the combination of a disjointed auditing process with the time and resources required to conduct manual evidence collection creates a perfect storm of chaos.
It comes down to this: Conducting multiple audits throughout the year is complex, but it doesn’t have to be chaotic. Taking a proactive approach to preparing for, and conducting, audits can create efficiencies that help an organization optimize evidence collection and streamline how that evidence is used. And perhaps the biggest benefit? It frees up resources to focus on the more strategic side of the business.
Download the 2021 A-LIGN Compliance Benchmark Report
Common SOC 2 Questions Answered
If you’re new to cybersecurity compliance, you’re probably wondering, “what is SOC 2?” The first step is understanding what information will be audited, what employees are involved in the audit, and what is included in the overall audit process.
Undergoing a SOC 2 can be complex, so we have provided answers to eight common SOC 2 questions on auditing and reporting.
Whether you have just started your business or you’re running an established organization, you know that handling the data of your client is very important. A SOC 2 report provides information about how effectively you are managing the security, privacy, and integrity of a client’s sensitive information.
1. Why is SOC 2 compliance important?
As you know, data privacy and security have never been more important. When working with large customers or those in regulated industries, you will likely be asked to provide proof of your SOC 2 controls, especially if you operate a cloud or services business. Below is a list of common risks related to delaying compliance assessments:
- Less competitive position: Many organizations are required by laws or regulations to ensure the security of their data or their customers’ data. Organizations and customers will typically work with partners and vendors who can demonstrate security controls, practices and compliance over a period of time through industry standard reporting and recognized frameworks, such as SOC 2.
- Drawn out sales process: At some point, a prospect will probably ask for your SOC 2 report before moving any further. Since SOC 2 is a rigorous framework, it is not something that can be completed overnight. Most often, an established SOC 2 framework can take several weeks, from start to finish, to demonstrate evidence of controls and perform the audit. It requires planning, thought, ongoing cybersecurity controls, and the help of an external auditing partner.
- Lack of consumer trust: A SOC 2 report sends a signal to customers that your organization prioritizes IT risk, ethics, security, and the protection of their information and data in delivering services. Obtaining a SOC 2 report indicates a level of maturity around IT security, technology and business. Without a SOC 2 report from a licensed certified public accountant (CPA), customers have no way of verifying that their data is being secured and well-placed. Without this trust, it is very difficult to do business.
- Vulnerability to security threats: One of the most valuable outcomes of pursuing a SOC 2 attestation is improving and maintaining the strength of your own organization’s cybersecurity posture. SOC 2 is comprehensive and covers a wide range of controls. A SOC 2 report can be leveraged to identify new potential risks, threats, security controls or processes to implement at your organization. These new processes cannot only strengthen security controls at your organization, but can also improve metrics, operations and service delivery to customers.
2. What are the Trust Services Criteria?
The scope of your SOC 2 audit report is dependent on how many of the Trust Services Criteria (TSCs) your organization needs to focus on to fulfill your client requirements. The TSCs that you can choose from, include:
- Security (Common Criteria) – The protection of information, data or systems throughout their lifecycle. Security controls are in place to protect against unauthorized access, unauthorized disclosure, and damage to systems that could affect other criteria beyond the Security Category. Security controls are designed to include a wide array of risk-mitigating solutions, such as endpoint protection and network monitoring tools that prevent or detect unauthorized activity. Entity-level and control environment topics are also considered to provide that the necessary controls are in place to govern organization wide security. Each SOC 2 report issued covers the Security category at a minimum.
- Availability – Considers controls that demonstrate systems maintain operational uptime and performance to meet stated business objectives and service level agreements. Availability does not set a minimum acceptable performance level, but it does address whether systems include controls to support and maintain system operation, such as performance monitoring, sufficient data backups and disaster recovery plans.
- Processing Integrity – Ensuring that data is processed in a predictable manner, reasonably free of accidental or unexplained errors. In other words, the information produced or manipulated by your systems needs to be complete, accurate, valid and reliable, to meet stated business objectives and SLAs. Due to the number of systems used by an organization, processing integrity is usually only addressed at the system or functional level of an organization.
- Confidentiality – Requires companies to demonstrate the ability to protect confidential information throughout its lifecycle, including collection, processing and disposal. The specific requirements for Confidentiality related controls may be defined by laws and regulations, as well as internal management or stated business objectives and SLAs. Confidential information may include personal information, as well as other information, such as trade secrets and intellectual property. Controls for Confidentiality include encryption and identity and access management.
- Privacy – Covers communication, consent, and collection of personal information, and verifies appropriate parties have access to that information and what can be done with it. Controls for Privacy include privacy policies and consent management mechanisms.
3. What is the difference between SOC 1 and SOC 2?
A SOC 1 audit is the ideal audit for organizations that handle, process, store or transmit financial information. SOC 1 reports demonstrate that you have the necessary quality controls in place to protect your customers’ financial reporting. These industries may include payroll processors, collections organizations, data centers and software as a service (SaaS) organizations.
