What Is the Difference Between a Vulnerability Scan and a Penetration Test?
Organizations understand the importance of having a strong security posture. From meeting various compliance and industry regulations to maintaining customer trust, organizations cannot risk overlooking any weak spots in their network. Yet many organizations often leverage a single security assessment and consider their due diligence complete. This approach, however, only tells part of the story. To create a truly strong security posture, organizations should explore both a vulnerability scan and a penetration test and see how they can complement one another.
What is a vulnerability scan?
A vulnerability scan checks an organization’s network and systems for any known vulnerabilities against a database of vulnerability information. At the completion of the scan, the organization obtains a report that outlines their risk exposure.
What is a penetration test?
A penetration test (also referred to as a “pen test”) takes a preventative approach to security. A pen test is a more intentional and manual exercise designed with the goal of “penetrating” an organization’s network and systems to gain access to data. Basically, it’s a simulation that leverages a variety of tools and tactics to map out vulnerabilities.
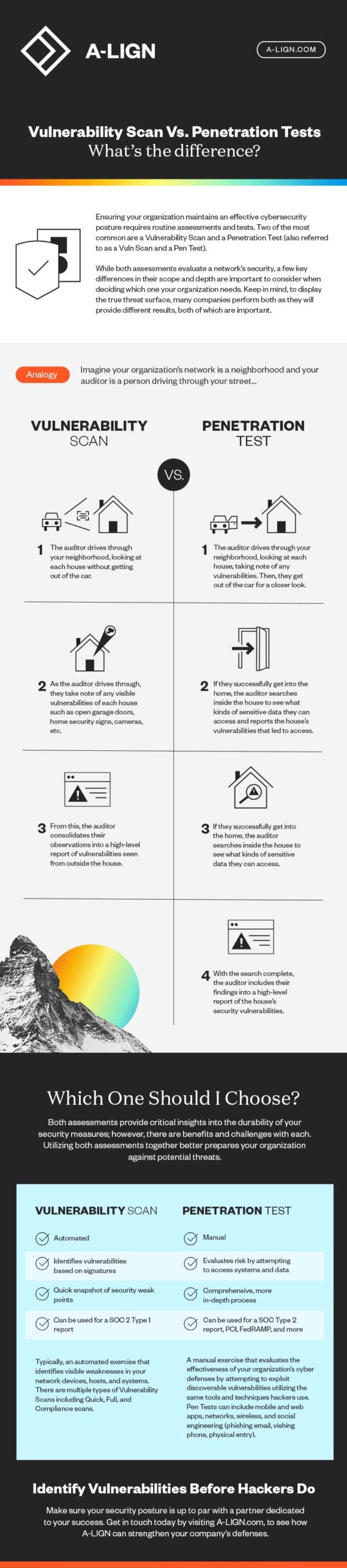
Better together: Combining a vulnerability scan and penetration test
When a vulnerability scan is paired with a pen test, it can provide organizations with deeper insights into where and how to enhance their security posture. A penetration test may not list or confirm every vulnerability in the environment, but a vulnerability scan will scan all systems looking for signatures that match known vulnerabilities that may (or may not) be able to be penetrated. This approach enables an organization to enhance its security posture with a more complete picture of the threat surface.
Ready to schedule your vulnerability scan and pen test?
Pen tests are an important part of any risk management strategy. Now that work-from-anywhere culture is here to stay, there’s no better time to schedule a pen test to ensure your organization is protected against the latest threats.
At A-LIGN, our OSEE, OSCE, and OSCP-certified pen testers emulate the techniques of actual attackers by creating scenarios and strategies unique to your organization in an attempt to breach your networks and applications, with the ultimate goal of helping you improve your security posture. Reach out now to get started on your compliance journey.
Combining Penetration Testing & ISO 27001 Audit for Enhanced Security Assessment
Performing a penetration test alongside a ISO/IEC 27001 audit is crucial as it provides a comprehensive assessment of an organization’s security measures. While an ISO 27001 audit evaluates controls and processes, a penetration test goes further by actively identifying vulnerabilities and simulating real-world attacks. This validation of security controls helps ensure their effectiveness and compliance with Trust Services Criteria (TSC) such as availability, confidentiality, processing integrity, and privacy. Additionally, a penetration test aids in mitigating risks, identifying areas for improvement, and fostering continuous enhancement of security practices.
