What is SOC 2? Complete Guide to SOC 2 Reports and Compliance

In today’s security landscape, it’s crucial you assure your customer and partners that you are protecting their valuable data. SOC 2 compliance is the most popular form of a cybersecurity audit, used by a growing number of organizations to prove they take cybersecurity seriously. A SOC 2 report will provide you with a competitive advantage in the marketplace while allowing you to close deals faster and win new business.
Below we provide everything you need to know about a SOC 2 audit and final report. Let’s jump in!
What is SOC 2?
A Service Organization Controls (SOC) 2 audit examines your organization’s controls in place that protect and secure its system or services used by customers or partners. The security posture of your organization is assessed based on the requirements within the SOC 2 framework, known as the Trust Services Criteria (TSC).
What is the AICPA and why does it matter in SOC 2?
The American Institute of Certified Public Accountants (AICPA) organization is the governing body of the SOC framework and set the U.S. auditing standards that auditors use for SOC 2 examinations. When you complete the SOC 2 attestation and receive your final report, your organization can download and display the logo issued by the AICPA.
Why is SOC 2 compliance important?
It’s important for customers and partners to know that your organization will protect their data and the best way to demonstrate this is through an independent, reliable source. In today’s landscape, a SOC 2 is considered a cost of doing business because it establishes trust, drives revenue and unlocks new business opportunities.
Bonus- Oftentimes, a SOC 2 report is an acceptable alternative to the time-consuming, 500-question security survey!
What are the key benefits of SOC 2 compliance?
Organizations who complete a SOC 2 assessment will benefit from the following:
- Valuable insight into your security posture
- A strategic roadmap for cybersecurity investments and initiatives
- Increased competitive positioning in the marketplace
How can a SOC 2 report help small businesses scale?
Your startup or small business will need a SOC 2 report to go upmarket and close large deals. Below are some of the benefits you will notice after earning a SOC 2 report.
- Development of strong policies and procedures
- Increased credibility with investors and partners
- A strong competitive advantage
- Saved time, money and resources on a potential data breach
Who uses a SOC 2?
Service organizations that process, store, or transmit data for their clients or partners. While SOC 2 applies to almost any organization, it’s particularly important to data centers, software-as-a-service (SaaS) companies, and managed service providers (MSPs).
Who can perform a SOC audit?
All SOC 2 audits must be completed by an external auditor from a licensed CPA firm. If you plan to use a software solution to prepare for an audit, it’s helpful to work with a firm who can provide both the readiness software, perform the audit and produce a reputable SOC 2 report.
What are the SOC 2 Trust Service Criteria?
The security posture of your organization is assessed based on SOC 2 requirements, known as the Trust Services Criteria (TSC). You can decide which of the five (5) TSC you would like to include in your audit process as each category covers a different set of internal controls related to your information security program. The five TSC categories are as follows:

Security (required)
- The Security Category is required and assesses the protection of information throughout its lifecycle and includes a wide range of risk-mitigating solutions.
Availability (optional)
- The Availability Category reviews controls that show your systems maintain operational uptime and performance to meet your objectives and service level agreements (SLAs).
Confidentiality (optional)
- The Confidentially Category examines your organization’s ability to protect information throughout its lifecycle from collection, to processing and disposal. This is particularly important if you’re storing sensitive information protected by Non-Disclosure Agreements (NDAs) or you’re required to delete information after processing.
Processing Integrity (optional)
- The Processing Integrity Category ensures the data your organization processes is free of accidental or unexplained errors.
Privacy (optional)
- The Privacy Category reviews the Personally Identifiable Information (PII) that your organization captures from customers, such as social security numbers, birthdays, etc.
Note- the more TSC categories you’re able to include in your audit, the more you’re able to better your security posture!
What are the top policies and procedures needed for a SOC 2 audit?
To start preparing for your SOC 2 examination, begin with the 12 policies listed below as they are the most important to establish when undergoing your audit and will make the biggest impact on your security posture.
- Information Security Policy
- Access Control Policy
- Password Policy
- Change Management Policy
- Risk Assessment and Mitigation Policy
- Incident Response Policy
- Logging and Monitoring Policy
- Vendor Management Policy
- Data Classification Policy
- Acceptable User Policy
- Information, Software and System Policy
- Business Continuity and Disaster Recovery
For further details on each individual policy and produce, visit SOC 2: The Definitive Guide.
What are SOC 2 controls?
SOC 2 controls are a collection of policies, procedures, and directives dictating the operation of an organization’s systems, ensuring the security, availability, processing integrity, confidentiality, and privacy of both company and customer data. These guidelines aid organizations in managing and safeguarding sensitive information, fostering the implementation of robust security measures and mitigating the likelihood of data breaches and ensuring adherence to regulatory mandates.
