CISO insights: Small steps, big impact –Strengthening security through employee training and culture
Cybersecurity is a field often associated with complex technology and large-scale strategies. Yet, prioritizing the “low-hanging fruit,” engaging employees through creative training, fostering a collaborative security culture, and making smart technology investments can significantly enhance your organization’s security posture. Ultimately, it all comes down to empowering the people who protect your data.
This article authored by Validic‘s CISO, David Hoover, reflects on how success often lies in addressing the smaller, foundational aspects of security.
Why the small things matter
Cybersecurity breaches rarely begin with highly sophisticated methods. Instead, bad actors often exploit simple oversights such as weak passwords, unpatched software, or unsuspecting employees clicking on phishing emails. These are the simple things — and they are also the vulnerabilities that companies can address most easily.
At Validic, we prioritize basic but crucial measures like local antivirus updates, regular software patching, and multi-factor authentication. These steps may seem mundane, but their impact is profound. For example, keeping software updated not only fixes known vulnerabilities but also signals to attackers that your organization is proactive about security.
By tackling these smaller issues head-on, you’re building a strong foundation that complements your broader security measures. The best part is that these actions often require minimal resources but deliver significant returns in protection.AI is a challenge and a tool in cybersecurity, changing how leaders protect their systems. With more focus on identity-based security and higher accountability at the top, leaders need to adapt quickly, stay strong, and build trust. This highlights the need for proactive strategies and new technologies to keep up with the constantly shifting landscape.
Making security training engaging (and unforgettable)
Security training is one of the most important — and, unfortunately, one of the most dreaded — parts of any organization’s cybersecurity efforts. Let’s face it, not everyone finds discussions about security protocols thrilling. The challenge lies in making the content memorable and engaging.
One of Validic’s most successful training campaigns featured employees’ pet photos. A snarling chihuahua, for instance, became the face of a reminder to “watch out for spam emails.” This quirky, relatable approach led to greater retention of security best practices and created a sense of community. Employees looked forward to the trainings, not just out of obligation but because they enjoyed participating.
To make security training more engaging and memorable, consider creative approaches like gamification—turning lessons into interactive challenges with rewards for participation. Use pop culture references from familiar franchises such as Star Wars or Friends to make concepts more relatable and incorporate storytelling by sharing real-world examples of cybersecurity wins and failures to highlight key takeaways.
When training isn’t just informative but also fun and interactive, it shifts the perception of security from annoying compliance to meaningful participation.
Building a collaborative security culture
For a long time, security teams have been perceived as the “department of no,” blocking projects and requests without explanation. This approach not only frustrates employees but also creates resistance to security protocols. Shifting this dynamic is essential to building a collaborative and effective security culture.
At Validic, we emphasize listening to employees when they make requests — whether it’s for new software tools, different workflows, or exceptions to certain policies. Instead of shutting them down immediately, we ask a simple but powerful question: “Why?”
This openness provides two key benefits: employees feel heard, and security teams can make more informed decisions to satisfy both security requirements and operational needs.
Balancing high-tech solutions with practicality
The cybersecurity marketplace constantly churns out advanced tools and technologies. It’s tempting to chase every shiny new solution, but organizations must assess whether these tools align with their broader goals and provide a strong return on investment.
At Validic, we tend to avoid single-use technologies. Instead, we favor tools that offer multiple functions, providing more flexibility and value. For instance:
- An integrated threat detection platform might cover endpoint security, email scanning, and cloud monitoring, eliminating the need for separate systems.
- A centralized patch management system can handle software updates across various departments, reducing manual effort.
Of course, there are exceptions. Specific compliance or operational needs might necessitate a niche solution. But generally, investing in versatile technologies not only simplifies security management but also ensures that updates and improvements benefit multiple areas simultaneously.
The human element in cybersecurity
All the encryption, firewalls, and multi-factor authentication in the world won’t protect your organization if employees don’t follow security best practices. Humans are the first line of defense — and, unfortunately, often the easiest target for attackers. This truth underscores why investing in your people yields the highest returns.
Your employees should be empowered to understand their role in protecting sensitive information like Protected Health Information (PHI) and Personally Identifiable Information (PII). When employees feel confident about security, it impacts interactions with clients, too.
The key is continuous education, clear communication, and fostering an environment where employees feel invested in your organization’s security goals.
How CISOs can empower their people with technology
- Audit basic vulnerabilities: Address outdated software, weak passwords, and overlooked security gaps.
- Revamp training programs: Use interactive and engaging formats to help employees internalize key concepts.
- Foster a collaborative culture: Shift from a restrictive approach to one that welcomes employee input and participation.
- Invest in flexible tech: Choose multifunctional tools that offer long-term value and adaptability.
- Empower your workforce: Keep security awareness fresh and continuous—your people are your strongest asset.
Cybersecurity isn’t just about preventing attacks — it’s about building a culture of shared responsibility. By focusing on fundamentals and small, strategic steps, organizations can create a resilient posture where every person contributes to lasting security success.
About David Hoover
David Hoover is a seasoned expert in IT security for 20 years, and performed several different roles for many types of organizations including state and federal government, educational universities, and privately held companies. David has extensive expertise in social engineering, vulnerability analysis, and endpoint security.
In his current role, David is responsible for developing and direction of data security and privacy, including establishing a data privacy and information security program for products, support, health software data development and other services within the company to achieve ISO/IEC 27001 and HITRUST certifications. David also leads HIPAA, CCPA, and GDPR compliance requirement initiatives.
About Validic
Validic Inc. is a digital health and intelligent digital care solutions company dedicated to improving the quality of human life by making personal data actionable. Through its technology and services platform, Validic delivers solutions to healthcare providers and organizations that improve operational efficiency and health outcomes.
The Seville Declaration on the Professionalisation of AI Auditing
Adopted by participants in the June 2025 AI Audit Workshops, Seville, Spain.