By combining a penetration test with an ISO 27001 audit, organizations can proactively identify and address security weaknesses, protect sensitive data, and demonstrate their commitment to robust security measures. Performing a penetration test alongside an ISO 27001 audit is vital to comprehensively assess an organization’s security measures. While audits evaluate the implementation of security controls, penetration testing goes a step further by actively identifying vulnerabilities and potential risks. Combining these approaches can help organizations validate the effectiveness of their controls, demonstrate compliance with ISO 27001 requirements, and gain a more thorough understanding of their security posture. The penetration test provides valuable insights into potential weaknesses that could be exploited, allowing organizations to take deliberate measures to enhance their security defenses and minimize potential risks.
ISO 27001 & pen testing benefits
A-LIGN refers to the below list as the top five benefits of penetration testing alongside an ISO audit:
- Risk management: ISO 27001 requirements place a strong emphasis on risk management, requiring organizations to identify and assess risks to the confidentiality, integrity, and availability of information. Penetration testing helps organizations identify vulnerabilities and potential attack vectors that could be exploited by malicious actors. Conducting a penetration test can help proactively identify and mitigate security risks, reducing the likelihood of security incidents and their potential impact.
- Compliance: ISO 27001 is an internationally recognized standard for information security management. It provides a framework for organizations to establish, implement, maintain, and continually improve their information security management system (ISMS). Penetration testing is one of the key controls recommended by ISO 27001, specifically in Annex A, as a means to verify the effectiveness of security controls and assess the resilience of the system against real-world attacks. Performing penetration tests helps demonstrate compliance with ISO 27001 requirements and provides assurance to stakeholders, clients, and regulatory bodies.
- Validation of security controls: Penetration testing validates the effectiveness of an organization’s security controls, including technical controls (e.g., firewalls, intrusion detection systems) and procedural controls (e.g., access controls, incident response processes). It helps identify weaknesses or gaps in security measures, enabling organizations to make informed decisions about improving their security posture and implementing necessary safeguards.
- Incident response preparedness: Penetration testing simulates real-world attacks, allowing organizations to assess their incident response capabilities. By testing detection and response processes, companies can identify areas for improvement and refine their incident response plans. This helps enhance the organization’s ability to detect, respond to, and recover from security incidents effectively, minimizing potential damages.
- Continuous improvement: ISO 27001 promotes a culture of continual improvement. Penetration testing provides valuable insights into the effectiveness of existing security measures and helps identify areas for enhancement. By addressing vulnerabilities identified during penetration testing, organizations can continually improve their security controls and reduce the overall risk exposure.
It’s important to note that while a penetration test can contribute to satisfying certain aspects of risk management, internal audits, corrective and preventive actions, and continuous improvement, it is just one component of an overall security management program. Other items listed, such as documentation control, management commitment, training, competence, and customer focus are typically not directly satisfied by a penetration test but are important considerations for achieving ISO certifications.
Get started by downloading our ISO 27001 Readiness Checklist.
What Is a Vulnerability Scan?
Organizations understand the importance of having a strong security posture. From meeting various compliance and industry regulations to maintaining customer trust, organizations cannot risk overlooking any weak spots in their network. Yet many organizations often leverage a single security assessment and consider their due diligence complete. This approach, however, only tells part of the story. To create a truly strong security posture, organizations should explore various cybersecurity assessments, and see how they can complement a vulnerability scan.
Let’s dig into what a vulnerability scan is and how it compares to — and works with — additional cybersecurity assessments.
What is the purpose of a vulnerability scan?
A vulnerability assessment checks an organization’s network and systems for any known vulnerabilities against a database of vulnerability information. At the completion of the scan, the organization obtains a report that outlines their risk exposure.
There are two approaches to vulnerability scanning: authenticated and unauthenticated. An unauthenticated method scans the organization’s network and systems in a manner similar to a threat actor; the scan is designed to look for vulnerabilities a threat actor could exploit without trusted access to the network (e.g., logging in).
An authenticated method utilizes authentication to scan the organization’s network and systems typically by providing credentials with certain permissions (limited, admin, etc.). This offers insights into where vulnerabilities exist that could be exploited by a trusted user (insider threats) or a threat actor who gained access as a trusted user.
Any organization that has login credentials (read: most common), should include both an authenticated and unauthenticated scan to more accurately reveal both sides of the threat surface. Some vulnerabilities may only be displayed after passing through user authentication, and vulnerabilities can differ based on permissions level. To that point, organizations should include various levels of authenticated scans using accounts with various privilege levels.
What types of vulnerability scans exist?