How to start a SOC 2 audit
Before starting the SOC 2 audit process, it is important that you’re well-prepared to avoid any lengthy delays or unexpected costs. Prior to beginning your SOC 2 audit, we suggest you follow the below guidelines:
- Undergo a SOC 2 readiness assessment to identify control gaps that may exist and remediate any issues
- Decide which Trust Service Criteria to include in your audit that best align with your customer’s needs
- Choose a compliance automation software tool to save time and cost. Pro tip- select a licensed CPA firm that also offers compliance automation software for an all-in-one solution and seamless audit process that doesn’t require you to switch vendors mid-audit.
During the initial stage of the audit process, it’s important that your organization follow the below guidelines:
- Review recent changes in organizational activity (personnel, service offerings, tools, etc.)
- Create a timeline and delegate tasks (compliance automation software will make this activity much less time consuming)
- Review any prior audits to remediate any past findings
- Organize data and gather evidence ahead of fieldwork (preferably with automated evidence collection)
- Review requests and ask any questions (pro tip- it’s important to choose an experienced auditing firm that’s able to answer questions throughout the entire audit process)
What is compliance automation software?
If you’re looking for SOC 2 software, compliance automation software may be the best solution. Compliance automation software allows users to consolidate all audit information into a single system to gauge readiness, collect evidence, management requests and continually monitor your security posture.
When selecting a compliance automation software it is recommended that you look for one that offers:
- Automated readiness assessments
- Automated evidence collection
- Policy templates
- Auditor assistance when needed
- Cloud integrations
- Project dashboard
- Consolidated audit requests
- Continuous monitoring
It’s important to note that compliance automation software only takes you so far in the audit process and an experienced auditor is still needed to conduct the SOC 2 examination and provide a final report.
What’s the timeline of the SOC 2 audit process?
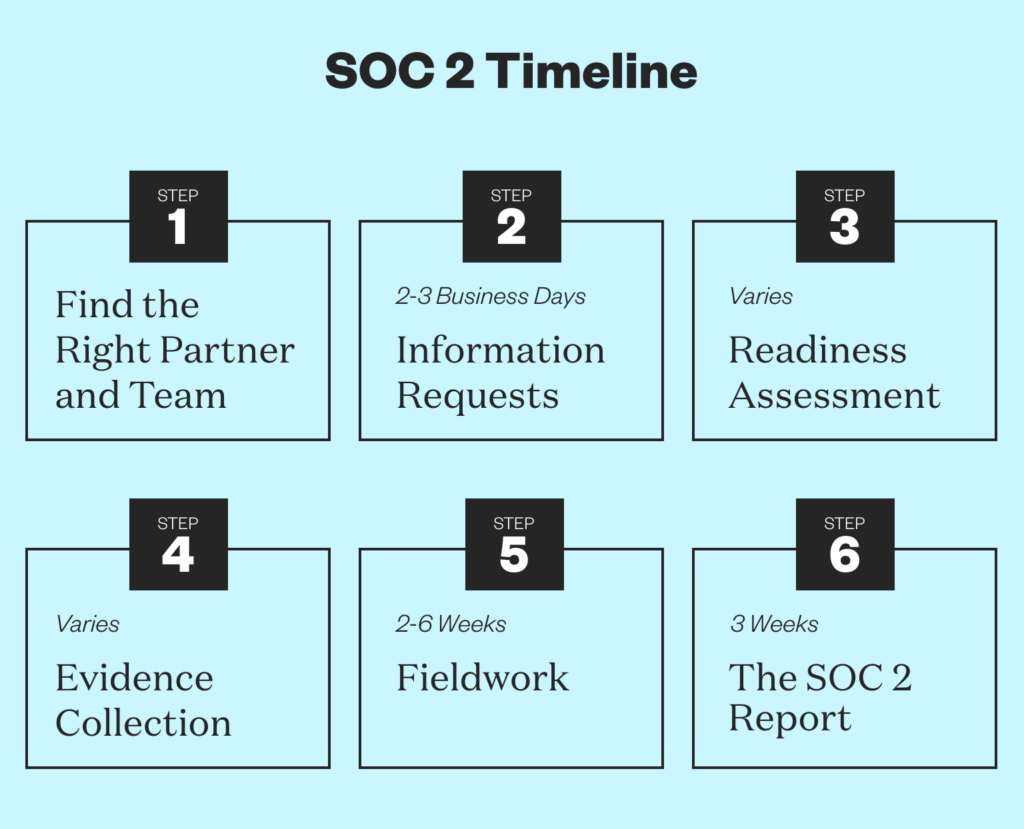
SOC 2 timelines vary based on the company size, number of locations, complexity of the environment, and the number of trust services criteria selected. Listed below is each step of the SOC 2 audit process and general guidelines for the amount of time they may take:
Step 1: Find the Right Partner and Team
A SOC 2 must be completed by a licensed CPA firm. If you choose to utilize compliance automation software, it’s recommended that you select an auditing firm that also offers this software solution for a more seamless audit.