A SOC 2 report highlights the security controls in place that protect and secure an organization’s system or services used by its customers. Unlike a SOC 1, the scope of a SOC 2 attestation tests the design and implementation of controls to protect the processing and storage of data that does not directly impact the financial statements of user organizations. Organizations of many sizes and industries can benefit from a SOC 2 assessment, as the audit can be performed for any organization that provides a variety of services to its customers.
4. What are the different types of SOC 2 reports?
When it comes to SOC 2 reports, two options are available: Type I and Type II. The best fit for your organization depends on your specific requirements.
- SOC 2 Type 1 – With this report, the service auditor can validate the presence of the organization’s description of their system and the sustainability of the design of control activities against the selected TSC. The auditor reviews and reports how well the organization has designed the system and its controls considering the selected TSCs as of a specific date in time.
- SOC 2 Type – With this report, the organization will receive a more comprehensive report as compared to Type 1. The report focuses on the description of your organization’s systems along with the operating effectiveness of controls with the service auditor’s test results included within the report. In addition, a Type 2 report gives a historical view of an organization’s environment to determine if the organization’s internal controls are designed and operating effectively over a defined period of time, ranging from three to twelve months typically.
5. What does a SOC 2 report focus on?
A SOC 2 report includes overall processes and controls as described by your organization and the auditor’s assessment either at a point in time (Type 1 Report), or over a period of time (Type 2 Report). This report will include a description of your system and the suitability of the design, and potentially the operating effectiveness of its controls relative to your security posture.
When you receive your SOC 2 report, you can share a version of the report with your customers, vendors, and stakeholders, when appropriate. This shows that your organization has the appropriate policies, procedures, and controls in place to manage and mitigate the key threats and vulnerabilities that pose a risk to their environment.
There are typically four sections to a SOC 2 report:
- Section 1: Assertion of Management – Management is attesting to the accuracy of information provided during the audit. This includes a summary of the details regarding the SOC 2 attestation.
- Section 2: Independent Service Auditor’s Report An independent, external Service Auditor provides an opinion, or summary, of the results of the audit performed.
- Section 3: Description of Client’s System Throughout the Review Period – Includes a number of descriptions about various organizational details associated with the system being reviewed, including but not limited to, company background, services provided, infrastructure, controls, processes, employees, policies and more.
- Section 4: Trust Services Category, Criteria, Related Controls and Test of Controls – Includes details of the organization-specific control activities specified by the service organization and tested by the Service Auditor.
- Section 5 (Optional): Other Information Provided by the Service Organization – Additional information provided by management, where applicable.
6. What areas are commonly reviewed during a SOC 2 assessment?
SOC 2 reports cover an assessment of an organization’s security controls against the in-scope TSC. The list of items and areas within your organization that will need to be reviewed typically requires the involvement of various organizational groups. Examples include entity-level, control environment, endpoint protection, network monitoring, unauthorized activity prevention controls and more. During a SOC 2 audit, document collection, review, and discussion can take several weeks from start to finish to demonstrate evidence of secure controls and perform the audit. The basic list below demonstrates the importance of starting your assessment preparation early as many different areas of your company will be involved and held accountable for providing their information.
For the requirements listed below, you will need to involve your human resources department:
- Organizational charts
- New hire processes
- Employee handbook
- Background checks
- Reporting relationships
- Service-level agreements (SLAs)
For other areas of the SOC 2 audit, the requirements will be the responsibility of your IT team, such as:
- Shared network drives
- Change approvals
- Master list of system components
- User access to systems
- VPN authentication
- Anti-virus software
- Network authentication and configuration
Many of your organization’s cybersecurity standards, settings and processes will also be evaluated, including:
- Information security policies
- The security of your company website
- Monitoring tools
- Incident response policy
- Risk assessment policy and risk assessment
- Network diagram and firewalls
- Encryption settings
- Internal controls matrix
- Third-party and vendor policy and assessment
7. What are some tips for companies as they prepare for an audit?
Before beginning the SOC 2 audit, it is important that your organization is well-prepared to avoid any delays in assessment or additional costs. To ensure you earn the SOC 2 report in a timely manner, it is important that you consider following a few basic guidelines
- Stay up-to-date on standards
- Review recent changes in organizational activity
- Create a timeline and delegate tasks
- Review prior audits (if applicable)
- Organize data and gather evidence ahead of fieldwork
- Review requests and ask questions
- Evaluate results
8. How do I select the right audit partner?
Ensure your audit partner has the right qualities and they:
- Are licensed
- Undergo audits themselves
- Are properly staffed
- Respond within 24 hours
- Offer premium audit software
- Provide a comprehensive suite of services
Next Steps
When beginning the SOC 2 compliance journey it is important to engage a professional and certified auditing firm to work with you.
Do you still have questions regarding a SOC 2 audit and report? Let our SOC 2 experts guide you through the process.
As a licensed CPA firm and one of the top issuers of SOC 2 reports in the world, A-LIGN has the people, process, and technology you need to help your organization reach the summit of your potential as it pertains to compliance.
