Audit reports are a critical tool for ensuring compliance. They provide an independent assessment of a company’s compliance program and identify any areas where improvement is needed. Many people assume that all audit reports are created equal, but nothing could be further from the truth. Some budget auditors will sell businesses on a service that looks like what they need but, in reality, is a poor imitation of a high-quality report.
So, what’s on the line when a company chooses a cut-rate audit?
The risk of a cheap audit
Whether companies are looking for a compliance assessment for SOC 2, ISO 27001, SOX 404, or another standard, it’s important to carefully select an auditing partner, as the results can have a significant impact on business operations and reputation.
When a company doesn’t do its research before signing the audit contract, it opens itself up to many risks:
- Security vulnerabilities: A superficial audit may fail to uncover key weaknesses in an organization’s information security practices. This can leave the company exposed to data breaches, cyberattacks, and financial losses associated with costly remediation efforts.
- Inadequate assurance: Cheap audits may lack the thoroughness required to provide a meaningful level of assurance. This can leave the company and its stakeholders uncertain about the effectiveness of internal controls and security measures.
- Negative brand image: An inadequate audit that fails to identify control deficiencies or security issues can lead to a loss of trust among clients, partners, and other stakeholders, resulting in reputational damage that can be difficult to recover from.
- Missed operational inefficiencies: A low-quality audit may overlook inefficiencies in business processes, preventing the company from optimizing its operations and improving its bottom line.
- Legal liabilities: Incomplete audits can leave a company vulnerable to legal liabilities, especially if clients or business partners suffer financial losses due to control failures that the audit didn’t detect.
- Lost business opportunities: Many clients and partners require evidence of a high-quality compliance assessment (e.g., SOC 1 or SOC 2 reports) before engaging in business relationships. Choosing a cheap audit can mean more work down the line if it doesn’t cover all the controls that interested parties demand.
What to look for in a final audit report
A high-quality audit report for a compliance assessment like SOC 1 or SOC 2 is crucial for ensuring the accuracy and reliability of a company’s internal controls and security practices. Here are some important things a company should expect in such a report:
- Clarity and transparency: The audit report should provide a thorough overview of the audit process, scope, findings, and conclusions. It should be easily understandable to both technical and non-technical stakeholders.
- Comprehensive scope: The audit should cover all relevant aspects of the organization’s controls and security processes. It should be customized to the company’s specific needs and industry best practices. The report should include a detailed assessment of controls, policies, and procedures, evaluating their design and effectiveness in meeting the compliance criteria.
- Compliance with audit standards: The audit should be performed in accordance with recognized standards, such as the Statement on Standards for Attestation Engagements (SSAE) for SOC 1 or the Trust Services Criteria for SOC 2. The report should explicitly state compliance with these standards.
- Testing and sampling: The audit should involve extensive testing and sampling of controls and transactions (as applicable) to ensure that the findings are representative of the overall control environment. The report should include detailed documentation and evidence to support the auditor’s conclusions.
- Recommendations and remediation: In the case of control deficiencies, a good audit report will provide recommendations for remediation and improvement, helping the company address the identified issues effectively. The auditor should also provide the opportunity for companies to ask questions in the draft phase and include those clarifications in the final report.
Note: A high-quality audit report will come from a qualified and competent audit firm. Look for certifications, experience, and a reputation for excellence in the field.
Protect your business with robust audit reporting
Selecting the right compliance partner can have a significant impact on the success of an organization’s compliance program. Partnering with a budget audit firm may put your business at risk of receiving a low-quality audit report, which could be rejected—leading to hidden costs and delays in obtaining another report.
A-LIGN stands out by delivering a single-provider approach that takes companies from readiness to report on a full suite of compliance certifications and assessments, including SOC 1, SOC 2, FedRAMP, ISO, HITRUST, PCI, and many more. Our reports cover hundreds of internal controls, so businesses can be sure that if there’s a vulnerability, we’ll find it. Contrast that with budget audit firms, which assess 80% fewer controls than A-LIGN in some cases.
Don’t just “check the box” on compliance. Get a high-quality report from a trusted partner that can help you make meaningful, lasting changes in your internal controls. To learn more, download our quality audit checklist.
SOC 2 compliance requirements are a set of criteria that service organizations must meet in order to demonstrate their commitment to maintaining the highest level of security, availability, processing integrity, confidentiality, and privacy for their clients’ data. Developed by the American Institute of Certified Public Accountants (AICPA), the SOC 2 framework is a comprehensive auditing process that can be tailored to the unique needs of each organization while ensuring client data is stored in a secure manner. As more businesses migrate their operations to cloud-based platforms, understanding SOC 2 requirements is essential to ensuring that sensitive information remains protected regardless of environment.
What is a SOC 2 audit?
A SOC 2 audit is an examination performed by an independent CPA firm to assess the design and/or operating effectiveness of an organization’s controls. The purpose of this audit is not only to report on control effectiveness within an organization’s internal control environment, but also to provide assurance that these controls are effectively mitigating risks associated with the applicable trust service criteria. Conducting a thorough and well-documented SOC 2 audit can also serve as a valuable marketing tool, demonstrating credibility and trustworthiness to current and potential clients.
Achieving SOC 2 compliance requires adherence to all relevant aspects of the SOC 2 framework. This entails designing and implementing controls that address all of the selected five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy. These criteria are intended to provide coverage across key areas of risk while still allowing organizations flexibility in determining which specific controls they need based on their unique circumstances.
SOC 2 Trust Services Criteria
Organizations can use the SOC 2 trust services criteria as a roadmap for establishing robust systems for protecting sensitive information. Each criterion represents a distinct area where vulnerabilities may exist:
- Security: Organizations must have policies and procedures in place that protect against unauthorized access, both physical and logical.