Though vulnerability scans have two methods, the type of scans that exist typically fall into one of three categories:
- Full scan – As the name implies, a full scan is a thorough vulnerability scan that leverages its database of known vulnerabilities to look for any existing vulnerabilities across an organization’s network and systems. This can also be referred to as a “deep scan.”
- Quick scan – Also known as a “discovery scan” or a “stealth scan,” this type of vulnerability scan is meant to elevate awareness of the type of vulnerabilities that could be possible based on the network devices and system applications that exist.
- Compliance scan – This type of vulnerability scan is leveraged primarily as a means to audit an organization’s security as it relates to compliance regulations.
Different applications and programs that perform a vulnerability scan have different modes, some deeper than others. Worth noting is that when selecting your vulnerability scanning tool, know what you intend to use it for. Some scanners may perform different checks or may not offer some of these options and instead only scan the common ports.
The benefits and challenges of a vulnerability scan
Vulnerability scans offer organizations a number of unique benefits. For example, a vulnerability scan can be run as frequently, or as infrequently, as an organization deems necessary. Though many organizations tend to lean towards a quarterly approach, vulnerability scans can be set to run monthly, sometimes even weekly, depending on an organization’s needs.
And, because they are automated scans, a vulnerability scan can be highly targeted to detect any known vulnerabilities on a range of network devices, such as firewalls, routers, and services, or at an application level. As a result, organizations can more effectively identify and remediate any potential issues associated with a vulnerability faster across the network devices and applications.
Though vulnerability scans paint a solid picture of where known vulnerabilities exist, the picture is, realistically, out of focus. This is because vulnerability scans are designed to detect known vulnerabilities only. Some scan reports do offer guidance on how to remediate the vulnerabilities detected, but it requires a manual check of each vulnerability uncovered to determine validity and prioritize which items should be addressed first.
To that point, a vulnerability scan can generate false positives; some of the results produced may not result in a hack or “penetration” by a threat actor.
Additionally, because vulnerability scans are designed to detect known vulnerabilities only, a vulnerability scan cannot detect zero-day exploits. This means that though vulnerability scans are a great detection tool, they alone cannot provide organizations with enough insights to confidently build a strong security posture.
The challenges associated with vulnerability scans can often lead to a misconception among organizations that a vulnerability scan and a penetration test can be interchangeable. But this isn’t the case. Vulnerability scans and penetration tests take two completely different approaches for displaying attack surface or threat surface and work well together to provide a complete overview.
Penetration test vs. vulnerability scan: What’s the difference?
As we’ve discussed, a vulnerability scan serves as a means of detection, testing an organization’s network and systems for known vulnerabilities. Because it’s automated, it can be highly targeted to look for known vulnerabilities within specific network devices or applications, but the final output requires a manual review to determine which vulnerabilities are valid and which ones take priority to remediate.
A penetration test, however, takes a preventative approach to security. A penetration test (also referred to as a “pen test”) is a more intentional and manual exercise designed with the goal of “penetrating” an organization’s network and systems to gain access to data (e.g., financial records, personally identifiable information [PII], intellectual property). Basically, it’s a simulation that leverages a variety of tools and tactics to map out vulnerabilities. The penetration tester (frequently a security professional) will look to exploit these vulnerabilities in a manner that emulates the behavior of a threat actor. The real purpose of a pen test is to evaluate the risk associated with various vulnerabilities that may be exploitable, resulting in unauthorized access into systems and data..
Similar to vulnerability scans, there are benefits and challenges associated with a pen test. A benefit, for example, is that a pen test is a much more detailed process that provides a more accurate evaluation of an organization’s true risk profile. However, one of the challenges of a pen test is that it will not confirm every vulnerability in an environment.
Clearly, there are some great benefits—and challenges—associated with using a single security assessment. But what if they were combined?
When a vulnerability scan is paired with a pen test, it can provide organizations with deeper insights into where and how to enhance their security posture. As we previously discussed, a penetration test may not list or confirm every vulnerability in the environment, but a vulnerability scan will scan all systems looking for signatures that match known vulnerabilities that may (or may not) be able to be penetrated. This approach enables an organization to enhance its security posture with a more complete picture of the threat surface.
How A-LIGN can help
The best way to know where your organization’s greatest vulnerabilities exist is to hack your own network. Vulnerability scans offer organizations a great option to more effectively detect known vulnerabilities across their network and systems. And, when paired with a pen test, organizations can more effectively enhance their security posture by taking a truly proactive approach to cybersecurity.