A SOC 2 in 14 days? We’ve completed thousands of them and we can say with authority that this is misleading. As auditors, we believe in accuracy, so we wanted to share what it really takes to complete a SOC 2 and how to get it done as quickly as possible.
The other day I got a call from a fast-growing startup company in the data analytics space asking if we could do a SOC 2 in two weeks “like other companies do.” This isn’t the first time I’ve received this question – in fact, lately, it’s coming up more and more. The conversation that ensued went something like this…
Me: Two weeks? What’s driving that timeline?
Client: I see ads all the time about getting a SOC audit in 14 days. Are you doing that?
Me: Ahh, I’ve seen those too. I’m afraid the reality is a bit more complicated.
Client: Isn’t that the whole point of SOC 2 automation software – simplifying it?
Me: (shaking head) Ok, let me explain…
Setting the Record Straight: SOC 2 Audits Take More Than 14 Days
Here’s the thing. We’ve performed thousands of SOC 2 audits. In fact, A-LIGN is the top issuer of SOC 2 reports in the world. We’ve produced reports for companies of all shapes and sizes, across all industries and around the globe. We know the ins and outs of the process – where companies struggle, where they trip up, and where the opportunities are to move faster.
So, we can say this with a reasonable degree of authority: A SOC 2 can’t be completed in 14 days without any preparation.
Only Part of Your Audit Can Be Done in 14 Days
To help illustrate why – and where the confusion is likely coming from – here’s a little diagram:
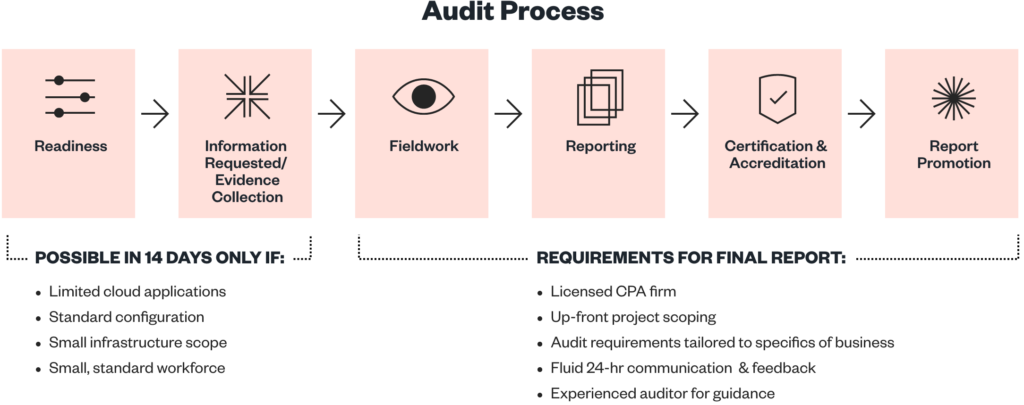
As this picture shows – when you see something that says, “14 days to SOC 2,” it’s actually only referring to the first part of the process. They aren’t talking about your completed SOC 2 report, which is your ultimate goal. The so-called “14-Day SOC 2” is a way of saying that, under certain circumstances, an automated system can get you a bunch of data that’s required to begin your audit in as little as 14 days. You won’t get a final report in that timeframe – you’ll only set the stage to get it produced.
Furthermore, that initial portion of your assessment can only be done if your environment meets a specific set of criteria. For example:
- You may need to be running your entire business from a limited set of cloud apps, such as AWS, Jira, GitHub, and a few others
- Those systems and the rest of your environment may need to be configured in a standard way
- Your infrastructure footprint probably needs to be small, simple, and consistent
- Your company probably can’t be too big – around 50 employees or under – and you’ll likely need a relatively standardized workforce in terms of roles and functions
The minute you start to introduce complexity at your company – in systems, processes, configurations, or your workforce – that’s when you’re going to see your SOC 2 take more time. Why? Because ultimately your auditor’s objective is to assess your cybersecurity practices, and the more complex your organization is, the more complex those practices will naturally be.
A more appropriate ad would read “14 days to gather information for your SOC 2” – or something similar. That’s not as catchy – but it is more accurate, and as auditors, we care deeply about accuracy.
Understand the Full Scope of Your SOC 2 with These 10 Questions
Alright, you’ve made it this far, and perhaps you are thinking that 14 days even to get ready for a SOC 2 sounds pretty good. And you’d be right – that would be fantastic. Just remember when something looks too good to be true, it often is. Do your due diligence by asking these questions:
1
After I’ve gotten through those 14 days, what else needs to be done – and by whom – so I can earn my final report?
2
Are there areas of my environment that can’t be instrumented or automated –– and who is responsible for populating this evidence? In particular, ask about:
- Legacy systems, data center systems, non-cloud systems
- Coverage across user workstations and mobile devices
- Differences between the health check that a tool provides and the evidence required to support it (for example, a report of where antivirus is supposed to be installed vs the actual evidence of the installation on each device)
- Observations for physical and environmental security concerns (including management of the maintenance records for applicable systems)
a. Legacy systems, data center systems, non-cloud systems
b. Coverage across user workstations and mobile devices
c. Differences between the health check that a tool provides and the evidence required to support it (for example, a report of where antivirus is supposed to be installed vs the actual evidence of the installation on each device)
d. Observations for physical and environmental security concerns (including management of the maintenance records for applicable systems)
3
For new policies that need to be developed – are templates provided enough for the context of your business? How will you customize them properly? What is the timeline required for implementation and training so I can show effectiveness against the policy control?