A-LIGN’s VP of Innovation and Strategy, Patrick Sullivan, leads the Certification Working Group that created the IAAA Audit Body of Knowledge. This group met in the Sevilla Sessions to bring together global experts in AI auditing to identify and address the gaps in current practice, structure, language, and expectations for the profession. The intent was to lay the groundwork for formalizing AI auditing as a recognized, standards-aligned discipline that ensures transparency, accountability, and safety in AI systems.
As artificial intelligence (AI) systems shape decisions that affect individuals, institutions, and societies increases, so does the need to have tools that ensure that automated algorithmic systems and AI products are safe and accountable. If AI innovation is to revolutionize jobs, processes, and relationships, it can only do so when it is safe for, and trusted by, users and society. Adequate safety and accountability specifications cannot be achieved without the capacity to independently and continuously evaluate AI systems, models, and their impacts through audits.
We, the undersigned participants of the Seville AI Audit Workshop, are AI experts from different corners of the world and from diverse fields including regulation, law, ethics, engineering, standards development, and frontline audit practice. We are committed to developing and shaping the AI auditing profession as a structured practice that draws on established IT and security auditing processes; captures the new risks and opportunities that AI poses; and brings transparency, accountability, and assurance to how AI systems operate and evolve over time.
During our first meeting in Seville (26-27JUN2025), we identified significant gaps in the current state of AI auditing practices. These gaps include:
- a lack of consistent terminology and definitions,
- undefined scope boundaries,
- missing professional standards,
- limited agreement on the qualifications required to conduct thorough and sufficient audits,
- an absence of consensus methods, metrics, benchmarks, and auditing procedures.
Without an established AI auditing profession, we believe that general commitments to AI safety and governance efforts will fail to identify and mitigate the many risks of AI, and to realize its potential.
As representatives of an emerging profession, we gathered to listen to one another, challenge assumptions, and find alignment in our purpose. We acknowledged the need for interdisciplinary collaboration going forward. And that shared understanding became our foundation. As a result of this collaboration, we declare our collective intent to:
- Work towards the development of a professional discipline of AI auditing that is credible, interdisciplinary, grounded in evidence, and committed to advancing trust and safety in AI.
- Align the practice of AI auditing with recognized international regulations, best practices and standards, including (where applicable), but not limited to ISO/IEC 42001, 42006, 27001, 27006, and related assessment frameworks, to ensure that AI audits are thorough and of sufficient depth to assure trust and safety.
- Define and share core competencies, methodologies, and ethical and accountability principles that guide AI auditors in their responsibilities to the public, to clients, and to the systems they assess.
- Offer our experience, tools, and networks to developers and policymakers to facilitate regulatory testing, improve AI policy, and promote best practices.
- Promote global collaboration so that AI audits remain responsive to cultural, legal, and regional differences while being repeatable and meeting sufficient and appropriate assurance.
- Prioritize the meaningful involvement of impacted communities in audit design, scoping, execution, and follow-up, recognizing that legitimacy cannot exist without stakeholder voices.
As a first step in our shared journey, we will work together on defining and testing a set of “minimum viable audit” frameworks and metrics for different use cases, incorporating both existing and established auditing procedures and the specificities brought about by advanced AI technologies.
This declaration is not the final word. It is the beginning of an organized effort to formalize what many of us have already been practicing informally. In the months ahead, we will work together to advance this vision, convene others, and build the infrastructure needed to sustain a professional field of AI audit that brings cohesion and direction to the many efforts of people working around the world on AI evaluations, assurance, and trustworthiness.
Signed in good faith by the participants of the Seville Workshops,
July 2025
Expanding your business into the American market offers a great opportunity for growth. The U.S. market offers potential, talent availability, and proximity to innovation hubs, making it an attractive place to grow your business. Plus, if you’re selling to global customers, it can give your organisation a competitive advantage over companies that don’t have an American presence.
While your business prepares for this significant milestone, there is one element you can’t forget about: compliance. Expanding into the U.S. brings all sorts of opportunities, but it also requires developing your compliance program to meet the needs of a new market.
Before committing to an expansion, it’s essential to consider the cybersecurity compliance frameworks and standards your company will need to secure to do business in the U.S. and how these will fit into your overall compliance strategy.
Compliance is a key part of your expansion plan, and it will cost you to make a misstep. Failure to comply with American frameworks can lead to lost business, broken customer trust, and worst of all, civil and criminal penalties.
In this guide, we’ll share the state of compliance the U.S. and get you up to speed on the frameworks your compliance team should focus on, plus best practices for developing a comprehensive compliance strategy for your U.S. expansion. Want to follow along? Download the complete guide. Read on to explore:
- Common frameworks and which industries they apply to
- Barriers to entry and how to get ahead of potential challenges
- How to choose an international audit partner
Common compliance standards in the United States
With the opportunity that lies in the U.S., there are many compliance frameworks to understand before you can do business in and with the country. Like many countries, the United States has its own variety of frameworks by industry.
As a baseline, understanding the frameworks that apply to your organisation is critical when preparing your expansion. Beyond this, complying with these standards sets your business up for success in a few ways:
- Competitive advantage: Many of your competitors, especially those without an American presence, won’t be compliant with the same standards you are. This gives your organisation a competitive advantage when vying for new customers in the U.S. Earning new compliance certifications isn’t just about appeasing potential customers, it’s about driving revenue for your organisation: missing certifications can mean lost business.
- Get ahead: If you’re planning to expand, getting ahead of these standards is going to help your organisation sell quicker and prepare for the flurry of activity that comes with a business expansion. Audit cycles can be long and time consuming, so it’s best to start them sooner rather than later.
- Build customer trust: Committing to new standards demonstrates to your customers that you care about protecting their sensitive information. Plus, entering a new market means your brand might not be known yet. Earning the appropriate compliance certifications can create trust with a strong security posture, giving new customers confidence in your organisation
Popular frameworks
Understanding the most popular frameworks in the U.S. and how they might apply to your organisation is a great first step to entering the market.
- SOC 1: SOC 1 reports are common for organisations that handle, process, store, or transmit financial information. This framework is common in the financial industry and ensures that clients’ financial information is protected through internal controls. The most common recipients of SOC 1 reports are payment processors, data centres, and benefits companies.