Step 2: Information Requests: Estimated Timeline: 2-3 Business Days
Your audit team will generate an Information Request List (IRL) for your organization. The information in this list is based on the scope, the chosen Trust Service Criteria, and other factors such as cloud hosting services, locations, and company size.
Step 3: Readiness Assessment: Estimated Timeline: Varies based on scope
If it’s your first audit, we recommend completing a SOC 2 Readiness Assessment to find any gaps and remediate any issues prior to beginning your audit.
Step 4: Evidence Collection for a SOC 2 Audit: Estimated Timeline: Varies
The time it takes to collect evidence will vary based on the scope of the audit and the tools used to collect the evidence. Experts recommend using compliance software tools, like A-SCEND, to greatly expedite the process with automated evidence collection.
Step 5: Fieldwork: Estimated Timeline: 2-6 Weeks
This phase includes walkthroughs of your environment to gain an understanding of your organization’s controls, processes and procedures. The time it takes to complete this phase will vary based on your scope, locations, TSCs, and more but generally, most clients complete in two to six weeks.
Step 6: The SOC 2 Report: Estimated Timeline: 3 Weeks
The audit team will provide a SOC 2 report for your company that comes in two parts. Part one is a draft within three weeks of completing the fieldwork in which you’ll have the opportunity to question and comment. Part two is a final report two weeks after the draft has been approved with the inclusion of the updates and clarifications requested in the draft phase.
What’s the difference between SOC 2 Type I and Type II?
When determining what type of SOC 2 assessment to undergo you will have two options resulting in two different reports, a SOC 2 Type 1 audit and a SOC 2 Type 2 audit. There are two main differences between the different audit types. The first is the duration of time in which the controls are evaluated. A SOC 2 Type 1 audit looks at controls at a single point in time. A SOC 2 Type 2 audit looks at controls over a period of time, usually between 3 and 12 months.
In addition, SOC 2 Type 2 audits attest to the design, implementation, and operating effectiveness of controls. A Type II provides a greater level of trust to a customer or partner as the report provides a greater level of detail and visibility to the effectiveness of the security controls an organization has in place.
What’s the difference between SOC 1 and SOC 2?
The difference between SOC 1 and SOC 2 is that a SOC 1 audit addresses internal controls over financial reporting. A SOC 2 audit focuses more broadly on information and IT security. The SOC 2 audits are structured across five categories called the Trust Services Criteria and are relevant to an organization’s operations and compliance.
What is a SOC 3 report?
To be issued a SOC 3 report, you must have first earned a SOC 2 report. A SOC 3 report is a public-facing version of the SOC 2 report intended for distribution and/or publication without the need for a non-disclosure agreement (NDA). A SOC 3 report is a SOC 2 report that has been scrubbed of any sensitive data and provides less technical information making it appropriate to share on your website or use as a sales tool to win new business.
What’s the difference between SOC 2 and ISO 27001?
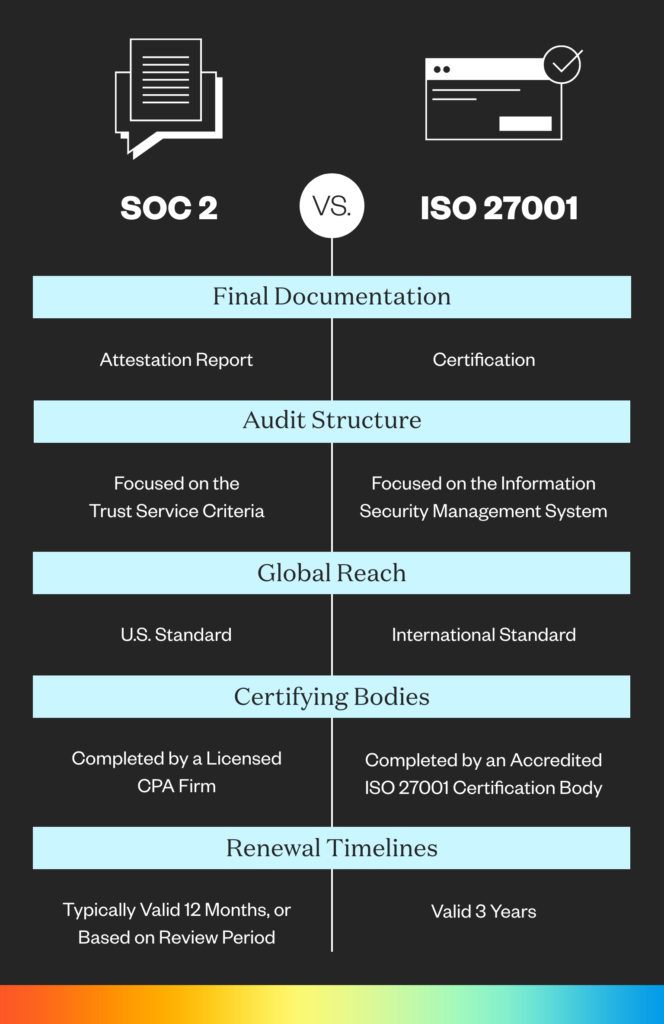
Both a SOC 2 report and ISO/IEC 27001:2013 certification are extremely attractive to prospective customers. Below are the major differences:
Certification vs. Attestation: ISO 27001 is a certification issued by an accredited ISO certification body and includes an IAF (The International Accreditation Forum) seal. SOC 2 is an attestation report provided by a third-part assessor such as a CPA firm.