4
What is the process for instances when the data produced by the automation tool is not sufficient for the needs of the audit? Requirements fall through the cracks more often than you’d think, especially in more complex environments. This is commonly experienced when testing Sample Populations for Type 2 audits.
5
Who will project manage your SOC 2? When you have questions, who is available to address them? Does your software vendor know enough about SOC 2 to help in a meaningful way? What if their advice conflicts with your auditor? How quickly can you get questions answered with all those parties involved?
6
What is the process for evaluating, questioning, commenting on, and supplementing evidence when questions need to be addressed? Are those changes tracked in a software tool, or will you still need to rely on email and spreadsheets?
7
Who will my auditor be? How do I choose them and what is the transition like? Do they have a good reputation? Have they successfully published reports that stand up to demanding customers? Are they superior to the auditor used by your competitors?
8
Are there other assessments that need to be coordinated with your SOC 2, for example, penetration testing, vulnerability assessments, risk assessments, ISO 27001 certification, FedRAMP certification, etc.? Who will conduct these and how will information be shared?
9
How much evidence is needed to satisfy time-based requirements (particularly for SOC 2 Type 2 reports)?
10
Who is responsible for resolving disputes with the auditor?
Do the Right Thing, Always
One of A-LIGN’s core values is “Do the Right Thing, Always” – which is why we felt it was important to help people understand how the SOC 2 process actually works and what to expect from it, especially for those people going through it for the first time.
Our SOC 2 engagements are thoughtfully planned and professionally executed, leverage our expert auditors’ many years of experience, and include complimentary software and automation to get you through your SOC 2 as quickly and efficiently as possible.
StateRAMP provides a comprehensive security framework designed to improve cloud security for state and local governments. Learn the ins and outs of the StateRAMP compliance framework its relationship with FedRAMP and how StateRAMP could impact your business.
As cyberattack attempts carried out against state and local governments continue to become more prevalent, government agencies are in dire need of a way to modernize and systematize their cybersecurity practices — especially regarding cloud technologies. That’s where the State Risk and Authorization Management Program (StateRAMP) comes in.
According to Comparitech, various ransomware attacks cost the U.S. government close to $19 billion in 2020. And recent ransomware attacks on state-run facilities have highlighted the importance of increased and improved cybersecurity measures for state and local governments.
StateRAMP provides a comprehensive security framework designed to improve cloud security for state and local governments. It delivers a uniform approach to verifying that cloud service providers (CSPs) meet the standards and regulations needed to do business with state and local governments.
As I outline the details of the StateRAMP compliance framework and its relationship with the Federal Risk and Authorization Management Program (FedRAMP) you will see how, and if, this could impact your business.
The StateRAMP and CSP Relationship
As mentioned above, StateRAMP was created to help state and local government agencies manage and verify the cybersecurity posture of third-party vendors that provide cloud technology solutions, also known as CSPs. This is important because CSPs have been replacing on-premise information technology (IT) solutions at a rapid rate over the past 10+ years.
CSPs offer government agencies cloud computing solutions and services like Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS), all of which are designed to improve an organization’s agility and scalability. Gaining advanced storage, computing, and analytics capabilities has become essential for many government agencies to increase collaboration and remote accessibility while gaining deeper insights into their data.
As government agencies adopt StateRAMP to enhance their cybersecurity posture, CSPs that respond to RFPs in those states will need to prove they are StateRAMP authorized. This will be a requirement for any CSP proposals to be considered by certain local government agencies.
StateRAMP’s Solution for State-based Cybersecurity
The StateRAMP framework was created by the StateRAMP non-for-profit organization in response to the encroaching cyber threat crisis that stands to disrupt modern life in unprecedented ways. According to StateRAMP, the program’s purpose is to:
- Help state and local governments protect citizen data.
- Save taxpayer and service provider dollars with a “verify once, serve many” model.
- Lessen the burdens on government.
- Promote education and best practices in cybersecurity among those it serves in industry and government communities.
Protecting Citizen Data
In the recent onslaught of ransomware attacks, it is frequently citizen data that’s held hostage by threat actors who demand a payout. This data is often personal identifiable information (PII) that, if exposed, can allow hackers to commit identify theft or monetize the stolen data on the dark web.
Because state and local government officials are elected to serve the needs of their citizens, keeping personal data safe is a major priority.
Verify Once, Serve Many
StateRAMP makes things easier for CSPs by allowing them to transfer their credentials and certifications across a set of uniform standards. The “verify once, serve many” model was designed so CSPs only need to have their cloud offering or product authorized once to confirm its cybersecurity standards are adequate. This authorization is then enough to be recognized by other government agencies that adopt StateRAMP.