- SOC 2: SOC 2 is the most popular cybersecurity audit in the U.S. This framework is designed to protect customer data used by third-party service providers and to ensure it is stored and processed securely. A SOC 2 attestation is earned when an organisation meets a high level of security in each of the five Trust Services Criteria. A variety of organisations can be subject to SOC 2, including data centres, SaaS vendors, and other cloud computing companies.
- FedRAMP: FedRAMP is a certification required for any cloud computing provider that plans to do business with the U.S. government. This standard is designed to protect federal information stored, processed, and transmitted by government contractors. Any organisation that is currently offering, or seeking to offer, cloud products or services to a federal agency will need to successfully complete a FedRAMP assessment.
- CMMC: The Cybersecurity Maturity Model Certification (CMMC) is a newly published certification for U.S. Department of Defense contractors. This standard is designed to protect Controlled Unclassified Information, or CUI, frequently used by organisations doing business with the DoD. There are three levels of certification in CMMC that measure cybersecurity practices related to information sensitivity and threat range. This certification is required for all organisations that plan to do business with the DoD.
- FISMA: FISMA, or the Federal Information Security Modernization Act of 2014, is a federal law that requires federal agencies to develop, document, and implement a comprehensive information security program. It supports the operations and assets of the agency, including those provided or managed by another agency, contractor, or other sources. This certification is mandatory for all federal information systems and contractors that manage or process federal information.
- HIPAA: The Health Insurance Portability and Accountability Act, or HIPAA, is a common framework in the healthcare industry designed to protect individually identifiable health information. HIPAA is a U.S. law and required for any entity that stores, processes, transmits, or touches patient health information that lives in the U.S. or with U.S.-based companies. This standard can be satisfied by the controls and requirements set in place by HITRUST.
- HITRUST: HITRUST is a comprehensive, prescriptive framework designed to empower organisations in highly regulated industries, like healthcare, to build and demonstrate a mature cybersecurity and compliance strategy.
Barriers to entry and how to overcome them
Demonstrating your commitment to cybersecurity and compliance in the U.S. doesn’t have to be difficult, but there are a few barriers to entry that your organisation should be aware of before taking the leap.
Context
Understanding current and emerging frameworks in the U.S. is essential to a successful overall compliance strategy. Just as you keep an eye out for new regulations from governing bodies in your region, it’s imperative to be ready for change and understand the complete picture of U.S. compliance.
The solution? Enlisting the help of a compliance partner that has a base in the U.S. and a global presence. This will ensure you have someone in your corner who recognises the historical knowledge and overall landscape of what’s important to your organisation as you take this next step.
Audit complexity
Entering a new market means your audit cycles could become more complicated. Your team will be managing changes in priorities as your path to business in the U.S. becomes clearer. This means your organisation could need more support internally to support the increased need for documentation and organization for these new frameworks.
To avoid the pressures associated with audit complexity, consider consolidating your audits and assessments with a single provider. The audit consolidation process identifies overlaps between frameworks to reduce repetitive tasks, save time, and drive consistency. Your best bet is to work with an audit team that has an international presence and can identify overlaps to simplify your audit cycle.
Synthesizing your audits with one provider will greatly simplify your compliance strategy. If you enlist the help of an audit partner that is accredited by both American-based bodies like ANAB and EMEA-based bodies like UKAS, you’re afforded the opportunity to complete all your audits with one provider, rather than working with one auditor for your EMEA-based certifications and one for your American-based certifications. This can reduce costs and improve communication and collaboration between your organisation and your audit partner.
Customer demands
Investigate typical customer requests in advance so you’re ready when it’s time for your first sale. A U.S. company looking to buy your products and services will likely vet your security systems before onboarding you as a vendor. They may ask you to fill out security questionnaires and share documentation, reports or certifications as evidence that your security practices won’t put them in harm’s way. Understanding and preparing in advance for those requests may help you close deals faster.
How to choose an international audit partner
Choosing your audit partner for this journey is the most important step. This partner will be with you every step of the way. We recommend you consider the following:
- International presence: Choosing an auditor with an international presence is key to a successful audit cycle when you are expanding to the U.S. Look for an audit partner with a presence both in the U.S. and in your region. Your organisation will benefit from U.S. expertise without being restricted to U.S. time zones.
- Experience: Auditors with an international presence have the experience to provide you a global audit cycle, understanding the frameworks you already have and advising you on the standards you’ll need to comply with to do business in the U.S.
- Audit consolidation: Consider the complexity that an international compliance strategy will bring. Partnering with an organisation that can consolidate your audits and simplify the process is essential. Plus, using the same auditor for all of your certifications can save time and money.
- Tech-enabled: We recommend finding a partner that is tech-enabled or that can work with your chosen GRC platform. This will empower both your internal team and your audit partner to work and communicate effectively and efficiently.
- Quality audit: Finally, ensure you prioritize a high-quality report from a trusted auditor. Seek out case studies and testimonials from clients and ask a potential partner about their client satisfaction and audit acceptance rates. After all, your certification is only as good as the audit that got you there.
After you’ve evaluated potential partners and signed a contract, it’s time to begin your U.S. compliance journey!
Why A-LIGN
A-LIGN is a global auditor with a local footprint. We have helped more than 5,700 companies of all sizes build and scale their compliance programme with frameworks including ISO 27001, SOC 2, ISO 42001, PCI DSS and more. We also help companies comply with international regulation requirements such as GDPR, NIS2 and C5, and map their overlaps with applicable frameworks, such as ISO 27001. A-LIGN has offices in EMEA, APAC, Central America, and the U.S., plus more than 100 EMEA-based auditors, demonstrating our commitment to your global compliance strategy. We can help:
- Conduct multiple audits in a single motion: Review and reuse submissions to scale to additional frameworks – saving you thousands in resource costs. Use the evidence overlap between frameworks (such as the ~60% overlap between SOC 2 and ISO 27001) to empower you to do more with less.
- Earn compliance in the U.S. market: A-LIGN is one of a few vendors with local offices and auditors in EMEA and APAC who can offer SOC 2 and other major U.S. cybersecurity frameworks, such as FedRAMP, CMMC and others. We are in a unique position to support companies headquartered in these regions but who also operate in the U.S. market.