- Availability: Businesses need reliable infrastructure designed for maximum uptime so customers can consistently access services when needed.
- Processing Integrity: Controls should ensure accurate processing of customer data without corruption or unauthorized alteration.
- Confidentiality: Organizations must implement measures to safeguard sensitive information from unauthorized disclosure and use.
- Privacy: Personal data must be protected, with controls in place that ensure compliance with privacy laws and regulations.
SOC 2 compliance requirements checklist
To streamline the process of achieving SOC 2 compliance, organizations can make use of a SOC 2 requirements checklist. This list presents an overview of all relevant criteria, broken down into manageable tasks or milestones. By using such a checklist, businesses can more easily identify gaps in their current practices and prioritize remediation efforts to address those vulnerabilities.
In addition to serving as a helpful organizational tool, compiling a SOC 2 requirements list is also valuable for demonstrating progress toward compliance goals. By maintaining thorough documentation of completed tasks and relevant evidence, organizations can provide auditors with clear evidence that they have taken meaningful steps to address security risks.
What are SOC 2 compliance requirements?
They are a series of standards designed by the AICPA to help service organizations establish robust and reliable internal controls that protect sensitive data in accordance with the trust services criteria. By adhering to these criteria, organizations can not only mitigate risks associated with poor data security but also demonstrate their commitment to customers and partners that they take this responsibility seriously.
Achieving SOC 2 compliance requires rigorous attention to detail and dedication from every level within an organization. Employees must be educated on proper data handling procedures; systems must be monitored closely for signs of potential breaches; infrastructure should be maintained to minimize downtime and maximize performance; and policies should reflect current best practices in data protection.
While achieving compliance may seem daunting at first glance, it is important for businesses operating in an increasingly interconnected world where trust is paramount. By diligently working through the SOC 2 requirements checklist and staying informed about evolving industry standards, organizations can build strong defenses against cyber threats while reinforcing their reputation as trusted stewards of customer data.
Navigating the world of SOC 2 requirements is an essential undertaking for modern service organizations looking to ensure the highest level of data security for their clients. By understanding the SOC 2 audit process, implementing controls based on the SOC 2 trust services criteria, and maintaining thorough documentation throughout the journey to compliance, businesses can demonstrate their commitment to safeguarding sensitive information and maintaining customer trust in an increasingly competitive marketplace.
Ready to start your SOC 2 journey? A-LIGN is ready to assist with any of your SOC 2 compliance, cybersecurity, and privacy needs. Contact us today.
If your organization handles customer data or stores sensitive information, you’ve likely heard of a SOC 2 report. These reports are a critical component in evaluating the security of an organization’s sensitive information. A SOC 2 report can provide assurance to customers, clients, and partners that organizations are taking the appropriate measures to protect their data.
As a result, SOC 2 has become increasingly important for companies seeking to maintain trust and credibility in the marketplace. In this article, we’ll provide an overview of SOC 2 reporting by covering its key aspects, including real-world examples and document templates to help further illustrate these concepts.
What is a SOC 2 report?
At its core, a SOC report (System and Organization Controls report) is a comprehensive attestation report conducted by third-party auditors that assesses an organization’s internal controls related to design and operational effectiveness. There are two main types of SOC reports: SOC 1 and SOC 2. While both serve essential functions in evaluating organizational controls, they differ significantly in scope and purpose.
A SOC 1 report specifically focuses on an organization’s internal controls that could impact a user entity’s financial reporting (ICFR), whereas a SOC 2 report addresses an organization’s information systems security, availability, processing integrity, confidentiality, and privacy controls. Both SOC 1 and SOC 2 reports can assess the design and operational effectiveness of controls over a defined period.
A SOC 2 report includes sections addressing:
- Control Environment
- Communication and Information
- Risk Assessment Policies
- Monitoring and Control Activities
- Logical and Physical Access Controls
- System Operations
- Change Management
- Risk Mitigation
Within the SOC 2 framework are two distinct subtypes – Type 1 and Type 2. A Type 1 report describes an organization’s control design at a specific point in time, whereas a Type 2 report evaluates the operating effectiveness of those controls over a designated review period.
Because SOC 2 audit reports are essential for organizations that want to demonstrate their commitment to security best practices, it is critical for businesses to understand specific sections within a report. For instance, within a typical SOC 2 Type 2 report are sections covering:
- The organization’s description of their system’s environment
- The Third Party Assessment Organization (3PAO)’s testing procedures and results
- Any identified exceptions in the organization’s controls design or effectiveness
- Management’s assertion of the fairness of description of the system and environment
Each section of the SOC 2 report plays a vital role in providing a comprehensive understanding of an organization’s compliance with established criteria.
Understanding the importance of SOC 2 reporting
As businesses face increasing scrutiny over their data-handling practices, it is also crucial to be well-versed in the reporting frameworks that govern these evaluations. The SOC 2 framework, for example, includes the Trust Services Criteria established by the American Institute of Certified Public Accountants (AICPA). This framework provides a rigorous set of guidelines that auditors follow when assessing an organization’s controls and processes.
Carrying out a SOC 2 audit can be a complex process involving several steps like scoping the engagement, selecting appropriate trust services criteria (TSC), engaging qualified independent auditors, gathering documentation of controls in place as well as testing control effectiveness over time.
The benefits of SOC 2 reporting templates
Given the complexities involved in protecting sensitive data from unauthorized access or disclosure, many organizations seek out resourceful tools such as downloadable examples (e.g., a SOC 2 report example PDF) or templates (e.g., a SOC 2 reporting template).