Government employees and officials are able to join StateRAMP at no cost as the program is entirely vendor-funded. This ensures enhanced cybersecurity is accessible for all state and local government agencies, regardless of size or budget.
Lessening the Burden on Government
Related to the last point, the StateRAMP model alleviates strain on state and local governments by removing the need for them to conduct redundant security assessments. In addition to being cost-efficient because StateRAMP removes the need for repetitive CSP security assessments, it saves countless hours and staffing needs that could be better utilized elsewhere.
For example, before StateRAMP, a government agency might have to review a dozen CSP vendors that responded to an RFP, even if they knew only a few of them would likely have acceptable cybersecurity standards in place. With StateRAMP, governments don’t have to waste valuable resources doing assessments for organizations that are severely lacking in cybersecurity maturity.
Promoting Cybersecurity Education and Best Practices
In the constantly evolving landscape of cybersecurity and compliance, it can be tough to stay up to date on the latest developments and regulations. StateRAMP aims to be as transparent as possible about policies and procedures, making cybersecurity knowledge available for anyone who wants to learn. In fact, the StateRAMP website provides a wealth of documents, templates, and other resources related to StateRAMP compliance.
After all, StateRAMP was designed to ensure government agencies and CSPs truly understand the reasoning and mechanisms behind the StateRAMP framework.
How Does StateRAMP Work?
Much like FedRAMP was created to provide a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services that store, process and transmit federal information, StateRAMP was designed to do the same for state and local government agencies.
StateRAMP’s Security Assessment Framework process is modeled after the National Institute of Standards and Technology (NIST) Risk Management Framework. Its primary requirements for CSPs seeking authorization include:
- Compliance with the security standards listed in NIST Special Publication 800-53 Rev. 5.
- A relationship with a Third-Party Assessment Organization (3PAO) that serves as a partner and educator throughout the entire process.
- Producing an in-depth security report in collaboration with a 3PAO that proves the organization has all the necessary controls in place and meets all requirements for authorization.
- Participating in continuous monitoring to demonstrate that the organization continues to maintain StateRAMP compliance.
To have a cloud offering or product become StateRAMP authorized, CSPs must work with their 3PAO to identify their impact level category based on the type of government data they handle, and the consequences that would result if a breach were to occur.
Each of the four categories corresponds with a defined set of security controls which align with familiar FedRAMP impact levels:
- Category 1 – This is the baseline any CSP has to meet. It maps to systems that involve publicly available data. Category 1 aligns with the “low” impact level in FedRAMP.
- Category 2 – This category covers data that is not available to the public, such as PII. Category 2 aligns with the “low” impact level in FedRAMP and contains some elements of the “moderate” impact level control baselines. Category 2 will continue to be developed and validated throughout this year.
- Category 3 – This category involves confidential data and systems that are of high criticality to the continuity of government. Category 3 aligns with the “moderate” impact level in FedRAMP.
- Category 3+ – This category is reserved for FedRAMP High authorized systems for reciprocity with StateRAMP.
StateRAMP also provides an official data classification tool that includes a brief survey to help government agencies determine what StateRAMP security category requirements they need to include in their RFPs. This tool can also help CSP better understand the StateRAMP security categories and what they entail.
Why Is StateRAMP Necessary?
With so much overlap between StateRAMP and FedRAMP frameworks, you may be thinking, “Why doesn’t a CSP just seek FedRAMP authorization for their products and achieve the same security outcome?”
It’s a fair question. FedRAMP built a reputation as a model security program over the past 10 years and has authorized hundreds of cloud products. Prior to this year, many CSPs that offered cloud solutions to state and local government agencies found themselves using FedRAMP security guidelines, but were still unable to achieve official FedRAMP authorization. This is because FedRAMP was specifically designed for federal agencies. This means organizations cannot obtain FedRAMP authorization without doing business with the federal government.
For this reason, a coalition of industry members decided to form the StateRAMP not-for-profit organization to bring FedRAMP’s standardized cloud security approach to state and local governments. As a growing number of states plan to join StateRAMP (the StateRAMP organization is in talks with hundreds of government officials across 35 states and counting), it would be wise for CSPs to start preparing for StateRAMP authorization sooner rather than later.
In addition to enhancing cybersecurity by providing a uniform approach to risk-based management, accomplishing StateRAMP authorization can help CSPs save time and resources by allowing them to re-use their security authorization across multiple government agencies. StateRAMP also increases transparency and trust between government agencies and CSPs, reducing the likelihood of any miscommunication, oversights, or errors that could affect potential contracts or working relationships.
Note: For CSPs that do business with both federal and state/local government and are already FedRAMP authorized, a reciprocity program is in process that will allow these organizations to take an accelerated path to StateRAMP authorization.
Get Started with StateRAMP
In a time when the public and private sectors are realizing they must work together to keep out threat actors, StateRAMP is a significant milestone for transparency, standardization, and community in cybersecurity.