- Seamlessly integrate with leading GRC tools: A-LIGN partners with leading compliance automation providers, so you can leverage the technology of your choice. We also use our own technology to streamline communication, track progress, and centralise evidence collection for all audits.
Ready to learn how A-LIGN can help your organisation achieve international compliance? Contact us to get started and download the complete guide to developing a compliance strategy for your U.S. expansion.
Compliance is more than a legal necessity; it’s a way to create business value. Complying with frameworks like SOC 2 and ISO 27001 gives your organization the level of security it needs to operate effectively, establishes trust with your customers, and cultivates a culture of security within your business. Read on to learn why earning these certifications goes beyond checking a box to generate business value.
SOC 2 and ISO 27001 defined
Applicable to all industries, SOC 2 and ISO 27001 are two of the most effective cybersecurity frameworks. Pursuing a SOC 2 report or an ISO 27001 certification (or both) can help increase trust with customers, prospects, and partners.
A SOC 2 audit is performed to ensure an organization securely manages their data to protect the privacy of both the organization and its clients. This framework is used in many industries, but it’s particularly useful for software-as-a-service companies and managed service providers.
Our experts recommend proactively completing a SOC 2 audit before a customer asks to see a report. Scheduling an audit and having a report on-hand when a prospect asks for one will prevent you from delaying important deals.
ISO 27001 is used to demonstrate an organization’s commitment to a strong cybersecurity program. This international standard focuses on data confidentiality, integrity, and availability. Earning an ISO 27001 certification showcases your organization’s commitment to data protection. ISO 27001 is most often used by SaaS, cloud computing, and data processing companies.
By building a culture of information security and diligence, organizations can reduce security incidents through implemented controls that are specific to their unique risks. Customers and partners will also feel more at ease entering a deal where the organization they want to work with has proven their dedication to risk management.
The value of SOC 2 and ISO 27001
These frameworks demonstrate your organization’s commitment to security, particularly when combined. But how do they drive business value?
Build trust among customers and partners
Earning your SOC 2 or ISO 27001 certification builds trust among your customers and partners. These stakeholders want to understand the steps your organization takes to process and manage their data to ensure that it’s in good hands.
The best way to demonstrate your company’s dedication to safeguarding their valuable information is through an audit conducted by a third party. Successfully completing an audit with an outside vendor shows that your organization cares to protect its customers’ data and that your processes match this commitment.
Mitigate risk
Cybersecurity breaches are costly – averaging $4.9M in 2024, according to IBM. Plus, depending on the industry, your organization could be spending even more money to make up for a data breach.
SOC 2 and ISO 27001 help mitigate this risk by defining responsibilities and demonstrating that your organization has sophisticated, mature cybersecurity and privacy practices. Plus, a data breach doesn’t just cost money, it can cost you your reputation as a quality company. Prevent a potential cybersecurity incident by protecting your customers’ data now, before it’s too late.
Beyond SOC 2
Once seen as a strong competitive advantage, earning your SOC 2 certification is now seen as the cost of doing business. It’s a no-brainer to implement this framework that will just get you started on your compliance journey. In fact, 92% of organizations are now conducting at least two audits or assessments per year according to the 2025 Compliance Benchmark Report. This demonstrates that companies are going beyond SOC 2 in today’s regulatory landscape and pursuing additional frameworks like ISO 27001, SOC 1, HIPAA and more to show their commitment to security as an organization. ISO 27001 appears to be taking center stage for the next most important framework with ISO 27001 certifications increasing by more than 20% year over year across all companies surveyed in the 2025 Compliance Benchmark Report.
Having a SOC 2 report is the bare minimum in compliance. As organizations increasingly depend on third-party providers to handle sensitive information, having a SOC 2 report is a fundamental benchmark.
Erika Fry, Director of IT Security, Boomi
Why A-LIGN
If you’re ready to take the next step, contact A-LIGN today to begin your journey to SOC 2 or ISO 27001 compliance. A-LIGN’s commitment to a high-quality compliance strategy is demonstrated by:
- 17.5k+ SOC assessments completed
- 4K+ ISO assessments completed
- #1 SOC 2 issuer in the world
A-LIGN is the leading provider of high-quality, efficient cybersecurity compliance programs. Combining experienced auditors and audit management technology, A-LIGN provides the widest breadth and depth of services including SOC 2, ISO 27001, HITRUST, FedRAMP, and PCI. A-LIGN is the number one issuer of SOC 2 and a leading HITRUST and FedRAMP assessor.
Navigating AI Regulations Around the World
As AI continues to grow, governments around the world are stepping up to establish regulatory frameworks that ensure its ethical and responsible use. From safeguarding human rights to promoting transparency and accountability, these regulations aim to strike a balance between fostering innovation and mitigating risks.
In this blog, we’ll explore key AI regulations from different regions, highlighting their objectives, approaches, and the impact they aim to achieve. We’ll keep this resource updated as new regulations are introduced, so bookmark this page as your go-to guide.
United States
The United States is taking a state-driven and federal approach to AI regulation, with laws focusing on transparency, accountability, and consumer protection. Here are some key regulations shaping AI governance in the U.S.:
California’s Generative AI Training Data Transparency Act (AB 2013)
California’s AB 2013 is the first U.S. law to mandate transparency in generative AI training data. It aims to enhance accountability, protect personal information, and provide users with greater insight into how AI outputs are generated. Signed in September 2024 and scheduled to take effect January 1, 2026, this law requires developers to publicly disclose detailed information about the datasets used to train their AI systems.
Colorado Senate Bill 24-205: Consumer Protections for AI
Colorado’s Senate Bill 24-205 aims to protect residents from algorithmic discrimination in high-risk AI systems. Passed in May 2024 and set to take effect on February 1, 2026, the law prioritizes transparency, risk management, and fairness in critical areas such as employment, housing, and finance. By assigning clear responsibilities to developers and deployers, it ensures AI systems are used ethically and without bias in decisions that significantly impact individuals’ lives.