A SOC 2 reporting template typically includes detailed instructions to organize relevant information and guidance on creating a clear, concise report that effectively conveys an organization’s control environment to external auditors.
With so much at stake concerning sensitive data protection, organizations cannot afford to maintain an ineffective control environment if they wish to achieve regulatory compliance. As such, organizations should look to SOC 2 reporting templates for assistance in preparing for these critical evaluations.
Prioritizing SOC 2 to help your business
Ultimately, organizations that prioritize robust controls and comprehensive assessments like SOC 2 reports are better positioned to protect their sensitive data and maintain their sterling reputations in an increasingly scrutinized business environment.
SOC 2 reports play critical roles in:
- Evaluating an organization’s internal controls related to control design and operating effectiveness
- Showcasing their commitment to safeguarding client data
- Maintaining robust security controls that help prevent unauthorized access or misuse
- Establishing credibility within competitive markets
Businesses looking for assistance during the SOC 2 reporting process can lean on helpful tools such as SOC 2 report examples and templates. Utilizing these resources can ensure your organization is prepared for the audit process.
Because earning a SOC 2 report is such a crucial component to show commitment to cybersecurity compliance, it is important to work with an experienced audit firm to receive a high-quality report.
Ready to start your SOC 2 journey? A-LIGN is ready to assist with any of your SOC 2 compliance, cybersecurity, and privacy needs. Contact us today.
On October 25, 2022, ISO/IEC 27001 (commonly called ISO 27001) was updated for the first time since 2013. Many organizations still haven’t modified their information security management system (ISMS) to conform to the new standard. Where does your business stand?
In this post, we’ll walk through the changes companies need to make and the associated deadlines so you can determine the right next step for your organization.
ISO 27001:2022 vs. ISO 27001:2013
First, let’s review the nine biggest changes in ISO 27001:2022:
- Updated Context and Scope: ISO 27001:2022 places increased emphasis on an organization’s internal and external context, including stakeholders and processes that impact the ISMS.
- Statement of Applicability (SoA): Organizations should revise their Statement of Applicability (SoA) to incorporate a mapping of the new 2022 controls (the actual SoA requirements are essentially the same).
- Controlled Changes to the ISMS: Clause 6.3 emphasizes the management of controlled changes in a structured and systematic way within the ISMS, ensuring changes do not compromise information security.
- Enhanced Operational Planning and Control: Clause 8.1 requires organizations to establish criteria for actions outlined in Clause 6 and systematically manage these actions. This clause underscores the importance of a structured approach to overseeing operational processes, including those involving third-party relationships.
- Reorganization and Reduction of Annex Controls: The new standard condenses annex controls from 114 to 93 to align more effectively with the evolving hybrid and remote work environments, acknowledging the need for a more focused and adaptable approach to information security controls.
- Introduction of New Controls: 11 new controls in the annex section formally address emerging threats and challenges, including threat intelligence, information security for the use of cloud services, ICT readiness for business continuity, and more.
- Recategorization of Controls: Controls have been restructured into four primary categories — organizational, people, physical, and technological — to improve clarity and simplify the structure.
- Emphasis on Needs and Expectations of Interested Parties: Clause 9.3 calls for management review to account for changes in the needs and expectations of stakeholders, underscoring the importance of aligning the ISMS with evolving stakeholder priorities and requirements.
- New Controls for Current Challenges: New controls aim to keep the standard current and relevant, covering areas such as threat intelligence, web filtering, and secure coding.
See a detailed breakdown of the changes.
ISO 27001 transition timeline
Organizations have until October 31, 2025 to transition to ISO/IEC 27001:2022, but that doesn’t mean you should put it off. Here’s a quick summary of the transition timeline:
- October 31, 2022: The transition period began.
- May 1, 2024: All new (first-time) ISO 27001 certifications should be on the 2022 version.
- July 31, 2025: All transition audits (for recertification and surveillance audits) should be completed.
- October 31, 2025: The transition period ends. All ISO 27001:2013 certifications will expire at this time.
Determine your organization’s next steps
Wondering what your business needs to do next to be ready for the 2025 transition deadline? Consider what steps have been taken so far and proceed accordingly.
For example, if your organization has yet to take any action, the first step is to make a plan. Consider how much time your team needs to perform all the necessary actions described in the following section. Work with your audit partner to make a unique plan that works with where you are in the ISO cycle.
One important factor to consider is budget — what resources will your team require to complete all necessary tasks by the October 31, 2025 deadline? Make sure you build anticipated costs into upcoming budgets so that company leadership and the specific teams involved can anticipate them.
If you’re ready to transition but not sure where to start, the rest of this article will give you a better idea of what you need to do next. As you begin the transition process, lean on your audit partner to ensure a seamless transition before the deadline.
How to update Your ISO 27001 Certification to the 2022 standard
If your organization is currently certified against the 2013 version of ISO 27001, there are several steps that must be taken in order to achieve certification under the new version.
Purchase the ISO/IEC 27001:2022 standard
Every organization that seeks certification must purchase the official published ISO 27001 standard from the ISO. ISO products come with a single-user license, so documents cannot be shared between organizations (or provided by auditors).
Perform a gap assessment
There are 11 brand-new controls in ISO 27001:2022, so organizations should expect to find gaps in their ISMS under the 2013 version of the standard. A gap assessment will help you map your existing security controls to the 2022 version and identify what changes are necessary. Based on the level of compliance expertise your organization has, this gap assessment can be performed internally or with the help of a third party.