ISMS vs. Trust Services Criteria: ISO 27001 is a pass/fail audit focused on the development and maintenance of an Information Security Management System (ISMS). SOC 2 is structured around the five Trust Service Criteria and includes an auditor’s opinion of the controls in place for each chosen TSC. A final SOC 2 report is much more detailed than the one-page letter that you receive with an ISO 27001 certification.
Global Reach: ISO 27001 is an international standard throughout the world while SOC 2 is primarily US-based. Note- while SOC 2 is American-born, it’s important for any organizations doing business in the US, and is rapidly gaining traction in Europe.
Certifying Bodies and Renewal Timelines: SOC 2 attestations are carried out by a licensed CPA firm and valid for 12 months. ISO 27001 certifications are carried out by an accredited ISO 27001 certification body and are valid for three years with annual surveillance audits.
Can you fail a SOC 2 examination?
No, you cannot “fail” a SOC 2 audit. It’s your auditor’s job during the examination to provide opinions on your organization within the final report. If the controls within the report were not designed properly and/or did not operate effectively, this may lead to a “qualified” opinion. This indicates that one of the SOC 2 criteria had testing exceptions that were significant enough to preclude one or more criteria from being achieved. Audit reports are crucial because they speak to the integrity of your executive management team and affect investors and stakeholders.
What should I do with my final report?
While you’re not able to publicly share your SOC 2 report unless under NDA with a prospective customer, there are ways you can utilize your SOC 2 assessment achievement for marketing and sales purposes.
- Announce earning your SOC 2 report with a press release on the wire and on your website. Then, share on your social media platforms!
- Showcase the AICPA badge you earned on your website, email footers, signature lines and more.
- Send a short email to customers announcing your SOC 2 report.
- Write a blog around earning your SOC 2 report and how this effort further demonstrates that you take your customer’s data security seriously.
- Teach your sales team how to speak about SOC 2 and the benefits it provides to customers.
If you would like a public-facing report to share, consider purchasing a SOC 3 report.
How long is my final report valid?
When you earn your final SOC 2 report, it’s generally valid for 12 months. Therefore, a SOC 2 audit should be conducted annually as an internal benchmark to assess your security posture year-over-year.
What are a few helpful SOC 2 resources?
SOC 1 vs SOC 2: What’s The Difference?
SOC 2 Framework: What You Need to Know
A Guide to SOC 2 Reporting: What Is a SOC 2 Report?
What are the SOC 2 Trust Services Criteria?
SOC 2 Compliance Requirements: An Overview
The Role of SOC 2 Auditors vs. Compliance Software
What’s an example of SOC 2 in the real world?
Below are several customer testimonials in which the organization earned a SOC 2 report to drive revenue, build customer trust and better their security posture.
Raindrop Earns SOC 2 Report with A-LIGN
ENSEK Earns a SOC 1 and SOC 2 Report, Building Customer Trust
MPS Monitor Demonstrates the Cybersecurity Gold Standard by Earning a SOC 2 Report
Plutoshift Utilizes A-LIGN to Earn SOC 2 Report and ISO 27001 Certification
Hifi Engineering Earns First SOC 2 Report
What is the history of SOC 2?
In 2010, the AICPA (The American Institute of Certified Public Accountants) introduced SOC 1 and SOC 2 to combat the growing need of companies to validate their cybersecurity posture.
Ready to start your SOC 2 audit?
SOC 2 can help you win more business and stand out from your competition. A-LIGN is the top issuer of SOC 2 audits in the world and has completed over 5,000 SOC 2 assessments. We provide the tools and expertise to help you during every step of the SOC 2 audit process — from readiness to report.
Ready to start your SOC 2 audit? Complete the below form to speak with an expert at A-LIGN.