Texas Responsible AI Governance Act (TRAIGA)
Signed in June 2025 and scheduled to take effect on January 1, 2026, TRAIGA establishes a regulatory framework for AI systems in Texas. The legislation focuses on transparency, risk management, and consumer protection, particularly for high-risk AI systems. It also includes a regulatory sandbox to encourage innovation while ensuring responsible AI development and deployment.
US Artificial Intelligence Research, Innovation, and Accountability Act (S. 3312)
This proposed U.S. legislation introduces compliance requirements for generative AI, high-impact, and critical-impact systems. It aims to enhance transparency, accountability, and risk management while fostering innovation. Although not enacted, the bill reflects a growing push for structured AI governance, particularly in applications that affect public trust, safety, and individual rights.
Europe
Europe is setting the standard for AI governance worldwide with its risk-based approach. Below are some of the region’s most influential regulations:
The EU AI Act
The EU AI Act is a landmark framework for regulating artificial intelligence globally. It introduces a risk-based classification system, categorizing AI applications into four levels: unacceptable, high, limited, and minimal risk. Each category is subject to specific rules and restrictions, requiring companies operating in the EU to implement compliance measures to mitigate legal and operational risks. Initially proposed in April 2021, the EU AI Act underwent final approval in 2024, with certain provisions becoming enforceable in 2025.
Council of Europe Framework Convention on AI, Human Rights, Democracy, and the Rule of Law
This Framework Convention establishes a comprehensive legal framework to ensure AI activities respect fundamental human rights, democratic principles, and the rule of law. It addresses risks such as discrimination, privacy breaches, and threats to democratic processes. This applies to public authorities and private entities acting on their behalf, mandating context-specific measures to manage AI-related risks effectively. Signed in September 2024, its adoption is ongoing, with implementation timelines varying across member states as they finalize national commitments.
Other regions
Across the globe, countries are introducing AI regulations that reflect their priorities and challenges. Here’s what’s happening in other regions around the world:
Brazil’s AI Bill (PL 2338/2023)
Brazil’s AI Bill aims to create a robust framework for the ethical and responsible development, deployment, and use of AI systems. It adopts a risk-based approach, imposing stricter regulations on high-risk systems that could impact public safety or fundamental rights. This bill emphasizes transparency, fairness, and alignment with Brazil’s General Data Protection Law (LGPD) to safeguard privacy. It also proposes the establishment of a regulatory authority to oversee compliance and promote innovation. Approve by the Senate in December 2024, the bill is still under legislative review, but its core measures are projected to take effect in 2026.
South Korea’s Basic Act on AI Advancement and Trust
South Korea’s Basic Act on AI establishes a regulatory framework to promote responsible AI development while maintaining public trust. The Basic Act, enacted in January 2025 and scheduled to take effect on January 22, 2026, emphasizes safety, transparency, and fairness, particularly for high-impact and generative AI systems. It also introduces initiatives such as a national AI control tower, an AI safety institute, and support for R&D, data infrastructure, and talent development.
Japan’s Act on Promotion of Research and Development and Utilization of Artificial Intelligence-Related Technologies (The “AI Bill”)
Japan’s AI Bill is the country’s first law explicitly regulating artificial intelligence. Enacted in May 2025 and taking effect almost immediately, this bill outlines core principles for AI research, development, and use, while establishing the government’s Fundamental Plan for AI. The legislation also creates an Artificial Intelligence Strategy Center to oversee national policies and promote ethical AI practices.
Building a future of ethical AI
As artificial intelligence continues to reshape industries and societies, the global regulatory landscape is evolving to ensure its ethical and responsible use. By understanding and navigating these frameworks, businesses and stakeholders can not only mitigate risks but also unlock AI’s full potential to drive innovation.
How to Successfully Prepare for an Audit
Preparing for your next audit is just as important as the audit itself. Whether it’s an audit for SOC 2, ISO 27001, or another framework, this process involves gathering documentation, understanding new frameworks, and ensuring your organization is set up for success. There are many ways to accomplish your audit preparation including readiness tools, consultants, and more. Keep reading to explore these audit preparation methods and decide which is the best fit for your organization.
Types of readiness partners
There are three primary types of readiness partners, or the option to rely on internal resources to ensure proper readiness. These are all great options for succeeding on your journey to compliance, the trick is selecting the right fit for your organization’s needs.
vCISOs
Virtual CISOs, often referred to as vCISOs, serve as the designated security leader for your organization. These roles operate as a CISO without being a direct employee of your company. This person is empowered to make strategic decisions, authorize purchases, and act on your behalf in the interest of cybersecurity and risk management. Typically, a vCISO is leveraged in companies that do not have a full-time information security leader, like a CISO, that can provide support for compliance and information security initiatives.
MSPs
Managed service providers are third-party companies that operate as an extension of your internal team, overseeing the deployment, configuration, and management of your security and compliance technology ecosystem.
This type of partner is embedded in day-to-day operations at your company. They will handle tactical execution, integrations, and troubleshooting.
Consultant/advisory
Consultants are third-party experts that provide a high level of guidance and influence key security and compliance decisions based on deep domain expertise. These partners are often brought in to help your company navigate complex challenges, drive transformation, or steer critical security initiatives. In addition to managing the audit process, consultants can build templates that are customized to the audit requirements of an organization’s compliance strategy and ensure their customer is audit-ready.
Consultants are not directly responsible for execution, but they can play a critical role in shaping cybersecurity strategy and aligning initiatives with business objectives.
In-house preparation
You can also be your own “partner.” Some teams have the appropriate resources in-house or have a teammate with a unique skillset for audit prep. If you’d prefer not to leverage a GRC tool, you can use an audit management platform like A-SCEND, A-LIGN’s in-house tool that keeps track of documentation if you’re completing the rest of the process in-house.
Which tactic is right for you?
After you’ve evaluated all the audit preparation methods, you will need to decide which audit preparation path is right for your organization. Before making any decision, there are a few factors to keep in mind. Consider:
- Experience: How much experience do you or your teammates have with preparing for this particular kind of audit? Have you done it a million times for multiple kinds of companies? Or, is this your first time? Experience will determine how much support you will need throughout the process.