Implement new security controls
Once the gap assessment is complete, your team should focus on implementing new controls or modifying current controls as needed based on what gaps were identified. Make sure you give your organization enough time to plan for these changes and implement them effectively before scheduling your transition audit.
Update the statement of applicability
The statement of applicability (SoA) is a required document for ISO 27001 certification. The SoA states which Annex A controls your business has applied in order to reduce information security risk. Because of the changes between the 2013 and 2022 versions of the standard, your SoA will need to be updated to consider the newly added and reorganized annex controls.
Revise the risk treatment plan
Now that you have identified the relevant risks to your organization (via the gap assessment), your formal ISO 27001 risk treatment plan should be revised accordingly. This document should detail what steps your organization has taken to address each of the information security risks that have been detected.
Schedule your transition audit
Remember, all ISO 27001:2022 transition audits should be completed by July 31, 2025 to ensure that all certification decision can be made prior to the October 31, 2025 deadline. Ideally, you should schedule your transition audit before July 2025 to account for any unforeseen challenges and avoid unnecessary pressure on employees.
ISO 27001 transition FAQs
What is the most challenging aspect of the transition?
It will vary from company to company depending on the controls already in place. With that said, the reorganization of controls in the new version of the standard necessitates changes to documentation, which will require time and effort to overhaul.
Can my organization complete the transition audit during a surveillance year?
Yes, if your organization is due for a surveillance audit (rather than a full recertification audit), the transition audit can be added on. Keep in mind that this will expand the scope of the surveillance audit, so talk with your audit partner to determine the necessary time and resources required.
Is ISO 27001:2013 still globally recognized during the transition period?
Yes, if your company has an active ISO 27001:2013 certification, it will still be considered active until its expiration date or the end of the transition period (whichever comes first). As an added measure, your organization might consider adding the new 2022 controls to your statement of applicability. That way, if any stakeholders question you regarding the transition, you can easily demonstrate your organization’s readiness and the progress you are making toward certification under the 2022 standard.
Get started on your ISO 27001 transition today
At A-LIGN, we are committed to helping our clients maintain the highest standards in information security. Our team is actively issuing the 2022 version of ISO 27001, and our experts are ready to guide your organization through the process.
Don’t wait until the last minute. Reach out to A-LIGN today to make a transition plan before the 2025 deadline arrives.
Get started by downloading our ISO 27001 checklist.
The SOC 2 framework is an essential and rigorous evaluation process for organizations that provide third-party services to others. It is designed to ensure the highest level of trust and transparency when it comes to the security, availability, processing integrity, confidentiality, and privacy of the systems, applications, and data belonging to their customers and users. The framework was introduced by the American Institute of Certified Public Accountants (AICPA) as part of their System and Organization Control reporting platform.
One of the goals in following the SOC 2 framework is to achieve SOC 2 compliance. Achieving compliance means that a service organization has met all necessary criteria pertaining to one or more of the five Trust Services Criteria (TSC): Security, Availability, Processing Integrity, Confidentiality, and Privacy. Ensuring SOC 2 compliance is vital for organizations that handle sensitive customer data in industries such as finance, cloud computing, healthcare, or technology services since these businesses are obligated to demonstrate they have specific safeguards in place.
To determine if a company meets all requirements for SOC 2, a thorough analysis is performed via a SOC 2 audit. A SOC 2 audit must be conducted by an independent certified public accountant or auditing firm with knowledge and expertise in this field. The primary goal of this audit is to evaluate an organization’s internal controls for managing and protecting customer data. This includes assessing policies and procedures related to access control, physical security measures, data backups and recovery processes, system monitoring tools, encryption technologies used for protecting confidential information, personnel training programs on security awareness and many other additional factors depending on the scope of TSCs being evaluated.
SOC 2 framework Trust Services Criteria
Understanding SOC 2 requirements is an essential first step of achieving compliance. These requirements are based on five Trust Services Criteria created by the AICPA:
1. Security: This criterion evaluates whether an organization’s systems and applications are protected against unauthorized access (both physical and logical) and other vulnerabilities, ensuring protection and integrity of client data and information.
2. Availability: This criterion verifies that services provided by an organization are available for operation according to agreed-upon terms, ensuring reliability and sustainability.
3. Processing Integrity: This criterion assesses the accuracy, timeliness, and completeness of system processing as well as the authorization of transactions to ensure data is processed as intended.
4. Confidentiality: This criterion ensures that sensitive customer information is properly stored, classified, protected, and accessed only by authorized personnel to maintain confidentiality.
5. Privacy: This criterion involves the collection, storage, retention, disclosure, disposal of personal information in adherence with privacy policies and any applicable laws or regulations.
Why SOC 2 matters
To have a more comprehensive grasp on SOC 2 definition, it is essential to understand its purpose and significance for organizations providing services to users and customers. The framework offers a standardized way for such organizations to demonstrate their commitment towards maintaining robust security controls over confidential user and customer data. It helps instill trust among clients who rely on these service providers for critical business operations while also promoting an ongoing culture of compliance within the organization itself.
One useful tool for entities embarking on their journey towards SOC 2 compliance is the SOC 2 questionnaire. A questionnaire serves as a valuable resource for self-assessment and an opportunity to communicate with auditors about specific controls in place at the organization. The questionnaire typically consists of detailed questions related to each TSC and assists with providing relevant examples evidence supporting those answers. This document aids in streamlining the audit process and identifying potential gaps in controls or areas requiring improvement.
In conclusion, adopting the SOC 2 framework signifies an organization’s commitment to maintaining robust security measures surrounding customer data. By understanding all aspects related to SOC 2 compliance – from audit processes through requirements based on Trust Services Criteria – businesses can effectively navigate their path towards achieving this critical attestation. Utilizing tools like questionnaires can also help ease some complexities associated with audits and provide valuable insight into an organization’s readiness for obtaining compliance status.
