As more customers ask for demonstrated SOC 2 compliance, independent cybersecurity control validation and attestation are becoming necessary to compete for high-priority contracts. Beyond customer demand, SOC 2 reports ensure that controls are properly implemented and used within your organization, greatly reducing potential security threats.
For organizations seeking a SOC 2 report, there are two attestation options available: Type 1 and Type 2. What type is best for your organization to prove compliance? Our experienced assessors break down the options so the path to SOC 2 compliance is clear.
What is a SOC 2 report?
A SOC 2 report highlights the controls in place that protect and secure an organization’s system or services used by its customers. The scope of a SOC 2 examination extends beyond the systems that have a financial impact, reaching all systems and tools used in support of the organization’s system or services. The security of your environment is based on the requirements within a SOC 2 examination, known as the Trust Services Criteria (TSC):
- Common Criteria/Security (required)
- Availability (optional)
- Processing Integrity (optional)
- Confidentiality (optional)
- Privacy (optional)
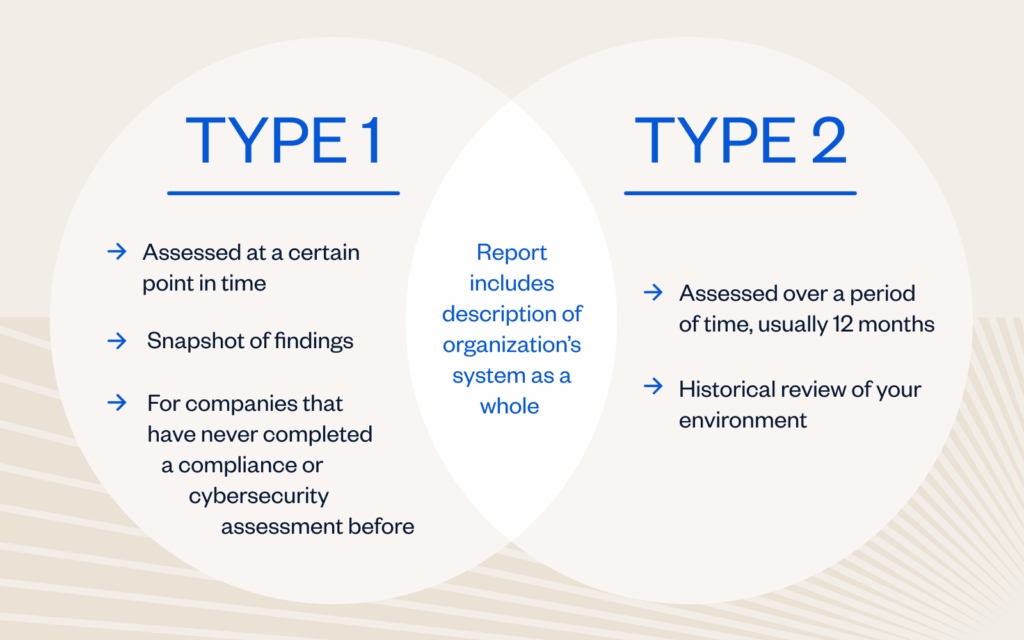
The difference between Type 1 and Type 2 reports
Which SOC 2 report should your organization choose? Read on to learn the difference.
SOC 2 Type 1 Report
Organizations that select a SOC 2 Type 1 report will evaluate the design and implementation of an organization’s system of internal controls as they relate to the in-scope TSCs. The report will include the management’s assertion, auditor’s opinion on the design and implementation of controls, a description of the in-scope system, and the controls that were independently tested by the auditor. This serves as a snapshot of an organization’s environment to determine if controls are suitably designed and in place.
SOC 2 Type 2 Report
SOC 2 Type 2 reports will evaluate the design, implementation and operating effectiveness of an organization’s system of internal control as they relate to the in-scope TSCs over a defined period of time, typically six to twelve months. The report will include the management’s assertion, auditor’s opinion on the design and operating effectiveness of controls, a description of the in-scope system, and the controls and test results that were independently tested by the auditor A SOC 2 Type 2 report provides a historical view of an organization’s environment to determine if the organization’s internal controls are designed and operating effectively.
What is a readiness assessment?
Now that you understand the difference between a Type 1 and Type 2 report, how can you best prepare for your SOC 2 examination? Consider these options from A-LIGN’s expert auditors:
- Traditional approach: A-LIGN will perform a formal Readiness Assessment that simulates a Type 1 or Type 2 audit and results in a report with recommendations from the auditor. This option is recommended for companies that don’t have many formal procedures or have never been through an audit before.
- Belay approach: This hybrid two-step approach has a smaller high-level gap assessment of key controls prior to the Type 1 SOC 2 examination. This approach saves time and costs and is designed for more mature organizations with formally established and implemented procedures who still have concerns or questions about their readiness for a SOC 2 audit.
Why A-LIGN?
A-LIGN is the leading provider of high-quality, efficient cybersecurity compliance programs. Combining experienced auditors and audit management technology, A-LIGN provides the widest breadth and depth of services including SOC 2, ISO 27001, HITRUST, FedRAMP, and PCI. A-LIGN is the number one issuer of SOC 2 and a leading HITRUST and FedRAMP assessor. The A-LIGN difference is:
- 17.5k+ SOC assessments completed
- #1 SOC 2 issuer in the world
- 200+ SOC auditors globally
Next steps
Ready to begin your compliance journey? Contact A-LIGN today to get started.