- Time: How much time does your team have available to spend preparing for your audit? Is your team lean or built out? A team with limited resources might be more likely to contract out prep work like this whereas one with a lot of bandwidth might take on this project themselves.
- Environment: Consider the type of environment you are having audited. Is it more complex or simple? Even the most experienced compliance professional might not know enough about working in your kind of environment to take on audit prep.
- Budget: Your budget is going to determine the options available to you. If you have a limited budget, consider whether you will need a tool to help automate the process. If so, a GRC tool would be a great option. If your budget can’t accommodate another tool, you can leverage an audit management system. For those with more budget at their disposal, expert assistance throughout the process with a consultant is a great option.
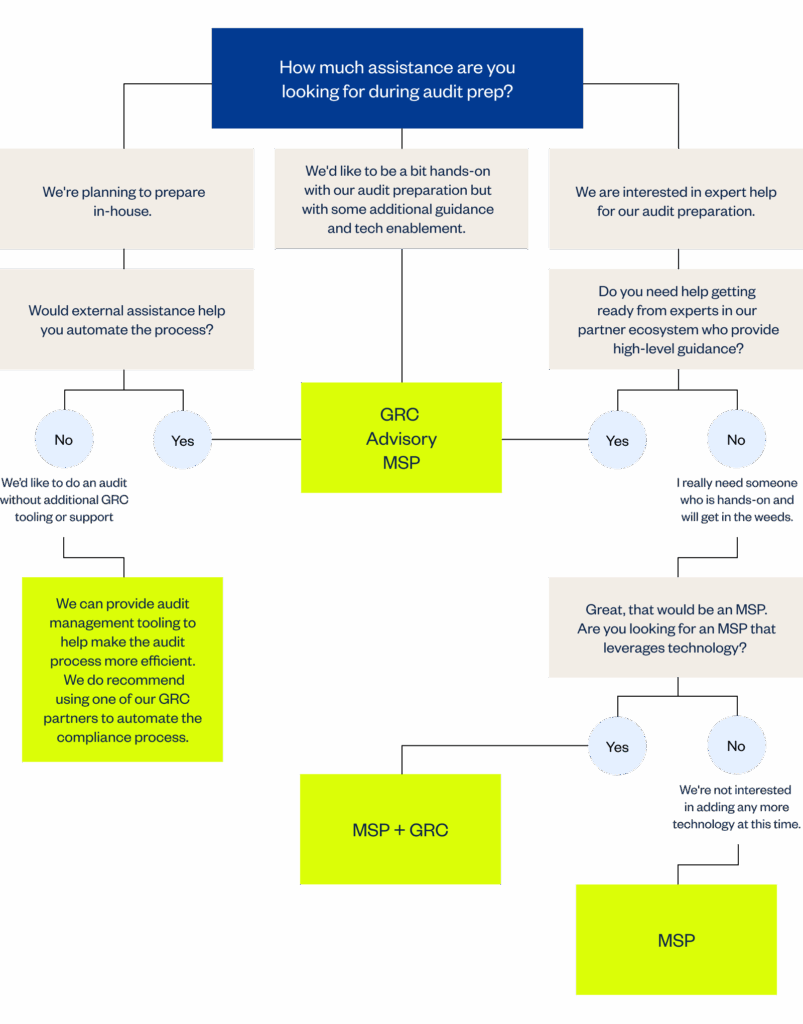
Why engage with A-LIGN early
Before choosing your path, engage with a trusted compliance auditor like A-LIGN that can provide high-quality audits with an expansive network of partners that include GRC tools, MSP providers and consultants to ensure you’re ready for your next audit.
A-LIGN can help connect you with the right GRC tools and trusted consultants to set you up for success and streamline the audit process. Existing relationships can simplify the process for preparation and your audit cycle. Plus, our auditors can provide perspective on GRC tools and best ways of working to save time during the evidence collection process.
If you choose the in-house route for preparation, our audit management platform, A-SCEND, can simplify the process and give your team peace of mind that your preparation is well documented.
Our responsibility as a quality audit partner is to provide a high-quality experience and ensure our clients receive expert guidance. Ready to simplify your audit cycle? Contact A-LIGN today.
Lockheed Martin, a global leader in defense and aerospace innovation, issued a decisive update regarding its implementation of Cybersecurity Maturity Model Certification (CMMC) requirements. This announcement underscores a critical trend sweeping the defense industry — an increasing push by Department of Defense (DoD) prime contractors to elevate and enforce stringent cybersecurity standards among their subcontractors.
If you’re a business working with or aspiring to work with DoD contractors, you might already feel the pressure of meeting compliance benchmarks. However, this is more than just fine print in a contract: CMMC compliance is now a non-negotiable gateway to participating in defense supply chains.
The bigger picture: Prime contractors raising the bar
For years, cyber threats have escalated in sophistication and frequency, threatening national security and the integrity of the defense supply chain. Recognizing the stakes, the DoD launched CMMC as a way to standardize cybersecurity practices across all organizations working with sensitive federal information.
Prime contractors like Lockheed Martin are tasked with ensuring their entire network of subcontractors and suppliers meets these strict cybersecurity requirements as single gap in compliance anywhere along the supply chain could lead to devastating security breaches. This strategic shift by primes not only secures their operations but also reflects the DoD’s unwavering commitment to safeguarding controlled unclassified information (CUI).
By tightening requirements, prime contractors are signaling that every link in the chain must be fortified. Subcontractors, especially smaller firms with fewer resources, are now facing a unique and urgent challenge to align with these standards or risk their place in the defense ecosystem.
Why the urgency?
The DoD is implementing CMMC requirements incrementally, but new updates like Lockheed Martin’s announcement make one thing crystal clear: the time to act is now. Compliance is no longer optional, and waiting until deadlines are looming can result in significant setbacks.