As industries continuously evolve and place increasing importance on protecting sensitive customer information against various threats – both internal and external – adhering to stringent compliance frameworks like SOC 2 becomes an essential business practice for service providers. In the end, it not only helps strengthen customer trust but also ensures long-term success in competitive markets.
How to get started
A great first step is to assess your readiness with our SOC 2 checklist. A-LIGN offers a variety of services, including SOC 2 automation through the use of our A-SCEND platform. Contact A-LIGN today to start the conversation about how we can streamline your compliance journey.
Compliance 101 for Growth-Stage Startups
In the early days of a business, owners have a lot to worry about: whether their product or service is a good fit for the market, whether they can effectively reach their target audience, what pricing strategy will help them grow. Needless to say, cybersecurity compliance may be the last thing on their minds, no matter how important it might be.
With so many other important problems to solve, startup founders might wonder whether compliance is an issue they can put off until a later stage of the company. While this mindset is tempting, there are several reasons founders should consider getting started with compliance early on.
The importance of laying a security foundation
If you have any hopes of scaling an enterprise that remains successful for years to come, it’s unquestionable that security policies and procedures will be necessary. Even if your business isn’t in a highly regulated industry that requires compliance with specific regulations, someone will likely want to see proof of security down the line (see the next two sections of this post).
Like with any other process, it’s much easier to establish a solid foundation for security compliance when your business is small rather than when it has grown large and complex. Suddenly introducing security requirements at a later stage can lead to confusion and frustration among employees. Plus, a lackadaisical approach to security puts your business at risk for breaches in those intervening years, which can make or break a young company.
Starting early with compliance means that new hires are automatically trained on good security practices, and you can easily layer in more sophisticated procedures over time as your needs and goals change. Specifically, undergoing a compliance audit like SOC 2 can identify gaps in your strategy that you likely wouldn’t uncover otherwise.
Showing investors you’re serious about compliance
Okay, we know you skimmed that last section to get to the important stuff: investment. The reality these days is that investors care about compliance. Many investors see a lack of security strategy as a major risk, and they may decline to invest in your business if it proves inadequate. In fact, our 2023 Compliance Benchmark Report found that 29% of organizations have lost a new business deal because they were missing a compliance certification.
Going through compliance audits early on can show investors that you take security seriously. Plus, an audit report can make it much easier for your team to answer questions about security during the investor’s due diligence process.

Setting yourself apart from the competition
More than ever, consumers care and are knowledgeable about cybersecurity, especially when it comes to their personal data. When choosing between similar SaaS products, buyers may choose the business that clearly demonstrates a commitment to cybersecurity compliance.
In a survey conducted by McKinsey, 85% of respondents said that knowing a company’s data privacy policies is important before making a purchase. Even more significant, many people surveyed said they consider switching brands when a company’s data practices are unclear, and a majority said they look specifically for companies that have a reputation for protecting data.
As you look to increase revenue over the early years of your business, committing to cybersecurity and communicating your policies to the market can help you build trust with customers and gain an edge over organizations whose security strategies are less mature.
Compliance challenges for startups
Technology industry analysis from A-LIGN’s 2023 Compliance Benchmark Report
There’s no doubt that compliance can be time-consuming, expensive, and difficult to manage. The technology industry in particular, which many startups are in, conducts more audits per year and uses more auditors than average.
Here are a few of the top issues startups face in the compliance process:
- Limited staff resources: This is the greatest challenge for most organizations, especially early on. Managing compliance risk takes time, and few startups have any to spare, let alone dedicated staff members for compliance.
- Multiple audits: Especially in the technology space, it is common for organizations to conduct multiple compliance audits a year, which stretches resources even thinner.
- Manual collection of data: Without any automated systems in place to help with compliance, teams have to manually pull together information needed for audits. That takes — you guessed it — even more time.
How a strategic compliance approach can help
The solution for minimizing compliance challenges comes down to one thing: planning. That’s where the idea of strategic compliance comes in. Strategic compliance takes a proactive approach to audits and assessments by consolidating audits and auditors into a single annual event.
Why audit consolidation?
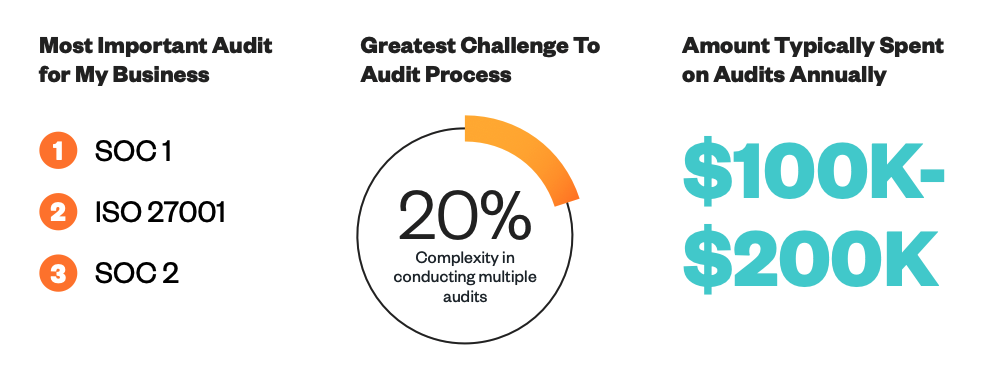
Our 2023 Compliance Benchmark Report found that one of the greatest compliance process challenges organizations face is the complexity involved in conducting multiple audits throughout the year. Duplicating efforts across various audits and providers, rather than getting multiple evaluations accomplished all at once, is the biggest downside to traditional compliance.