If your organization requires StateRAMP authorization to do business with a state or local government agency, A-LIGN can help put you on the right track. Drawing from our extensive experience as a 3PAO for FedRAMP, A-LIGN is one of the only StateRAMP-registered assessors on the market today.
How HITRUST Certification Can Satisfy Your SOC 2, ISO 27001, and FedRAMP Requirements
The HITRUST CSF pulls from many major pre-existing frameworks to provide a complete, certifiable security standard. Learn about the many different cybersecurity frameworks that can be incorporated into your organization’s HITRUST assessment to help streamline your approach to compliance.
Confusing. Difficult. Expensive. Overwhelming. Do you associate these words with the plethora of cybersecurity assessments available today? Many organizations are unsure of where to start and what assessments or audits will best prove to their customer that they take data security seriously.
While there are a variety of different audit options for any organization, the HITRUST CSF provides comprehensive, scalable, flexible and prescriptive solutions for organizations. By pulling from many major pre-existing frameworks and working with organizations to better understand their needs, the HITRUST certification provides a complete, certifiable security standard. Let’s first define HITRUST CSF and then take a look at the many frameworks that can be incorporated into the assessment. You’ll see how beginning with HITRUST CSF will streamline your approach to compliance!
What is HITRUST CSF?
The certification provides an integrated, prescriptive framework that works primarily with the needs of the healthcare industry in order to comply with the necessary cybersecurity standards. However, this framework is able to be scaled for various sizes and types of organizations in any industry and their control systems.
It also allows for the tailoring and scaling of controls with HITRUST oversight to ensure that the integrity of the systems remain intact, and applications remain consistent. With a comprehensive framework for organizations of any size, system, or regulatory requirement, the HITRUST certification allows for organizations to easily assess their current compliance while providing implementation requirements based on an organization’s risk factors.
What are the types of HITRUST assessments?
HITRUST has two methods to approach complying with the HITRUST CSF with each providing their own unique benefits, depending on the needs of an organization. They include the self-assessment, and a validated assessment, which leads to HITRUST certification. They each function on varying degrees of assurance based on the cost, effort level, and time required. The benefits of any type of HITRUST CSF Assessment include:
- Scalability for organizations of any size
- Understand their current level of compliance with the CSF and areas of general risk
- Stay up-to-date on the latest security risks
- Save time on numerous compliance audits
HITRUST self-assessment
The HITRUST CSF is designed to be completed by an organization in order to minimize time and resources when demonstrating compliance with the CSF. The self-assessment can also be used as a stepping stone to a validated assessment. The benefits include:
- Low to medium level of effort needed to complete
- Can be quickly completed
- Lower investment in terms of budget and time
However, one of the drawbacks of a self-assessment report is that it provides the lowest level of assurance, as no validation comes from the self-assessment: it simply results in a HITRUST issued CSF Self-Assessment report.
Validated or certified assessments
A validated assessment is a more rigorous assessment process, with an increase in assurance level performed by a CSF third-party assessor firm to validate the information gathered by the organization. One of the benefits of receiving a CSF Validated Assessment includes providing an increased assurance level to the relying entity.
The process is more rigorous due to testing conducted and authorized by an external CSF assessor at the organization. A validated assessment requires a medium to high level of effort for completion, due to the rigorous testing procedures. Upon completion, HITRUST reviews the complete assessment and issues a validated report as the outcome if the organization has failed to receive a rating of ‘3’ or higher on any of the controls. If an organization received at least a ‘3’ on HITRUST’s scale and has shown a high level of maturity they will receive a certified assessment.
The benefits of receiving a CSF certified assessment include:
- A report that is good for two years, with an interim assessment completed at the one-year mark
- The most complete assurance level certified by HITRUST
- Results in an official certification to provide to clients, partners, etc.
A certified assessment is only earned once an organization successfully demonstrates that they are able to meet all of the controls in the CSF required for certification at the appropriate level based on organizational needs.
The HITRUST framework & cybersecurity assessment integrations
HITRUST did a great job of mapping CSF requirements to existing standards for other cybersecurity assessments. Once an organization earns HITRUST certification, they may have already covered all of the requirements for a variety of other frameworks. If your organization uses a firm (like A-LIGN) to conduct your audits, you avoid hiring multiple auditors to earn other cybersecurity certifications.
The external assessor firm has the ability to conduct multiple audits at once, de-duplicating tasks. For example, if you use an external assessor firm that handles multiple security frameworks, and are working toward your HITRUST CSF, your auditor can also complete all of the tasks for SOC 2, NIST 800-53, ISO 27001, FedRAMP, PCI DSS, and many more. Starting with the HITRUST certification and treating the assessments as one data collection process, rather than one-off assessments will save your organization a great deal of resources, time and budget.
HITRUST & SOC 2
SOC 2 reports describe the internal controls at a service organization, based on the American Institute of Certified Public Accountants (AICPA)’s Trust Service Criteria:
- Security (Common Criteria)
- Availability
- Processing Integrity
- Confidentiality
- Privacy
SOC 2 reports provide users with management assertions, a description of both the system and the controls, tests and the results of the tests, and the independent service auditor’s report. The SOC 2 is widely used by service organizations that provide services to other business entities.