Failing to become compliant could leave your organization at risk of losing critical contracts, disrupting your business operations, and even tarnishing your reputation. Additionally, as primes adopt these standards, organizations without a strategic compliance plan will find themselves left behind in favor of those already meeting or exceeding requirements.
Timely adoption of CMMC compliance offers exciting opportunities as well. Compliant businesses strengthen their credibility, appeal to risk-averse primes, and position themselves as leaders within the defense community. By acting on CMMC now, you’re creating a robust foundation for long-term success.
Steps to get started with CMMC
Understanding where to begin your CMMC compliance journey can feel overwhelming, but breaking it down into actionable steps can simplify the process. Here’s how your organization can tackle CMMC today:
Understand
Read the CMMC final rule, understand program requirements, review DoD’s resources, and familiarize yourself with the practices outlined in the model for each of the CMMC levels.
Identify
Identify your CMMC level and the assets in scope for your CMMC assessment. As a part of this step, you should also complete a gap assessment to identify any areas where there are gaps in your compliance.
Prepare
Develop an implementation plan to address vulnerabilities found in the gap assessment. Prepare for the C3PAO assessment by gathering evidence and preparing for interview questions. During this stage, you may want to undergo a mock audit.
Assess
Following the CyberAB’s CMMC Assessment Process, the C3PAO will review documentation and complete interviews with your team before putting together the final report. If you’ve done the appropriate pre-work, gap assessments, and mock assessments, your team should be well prepared for this step in the process.
Improve
After receiving your certification, the work continues. Plan for continuous improvement and ensure you understand the next steps for future assessments.
A-LIGN’s role in CMMC compliance
Navigating compliance on your own can be complex, but partnering with experts like A-LIGN can streamline your roadmap to success. As a top C3PAO with over 20 years of experience, A-LIGN has completed over 1,000 NIST-based assessments, including FedRAMP, GovRAMP, NIST 800-171. Our trusted team of experts equips businesses with the tools, training, and guidance needed to confidently achieve compliance and securely scale their operations.
By collaborating with a trusted advisor, you not only save time and resources but gain peace of mind knowing you’re meeting prime contractor expectations and DoD mandates.
Act today or be left behind
Lockheed Martin’s latest announcement isn’t just another update, it represents an inflection point for subcontractors across the defense industry. The window to prepare for CMMC compliance is closing, and organizations that proactively align with these standards now will have a competitive advantage.
Don’t wait until it’s too late. Start preparing for CMMC today. Strengthen your cybersecurity posture, secure future business opportunities, and ensure your place in a resilient supply chain that safeguards America’s security.
CMMC Phase 1: Why Contractors Shouldn’t Bet Everything on Self-Attestation
As CMMC enters its official rollout, many defense contractors are treating Phase 1 as a 12-month grace period — a window where self-attestation will be the only requirement for compliance with Level 2. And while that’s technically what the baseline rule allows, there’s a critical detail many are missing:
DoD contracting officers have discretion to require third-party CMMC certifications — even during Phase 1.
This is explicitly stated in the 32 CFR rule, but many organizations are moving forward as if self-attestation is guaranteed. Here’s why that’s a risky assumption — and how you can prepare accordingly.
The costly misconception about CMMC timing
Here’s where many companies are getting it wrong. A common belief is that CMMC certification isn’t needed until 12 months after 48 CFR becomes effective on November 10, 2025. While this phased rollout timeline applies in general, an important detail tucked into the 32 CFR CMMC Program Rule states that DoD Program Managers will have discretion over requiring Level 2 CMMC Certification — even during the first 12 months.
Yes, you read that right. According to the rule:
“Phase 1. DoD intends to include the requirement for CMMC Statuses of Level 1 (Self) or Level 2 (Self)… DoD may also, at its discretion, include the requirement for CMMC Status of Level 2 (C3PAO) in place of the Level 2 (Self) CMMC Status for applicable DoD solicitations and contracts.”
(Source: 32 CFR Part 170.3 e (1) – Cybersecurity Maturity Model Certification (CMMC) Program Rule)
That final sentence is the most important — and often overlooked.
Key takeaway:
If your CMMC strategy revolves around hoping DoD Program Managers won’t enforce certification requirements early, you’re taking significant risks with your pipeline.
What this means in practice
Here’s what’s happening on the ground:
- Many primes are already flowing down CMMC certification requirements to their subs, regardless of phase.
- We’ve seen early RFIs and RFPs include CMMC language — including third-party certification expectations.
- DoD contract officers could require CMMC Level 2 Certifications immediately 48 CFR’s effective date of November 10. Now, readiness is no longer optional and all new DoD solicitations and contracts include some level of CMMC requirement.
Bottom line: the rules may allow for self-attestation, but your contract may not.
The risk of misreading Phase 1
Contractors who assume that Phase 1 guarantees a 12-month reprieve from C3PAO involvement are setting themselves up for:
- Contract risks: Organizations risk bid disqualification due to lack of a required third-party certification.
- Competitive disadvantage: Proactive competitors will be certified and ready to go. Delaying your own certification gives them the edge to secure more opportunities you could have been eligible for.
- Cost surges: The longer you wait, the higher the demand for certification services will be. This could lead to inflated service costs and fewer available resources as deadlines get closer.
- Lost trust: Primes and customers can lose trust, knowing that a contract’s status was unable to be awarded due to your lack of preparedness when the requirements come.
How contractors can prepare
Proactive organizations are avoiding the “wait and see” mindset. Here’s what we recommend:
- Understand: Read the program requirements and familiarize yourself with the practices outlined in the model for each of the CMMC levels.
- Identify: Based on your level, you must identify your scope and any gaps in compliance.
- Prepare: Develop an implementation plan and prepare for the C3PAO assessment.
- Assess: Your C3PAO will complete the CMMC assessment for certification.
- Improve: Perform annual self-assessments before renewing your 3-year CMMC certification.
Learn more: Understand what the guidance means for you, what to look for in a C3PAO, and prepare for your assessment with our CMMC Buyer’s Guide.
Final word
Phase 1 of CMMC’s rollout is not a blanket exemption from certification. It’s a flexible phase that gives the DoD — and contracting officers — room to assess risk and require certification when they see fit.