Consider, for example, that if you complete a SOC 2 certification, you will have met 100% of evidence requirements for SOC 1 and 90% for HIPAA. So, why go through separate audits at different times when you could have covered nearly all the requirements for three compliance processes in the same audit? With a strategic approach and the right partner, you can gather all the necessary evidence and use it for multiple certifications.
The value of selecting the right audit partner
Choosing a quality auditor is important for any compliance-focused organization, but the stakes are higher for startups. With limited resources and a lot to prove, a poorly conducted audit can be disastrous. Startups need to allocate their precious time and money to partners that can help them level up.
Here are a few things to look for when choosing a compliance vendor:
- The ability to produce actual reports and certifications. Some companies only offer software, which can help get you ready for an audit but is no replacement for the real thing. These companies farm out your actual audit to third parties. The audit they offer might be cheap, but you know what they say: You get what you pay for. Our research found that 32% of organizations have rejected a security report due to the reputation or quality of the auditor.
- A full suite of compliance services. As your startup scales, you may need to complete more audits and certifications. So, it will pay dividends down the road if you go with a vendor who can help you with many different compliance processes. Select and build a relationship with a compliance partner with your business’s future in mind.
- Experience and credibility. Your compliance vendor should have a proven track record of success and longstanding relationships with standards organizations like ISO, HITRUST, and the AICPA.
A-LIGN: A trusted cybersecurity and compliance partner for startups
A-LIGN is a technology-enabled cybersecurity and compliance partner trusted by more than 5,700 global organizations to mitigate cybersecurity risks. Our audit management platform, A-SCEND, combined with our audit experts offers startups and growing businesses a single-provider solution for their evolving compliance needs.
Ready to get started on your compliance journey with expert guidance? Reach out to A-LIGN today.
In the realm of cybersecurity assurance, the stakes have never been higher. The sophistication of cyber threats is increasing, which can cause significant financial and reputational damage. To combat these threats, organizations must ensure that their cybersecurity measures are robust, effective, and compliant with relevant third-party and regulatory standards.
Traditionally, many organizations utilize self-assessments to attest to their cybersecurity compliance. However, recent events such as the Penn State University case, have cast a shadow of doubt over the reliability and credibility of these self-assessments.
While self-assessments can be the initial introduction to a compliance journey, we believe in the value of third-party assessments for cybersecurity assurance. Keep reading to learn why third-party evaluations are not just preferable, but essential.
The Limitations for Self-Assessments
Objective Scrutiny
Self-assessments, by their very nature, lack external validation. Even with the best intentions in mind, an organization may unintentionally overlook their own vulnerabilities or be biased in its evaluation. After all, it’s like grading your own homework – people are more likely to give themselves the benefit of the doubt or be less harsh when reviewing their own work. A third-party assessment brings an objective lens to the compliance process, ensuring that evaluations are free from internal biases. With the help of an external partner, organizations can be confident that no stone is left unturned.
Expertise and Specialization
Many third-party assessors specialize in cybersecurity evaluations and keep up to date with the latest threats, vulnerabilities, and best practices. Working with a trained and experienced team ensures a thorough and comprehensive assessment based on current standards. Internal teams are often juggling many responsibilities and may lack the know-how of an audit team that is steeped in compliance trends on a daily basis. When it comes to something as serious as cybersecurity, it is worth it to bring in best-in-class experts.
Credibility and Trust
In the eyes of stakeholders, including clients, partners, and regulators, a third-party assessment carries more weight than any you could complete internally. It signals that the organization is serious about its cybersecurity posture and is willing to have its defenses scrutinized and improved with feedback from external experts. A third-party assessment can help organizations build trust and credibility with their customers, backed by an unbiased audit team.
Legal and Regulatory Defensibility
Should a security breach occur; a recent third-party assessment can provide a strong defense in legal and regulatory scenarios. A quality assessment, performed by a trusted audit partner, demonstrates due diligence and a proactive approach to cybersecurity. Of course, the goal of any cybersecurity program should be to prevent breaches in the first place, but even the most prepared organizations still find themselves in difficult situations. With the backing of a third-party evaluation, organizations may be able to mitigate penalties associated with a security breach and minimize reputational damage.
Continuous Improvement
Cybersecurity compliance should not be based on a single moment in time. Instead, organizations should seek out real-time validation and an always-on compliance program enabled by technology. Third-party assessors can help you move from reactive to proactive and can provide feedback and recommendations based on the latest industry standards. Technology-enabled assessors in particular can help you assess current state with compliance software and give you customized feedback from professional auditors on how to improve. This feedback can help organizations keep compliance top-of-mind throughout the year and continuously improve their cybersecurity posture.
The Role of Quality in a Third-Party Assessment
It is clear that a self-assessment is inferior to one conducted by a third-party, but it is important to keep in mind that not all third-party audits are created equal. Once you’ve decided to go down the path of engaging an outside party for an audit, there are important factors to consider when choosing an assessor.
One of the main criteria to look for in an auditor is the quality of their report. There are many low-cost, low-quality audits on the market today, but you get what you pay for. Budget auditors often cut corners when it comes to the number of controls tested, which can leave your team open to vulnerabilities. In some cases, your internal team may even be looking at more controls than a low-cost external partner.
The area where you’ll see the biggest difference in quality is the final report. Best-in-class assessments are often upwards of 100 pages and provide a comprehensive overview of an organization’s security posture. This document is a physical manifestation of security, demonstrating compliance to all key stakeholders.