HITRUST and the AICPA have developed a collaborative approach that aligns the AICPA’s Trust Services Criteria with the HITRUST CSF criteria. This allows licensed CPA firms, who are also CSF assessor firms to issue a SOC 2 plus HITRUST report that includes both the SOC 2 criteria and HITRUST CSF. This makes HITRUST and SOC 2 complimentary services through this converged reporting model.
HITRUST & PCI DSS
PCI DSS is a payment card industry standard used to protect payment card data. Founded by the five major card brands, Visa, MasterCard, American Express, Discover and JCB, PCI DSS defines controls to enhance credit and debit card security.
HITRUST used the PCI DSS methodology in the creation of the HITRUST healthcare standard. To correctly map the two frameworks, HITRUST received input from their board of directors, who are industry experts from major healthcare organizations, to tailor the framework to the industry’s needs. The tailoring of this framework resulted in numerous factor overlaps between the two certifications, making PCI DSS easily attainable once HITRUST CSF is achieved.
HITRUST & ISO 27001/ NIST 800-53
HITRUST recognizes the complex, global nature of the healthcare industry and the need for an industry-specific approach to information protection. Because of this, ISO/IEC 27001 and NIST SP 800-53 were chosen as the foundations upon which the HITRUST CSF was built upon due to both being an international standard for information security.
ISO 27001 differs from the HITRUST CSF, as ISO 27001 is not control-compliance based, but is instead a management/process model for the Information Management System that is assessed. One of the key differences between NIST 800-53 and the HITRUST CSF is that NIST 800-53 does not address the specific needs within the healthcare industry. While ISO 27001 and NIST 800-53 are both beneficial frameworks to demonstrate cybersecurity standards, they are not as comprehensive as HITRUST CSF. The HITRUST certification covers many more factors than ISO 27001 and NIST 800-53, making both certifications easily attainable under HITRUST CSF.
HITRUST & FedRAMP
The Federal Risk and Authorization Management Program (FedRAMP) serves to increase confidence in the security of cloud service providers (CSPs) utilized by the federal government.
FedRAMP certification is incredibly valuable for vendors working with the U.S. government. If you are working with the state level and not truly working with the federal government, you can easily map FedRAMP requirements to the HITRUST CSF framework. Organizations that are interested in pursuing FedRAMP certification could consider adding it to their HITRUST assessment to benchmark whether they are prepared and to mature their controls as needed but should note that adding FedRAMP to a HITRUST assessment is not the equivalent of achieving FedRAMP certification.
HITRUST & GDPR
The General Data Protection Regulation (GDPR) aims to enhance the protection of personal data of European Union (EU) residents. The GDPR not only impacts organizations within the EU, but also any organization that processes the personal data of EU residents. Failure to comply with the Articles outlined within the GDPR may not only present a reputational risk for organizations, but also the potential for the following enforcement actions:
- Restricted access to data
- EU Commission-directed data protection audits
- Fined 4% of annual worldwide revenue
HITRUST has mapped the EU’s GDPR into the HITRUST CSF comprehensive privacy controls. By doing this, HITRUST helps its customers identify and lessen gaps and risks in their existing programs, ultimately helping them grow their cybersecurity compliance.
HITRUST & CCPA
The California Consumer Privacy Act of 2018 (CCPA) allows consumers to have more control over the personal information that businesses oftentimes collect. California consumers now have the following privacy rights:
- The right to know what information is being collected and how it will be used
- The right to delete personal information collected (with a few exceptions)
- The right to opt-out of the sale of the personal information
- The right to non-discrimination for evoking these rights
The HITRUST certification includes comprehensive privacy controls and maps back to CCPA, similar to how the HISTRUT certification maps back to GDPR. The HITRUST certification will help organizations identify and mitigate gaps in their current compliance programs, allowing them to meet the growing regulatory requirements and customer expectations regarding their data usage.
Getting started
While there are a variety of different audit options for any organization, the HITRUST CSF provides scalable, prescriptive solutions for organizations of any type. By pulling from major pre-existing frameworks and working with organizations to better understand their needs, the HITRUST CSF provides a complete, certifiable security and privacy standard. Are you ready to get started? The best way to set yourself up for success when it comes to a HITRUST assessment is to make the time and resource investment upfront. After all, proper planning equals HITRUST success. Before diving in, review our expert list of do’s and don’ts when getting started with your HITRUST certification.
What is Zero Trust?
There is no one-size-fits-all solution for security so the best way to lessen the threat surface is to implement a zero trust architecture. To determine if pursuing a zero trust architecture is the right move for your organization, you need to understand its purpose, benefits and challenges.
Traditional attempts to protect the perimeter have shown that they are no match for today’s increasingly sophisticated threat actors. After all, humans are still the weakest link; it’s far too easy for someone to fall victim to a phishing attack, granting access to an internal network.