Don’t leave your compliance future up to chance. By taking action now, you’re not only protecting your pipeline but also safeguarding your reputation as a trusted partner in the defense supply chain.
Need help navigating your CMMC strategy? Schedule a consultation with our team of experts and ensure your organization is equipped to succeed.
Guide: How to Transfer ISO Certification Bodies
Your compliance team dedicates time and mental energy toward securing the best quality ISO certifications to keep your organization in good standing. But things don’t always work out with your certification body. Keep reading to learn about the process of transferring your company’s ISO certificates to a new auditor.
Why would you transfer your ISO certificate?
There are a number of reasons you may want to change your current auditor:
- Inefficient audit process
- Poor communication
- Unsatisfactory final report and certificate
- Consolidating your audit cycles
If any of these sound familiar, you may be heading towards making the decision to finding a new audit partner. But it doesn’t have to be overwhelming. The right partner will make it all worth your while.
Who is eligible to transfer their certificate?
While you might think the answer to this is anyone – it’s not. There are a few criteria that should be met before committing to a certificate transfer:
- Accredited certification body: If you’re looking to transfer to an accredited auditor, your certificate must be from an accredited certification body with valid accredited standards.
- Enough time: This process may take a few weeks to collect the documentation and coordinate with the prior certification body. Pay attention to the timeline for required surveillance audits so that you don’t allow your certificate to suspend of expire. Plan ahead so you have plenty of time for the transfer.
- Certificate scope: Transferring your certificate doesn’t mean you get to expand the scope or locations of your audit, it must stay the same or be a reduced scope for you to move from one auditor to another. You can add more locations or additional scope in your next audit cycle.
What is the process for transferring ISO certificates?
The process for transferring your ISO certificate can be tedious, but the right audit partner will simplify the transition. Take the time to understand what documents you should prepare and how to navigate the steps to transfer auditors to reduce stress and streamline the process.
Preparation
It should come as no surprise that you will need to gather documents before transferring auditors. First, it’s imperative that you verify the validity of your certificate. You cannot transfer certificates from an unaccredited certification body to an accredited one. Luckily, the International Accreditation Forum (IAF) makes it easy to verify the accreditation of your CB with their database – IAF CertSearch. If you worked with an unaccredited certification body, you’ll need to complete an initial certification audit with an accredited certification body.
After this step is complete, we recommend checking the expiration date and scope of your ISO certification. If your certification is days or weeks from expiring, now is likely not the time to begin the transfer process. In addition, you should understand that the scope of your audit must stay the same or reduced for the transfer process. A new location or expanded scope may be added after the certificate has been transferred, either during the next audit or as a special audit.
You should ensure you start this process at least three months before your certificate is at risk of being suspended due to surveillance audits not meeting the required timeline or your certificate expires, preferably more. This is because the process of approving a transfer once you’ve chosen a new certification body can take several weeks. Then, you’ll need to get on the schedule for your next audit. When transferring auditors, it’s particularly important to not rush the process and do it right.
Transfer Process
Now that you’ve prepared and verified your certificate, it’s time to get started!
This step in the process will be very similar to the last time you did it: you will research certification bodies and look for one that aligns with your priorities. We recommend choosing a partner that has an experienced audit team, a high standard of quality, and prioritizes efficiency through technology and audit consolidation. For a comprehensive checklist of questions to ask potential CBs, check out our ISO 27001 Buyer’s Guide.
Checklist: Questions to ask an assessor
- What is your experience with ISO certification audits?
- Does your team have experience with multiple ISO certification standards including ISO/IEC 27001, ISO/IEC 42001 or ISO/IEC 27701?
- Does your organization conduct other audits such as SOC 2, PCI DSS or HITRUST?
- What can I expect during the audit process?
- How do you ensure the quality of your audits?
- How much will my audit cost?
- How long does an ISO audit take with your organization?
- Do you have references and case studies from satisfied customers?
For the complete checklist, download our ISO 27001 Buyer’s Guide.
Your commitment
You’ve chosen a new certification body that aligns with your organization’s priorities – congratulations! Here’s what the process will look like at this stage:
- Certificate verification: At this time, you will provide your current certificate to your new certification body’s audit team. They will verify its validity and request a transfer from your former CB. This step could take some time, so be prepared to wait.
- Review of information: In order to transfer your certificate to a new certification body, a number of items will need to be reviewed in accordance with IAF MD 2: IAF Mandatory Document for the Transfer of Accredited Certification of Management Systems. Your CB will review confirmation of the AB and CB scopes, reasons for transfer, sites that are transferring, previous reports, certificates, audit program, complaints received and additional audits with regulatory bodies. Additionally, your new certification will need to coordinate with the previous certification body to ensure all nonconformities have verified actions in accordance with the severity and that the status of the certificate is not in danger of falling out of active status.
- Contract signing: While a contract may be signed prior to a transfer, an amendment will need to be executed if the transfer is not accepted by the certification body.
Acceptance
After your former certification body accepts the transfer, your new certification body will issue you an updated certificate on the new CB’s paper. There will be no lapse in coverage if your certificate was valid and the scope is the same. Your ISO certification will now continue through the audit lifecycle.
If the certification body does not accept the transfer, you will need to start with an initial certification audit.
Best practices for transferring ISO certificates
- Start early: Like we mentioned, give yourself at least three months from the time you choose your new CB to the expiration date of your certificate. You don’t want any lapse in coverage or to have to start the audit process over again!
- Ensure the validity of your certificate: IAF makes it easy to check the validity of your certification body. Simply look up your CBs information in their database to confirm accreditation.
- Choose a quality partner: You’ve seen the results of choosing the wrong partner. Take the time to choose a partner that meets your standards of quality and aligns with your values in the process.
- Now is the time to streamline: Pick a provider that can handle all of your audits and highlight overlaps you didn’t even know existed. This will help your team work smarter, not harder.
If you’re ready to work with a high-quality audit partner that prioritizes team expertise, technology, and efficiency, A-LIGN may be the choice for you. Contact us today to learn how to get started on the path to a first-class final report.