The Importance of Third-Party Evaluations for Cybersecurity
For CIOs and CISOs, the message is clear: while self-assessments can serve as periodic internal checkpoints, they cannot replace the depth, expertise, and objectivity that quality third-party evaluations offer. By opting for external assessments with a trusted compliance partner, CIOs and CISOs not only bolster their organization’s defenses but also build trust with stakeholders, ensure regulatory compliance, and position their organizations as leaders in cybersecurity best practices. In our current cyber landscape, third-party assessments from trusted assessors are not just best practice; they are a necessity.
Get Started with a Third-Party Assessment
If you’re ready to take the next step from self-assessments to a trusted, third-party evaluation, contact A-LIGN. Our team of experienced auditors will help you every step of the way to ensure you have the right protections in place to secure your organization against cyber threats
Enron, WorldCom, Tyco… even two decades after their respective scandals, these names are still synonymous with corporate fraud. Congress passed the Sarbanes-Oxley Act of 2002, commonly referred to as SOX 404, in response to these egregious examples of corporate greed and misconduct. The law holds U.S. companies responsible for their financial record-keeping and reporting practices, and it stipulates criminal penalties for misconduct related to the manipulation, destruction, or alteration of financial records.
As a U.S. company, especially a publicly traded one, it’s vital to know what parts of SOX apply to your business and how to ensure compliance. Section 404 of the act (SOX 404) deals specifically with the internal controls and procedures that companies must implement in their financial reporting process. Keep reading to learn more.
What Is SOX 404? A Summary
SOX Section 404 (“Management Assessment of Internal Controls”) is commonly considered one of the most resource-intensive sections of the act to which companies must adhere. There are two subsections:
SOX 404(a) requires that companies implement and maintain effective internal controls. Companies document compliance with an “internal control report” with each of their annual reports mandated by the Securities Exchange Act of 1934, such as Form 10-K. This report, provided by company management, should describe and assess the effectiveness of the company’s internal control over financial reporting (ICFR).
SOX 404(b) requires that an independent auditor attest to and report on the assessment of internal controls provided by company management.
The Importance of SOX 404
While complying with SOX 404 can be a headache for executives, it serves an important purpose. Beyond shielding investors from risk, SOX 404 also safeguards a company’s reputation and longevity by annually assessing the design of their control environment and ensuring the controls are operating effectively with no gaps that would lead to a risk of incorrect financial statements.
Who Must Comply with SOX 404?
The Sarbanes-Oxley Act applies to all publicly traded companies in the U.S. (including wholly owned subsidiaries and publicly traded foreign companies that do business in the U.S.) with some important distinctions between SOX 404(a) and SOX 404(b). The Dodd-Frank Wall Street Reform and Consumer Protection Act codified an exemption to SOX 404(b) for non-accelerated filers, as defined by the Securities and Exchange Commission (SEC). In other words, companies that do not rise to the level of accelerated or large accelerated filers according to the SEC are not required to enlist an independent auditor for SOX testing and will only fall under the requirements of SOX 404(a).
The SEC updated its definitions of accelerated filer and large accelerated filer in March 2020, which led to a greater number of companies becoming exempt from SOX 404(b). Combined with previous SEC updates to its definition of smaller reporting companies (SRCs) in June 2018, companies meeting any of the following criteria are exempt from SOX 404(b):
SRCs (i.e., companies with less than $250 million in public float or less than $100 million in annual revenues with less than $700 million in public float) that reported less than $100 million in annual revenues in the most recent fiscal year
Emerging growth companies (EGCs) for the first five years following their initial public offerings, as long as they do not exceed annual gross revenues of $1.235 billion, have not issued more than $1 billion in non-convertible debt in the past three years, and do not become large accelerated filers
Newly acquired businesses in the first year following acquisition
Do Private Companies Need SOX 404 Testing?
While private companies and nonprofits are not required by law to perform SOX 404 audits, there are situations in which third parties may encourage them to perform various internal control audits (SOC/ISO) to ensure all systems and processes used in financial reporting are reviewed.
How SOX 404 Compliance Testing Works
The complete SOX testing process involves several rounds of internal testing throughout the year followed by an annual independent audit as required by SOX 404(b). If you are preparing for your first official SOX audit, consider working with compliance experts who can help you set processes up the right way and avoid headaches down the road.
That said, no matter how mature your company is or how robust your internal controls are, some deficiencies might be uncovered during SOX 404 testing. Often, auditors point to incomplete design or documentation of controls as the cause of weaknesses. Luckily, hiring an experienced compliance auditor gives you access to expert advice that helps you decide what parts of your processes require additional steps, signoffs, or documentation to ensure the effectiveness of internal control design and operations.
Combining SOX 404 Testing with Other Compliance Requirements
When it comes time for your yearly SOX audit, an external third party can provide subject matter expertise ensuring robust coverage of the control environment. As you research auditors, take into account any other compliance testing your company requires. Look for a SOX auditing firm that can help you with other compliance and cybersecurity certifications like SOC 1 or SOC 2.
Considering the strain that compliance testing can put on internal resources in terms of manpower and finances, it’s in your business’s best interest to avoid going through multiple rounds of auditing with different testing providers. Using an auditor who can identify the overlap of internal controls, processes, and evidence requests to satisfy multiple compliance efforts reduces the burden on your employees. Simply put, your team can get back to doing their jobs instead of tracking down documentation and information for auditors.
SOX 404 Compliance: Simplified
In summary, the Sarbanes-Oxley Act of 2002 was passed in response to major corporate scandals of the early 2000s. SOX 404 applies to most U.S. publicly traded companies and requires a yearly audit of internal controls and processes related to financial reporting. With A-LIGN, you get comprehensive control framework coverage and testing that will provide management and investors comfort that internal controls over financial reporting are designed and operating effectively. With the right controls in place, you don’t have to dread your annual SOX audit.