While zero trust has been an intimidating topic for many organizations due to the well-known challenges associated with implementing such an approach into an existing organization’s frequently complex network, the benefits shouldn’t be overlooked. Even the Federal Government is recognizing the importance of this approach as indicated in the recent Executive Order on Cybersecurity from President Biden which states, “The Federal government must lead the way and increase its adoption of security best practices, including by employing a zero-trust security model…”
To determine if pursuing a zero trust architecture is the right move for your organization, you need to understand its purpose, benefits and challenges.
What is Zero Trust?
Zero trust is a collection of concepts and ideas that are designed with the principle of least privilege for information systems. Basically, it’s about restricting access to resources to only the people who need them.
Every time a user wants to access specific data or a specific resource, the user will need to authenticate and prove who they are. For example, if a user needs to read the details from a document to do a portion of their job, they will only be granted privileges to read the document; they will not be able to edit or modify that document in any way.
This restriction around privileges is done intentionally. After all, a zero trust architecture uses zero trust principles to manage workflow and is designed to assume that an internal network is already infected with various threats. This is a unique mental hurdle for many organizations since most people just assume that an internal network is protected.
So how do you start implementing a zero trust architecture into your own network?
The Gold Standard of Zero Trust: NIST 800-207
Organizations looking to implement a zero trust architecture need to first identify the framework they want to follow. The NIST Special Publication 800-207 Zero Trust Architecture is widely referred to as the “gold standard” of zero trust. It is, perhaps, the most thorough framework an organization can follow to implement a true zero trust architecture.
According to NIST 800-207, “zero trust (ZT) is the term for “an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources.”
The transition to a zero trust architecture is a significant task that cannot be achieved by simply updating or implementing new network security solutions. For that reason, many organizations pursue zero trust architecture in phases, oftentimes having components of zero trust incorporated in the organization’s infrastructure paired with perimeter-based security solutions.
The Benefits of Zero Trust
The greatest benefit of a zero trust architecture is obviously security. But there are three distinct components within network security that are worth highlighting.
1. Lessening the Threat Surface
Implementing a zero trust architecture is similar to implementing a brick wall against a traditional attack. This approach requires constant authentication, measurement, and verification to ensure the users who are granted access are who they say they are, and that they don’t abuse the access they’ve been given.
2. Visibility and Accountability
If organizations follow proper guidance, they should have logging and monitoring in place to know when anomalies happen. Though this is not a unique element to zero trust, limiting user access and accurately logging and monitoring activities allows organizations to gain greater visibility into user activities.
3. Securing the Remote Workforce
Clearly, the rapid shift to a remote workforce was both unprecedented and unexpected. Also unexpected was the speed with which new security concerns arose as a result of the increased presence of a distributed workforce, where employees began accessing the organization’s internal network from wherever they chose to work.
Consider, for example, if a user’s laptop was infected and they connected to the organization’s internal network through the virtual private network (VPN). With a zero trust architecture, it wouldn’t be as easy for the infected machine to infect the network because even the internal network is not automatically treated as an implicitly trusted network.
Based on this short list, it may seem like a no-brainer to implement a zero trust architecture into your organization, but there are some challenges to consider.
The Challenges of Zero Trust
The challenges around implementing zero trust architecture largely revolve around user experience and expertise.
Productivity and Performance
When it comes to productivity and performance, a zero trust architecture can unintentionally impact a user’s ability to get their job done. It can be tricky to find the delicate balance between locking down your assets as tight as possible and making employees unproductive. After all, humans are the weakest link when it comes to network security. Limiting each user’s ability to interact with organizational data and information according to least privilege principles makes sense, until it prevents them from getting their job done in a timely and efficient manner.
Implementation Expertise
One of the biggest challenges organizations encounter with implementing a zero trust architecture is the amount of time and deep security knowledge required to implement it, especially for an already established organization.
A deep understanding of how an organization’s network operates and how the business runs is just the beginning. To effectively implement a zero trust architecture an organization must think ten steps ahead. For example, you’d need to think about the architecture in use today, how it can be modified while in use, and what long-term changes would need to take place.
Troubleshooting
Part of implementation planning is troubleshooting. Before a zero trust architecture is even implemented, the security team needs to consider all the possible scenarios that could require troubleshooting.
What if something stops working when zero trust is implemented? Who has enough functional knowledge of every component within an organization’s network to effectively troubleshoot something if or when something stops working?
Ultimately, this highly specialized skillset requires someone who is technically aware and geared toward managing and troubleshooting a zero trust environment.
What Zero Trust Steps Can you Take Today
Organizations have become increasingly complex making traditional network security solutions less effective on their own. This, coupled with the increasing sophistication of threat actors, illustrates a very real need to explore an approach that lessens the threat surface.
I strongly believe it’s time for organizations to start having zero trust conversations and think about what it would look like to begin the migration process.
To do so most effectively, leverage an existing methodology or framework, like NIST 800-207, as a blueprint for pursuing your zero trust mission. Create a checklist and a Q&A test plan to ensure you understand what the implementation could look like.
And remember, hacks happen from gaps that are often overlooked. Whatever framework you decide to pursue for your zero trust mission, follow it completely.