Reach out to A-LIGN’s SOX 404 experts today to learn how our decades of experience, comprehensive offerings, and flexible scheduling can help you avoid the fiscal year-end time crunch.
What Is a SOC 1 Audit?
If your organization handles, processes, stores, or transmits financial information, or information that can impact the financial statements of your customers, then it’s the ideal candidate for a SOC 1 audit. As an evaluation of the internal controls your organization has in place, a SOC 1 audit reviews how your organization protects client data. To go through an examination and receive a SOC 1 report, an organization must demonstrate that it is committed to and capable of delivering secure services.
What is a SOC 1 report?
A SOC 1 audit typically covers a period of six to 12 months. Following completion of the audit testing, a CPA firm will issue a report to review the findings and implement new measures if needed. It is considered an “attestation” report whereby management asserts certain controls are in place to meet the objective of the report. The firm’s auditors will provide an opinion on whether it agrees with management’s assertion.
An organization may be required to obtain a SOC 1 report by clients or stakeholders. The opinion stated by the firm in the report is valid for twelve months following the date of issuance. A bridge letter, or gap letter, is a document that states there have been no material changes or significant events within an organization’s control environment between SOC reports. The letter is issued by the organization and typically covers a period of three months or less.
Who should get a SOC 1 audit?
Enterprises that handle sensitive financial data, especially those whose actions affect financial reporting, should conduct SOC 1 audits to demonstrate to clients and partners that their information is in good hands. These include:
- Payment processors: These companies are contracted to distribute the payroll for employees at other organizations, and as such, must be trusted to perform this high-value responsibility.
- Collections organizations: These firms collect debts on behalf of another organization, and, in turn, directly impact financial reporting.
- Benefits administrators: These administrators manage, direct, and plan group benefits programs such as health, dental, vision, workers comp, 401(k), retirement and other plans.
- SaaS MSPs: Software-as-a-Service MSPs that process financial statements have a direct impact on financial reporting.
What are the benefits of SOC 1?
Even if it’s not required by a customer or investor, there are still benefits to pursuing a SOC 1 audit. The following benefits demonstrate the value of a SOC 1 audit:
- Ensure protection of your customers’ and partners’ financial information
- Demonstrate a commitment to corporate governance
- Provide assurance to customers and partners that your systems are secure
What is the difference between a SOC 1 Type 1 and Type 2?
There are two types of SOC 1 audits that an organization can conduct – Type 1 and Type 2. So, what’s the difference?
A SOC 1 Type 1 audit assesses an organization’s internal controls at a specific point in time. The report acts as a snapshot of your environment to determine and demonstrate if the controls are suitably designed and in place.
A SOC 1 Type 2 audit assesses an organization’s internal controls over time, typically a twelve-month review period. It serves as a historical review of an environment to determine and demonstrate if the controls are suitably designed and in place, as well as operating effectively over time.
How does a SOC 1 report differ from a SOC 2 report?
You might have heard of a SOC 2 report and are now wondering how it differs from a SOC 1 report. While similar, there are a few key differences you should be aware of when deciding whether to pursue SOC 1 or SOC 2.
SOC 1 is ideal for organizations whose data processing or storage can impact the financial reporting of their customers, and SOC 2 reports are relevant for a broader group of organizations because they focus on information and IT security. These may include data centers, IT managed services, SaaS vendors, and other technology and cloud computing businesses. SOC 2 audits are structured across five categories called Trust Services Criteria and are relevant to organizations who process data that does not directly affect the financial statements of end users:
- Security (required): Security controls protect information throughout its lifecycle. Organizations establish security controls to protect against unauthorized access, unauthorized disclosure, or damage to systems. Controls include a range of risk-mitigating solutions including endpoint protection and network monitoring tools to prevent or detect unauthorized activity.
- Availability (optional): Availability controls keep systems operational and available at a level that meets stated business objectives.
- Processing Integrity (optional): Processing Integrity controls ensure systems operate predictably and without accidental or unexplained errors.
- Confidentiality (optional): Confidentiality controls protect sensitive information throughout its lifecycle from collection to disposal.
- Privacy (optional): Privacy controls are specific to protecting personal information, especially information captured from customers.
How can I prepare for an audit?
Proactively preparing for a SOC 1 audit can save you time and better position your organization for a successful and efficient evaluation.
Define the scope: To ensure that your audit proceeds on schedule and within budget, define the scope. Will the assessment engage the entire organization, or will it be limited to specific departments? Determining this before the evaluation begins is critical.
Take inventory of assets: Compile a comprehensive list of the information systems in use including servers, routers, firewalls, load balancers, and applications so that you and your auditors can better envision the scope of the assessment.
Conduct a readiness assessment: An efficient audit requires a readiness assessment to identify what’s missing from an effective and complete internal controls environment. Remediating deficiencies before the audit begins is another critical effort.
Determine control objectives: There is flexibility allowed when compiling SOC 1 reports such that the reports of a company working with a CPA firm might differ from a similar company working with another firm. Prior to commencing the audit, determine internally and with your auditing partner which control objectives are to be included in your report.
Perform continuous monitoring: Following the completion of your audit, it’s essential to continue monitoring and assessing your control environment for maximum effectiveness, and then make improvements when necessary.
How A-LIGN can help
With thousands of SOC 1 assessments completed and more than 20 years of experience, A-LIGN is a leader in helping organizations protect the financial information of their customers and business partners. Click here to start your SOC 1 compliance journey.