A-LIGN is a trusted partner in helping organizations more effectively assess their cybersecurity and compliance needs. Our experienced team employs automated and manual techniques to find weaknesses so you have confidence that your organization’s critical data is protected. Contact us today to learn more.
Why Penetration Testing Is the First Step to Better Prepare for Hacks
The threat landscape is in a constant state of evolution. What may have been a best practice a year ago to help protect your organization against cyber threats may quickly become outdated, no longer providing enough protection on its own.
Consider the type of threats that have impacted organizations of all sizes and across industries, including cybersecurity organizations. Okta, a SaaS-based identity and access management company, fell victim to a third party data breach through the use of compromised credentials, and Shutterfly experienced a ransomware attack. And everyone remembers Colonial Pipeline’s ransomware incident that was the result of a compromised VPN password.
But it doesn’t stop there. Organizations need to take proactive steps to prepare for any threat that could elevate their threat risk, like cyberwarfare. To create and maintain a strong cybersecurity posture, organizations should leverage various assessments to test the strength of their cybersecurity efforts. One of the most effective approaches is to start with a penetration test (pen test).
What is pen testing?
A pen test is a simulated cyber attack that aims to penetrate an organization’s network. Sometimes referred to as “ethical hacking,” a penetration test takes a preventative approach to cybersecurity, evaluating an organization’s infrastructure by utilizing the same tools and tactics threat actors use. This goal-based exercise targets their technology and system’s vulnerabilities to determine if a threat actor can exploit them to gain access.
At A-LIGN, our penetration tests include six unique components that explore every part of an organization’s technologies and network. These include:
- API testing
- Network layer testing
- Mobile application testing
- Web application testing
- Wireless network testing
- Facility penetration testing
Though a pen test is extremely effective in helping organizations enhance their cybersecurity efforts, it’s important to note that it is not a one-and-done test. Most organizations conduct pen tests annually or after a big event, like switching from an on-prem to cloud architecture, development changes or feature enhancements that may introduce new functionality, or after hearing about a noteworthy cyberattack.
Relying solely on annual pen tests, however, is bad practice. Since threats emerge and evolve every day, eternal vigilance is needed to ensure organizations don’t lull themselves into a false sense of security. Fortunately, there are options available to fill in the gaps that exist between tests.
Pen tests + vulnerability scans
To maintain an updated cybersecurity infrastructure, organizations should supplement their pen tests with a quarterly vulnerability scan.
What is a vulnerability scan?
A vulnerability scan, also referred to as a vulnerability assessment, checks an organization’s network and systems for any known vulnerabilities against a database of vulnerability information. Vulnerability scans can be automated to run quarterly, monthly, or even weekly, and can be highly targeted to detect any known vulnerabilities. This enables organizations to more effectively identify and remediate potential issues associated with a vulnerability in a timely manner.
But it’s important to note that vulnerability scans are only used for detection of existing vulnerabilities; they cannot effectively detect a zero-day exploit. Pairing a vulnerability scan with a pen test is beneficial to an organization: The combination of the two provides a holistic approach to enhancing cybersecurity.
Determine your best practice
There is no one-size-fits-all approach to cybersecurity, but there are steps every organization should take to ensure they are effectively testing their security posture on a regular basis.
Leveraging pen tests is just one part of the equation. Additional steps include:
- Developing and implementing a framework. Do your research into existing frameworks, and leverage an acceptable framework, like NIST, to establish cybersecurity controls to reduce your cybersecurity risk.
- Leaning into a zero trust architecture. Be aware of who has access to your most sensitive resources, and limit that access to only the people who need it.
- Exploring additional cybersecurity assessments. Leveraging other assessments, like a Ransomware Preparedness Assessment, can provide even greater insight into your organization’s level of preparedness for a cyberattack.
- Staying educated on the evolving threat landscape. This means knowing what threat actors will try to use to infiltrate your organization, from phishing to ransomware. (To better understand and recognize various cyber threats, download The Ultimate Cybersecurity Guide.)
It’s not if, but when
Every organization across every industry is at risk for a cybersecurity incident. Staying ahead of threat actors requires organizations to adopt a tactical approach to cybersecurity. This means knowing the infrastructure, the devices connected to the network, how they communicate, the characteristics of the organization’s data, and who has access to the data.
Gain this insight by leveraging regular pen tests and supplement them with security scans and audits, including vulnerability scans and a Ransomware Preparedness Assessment.
At A-LIGN, our OSEE, OSCE, and OSCP-certified pen testers emulate the techniques of actual attackers by creating scenarios and strategies unique to your organization so you’re well prepared to respond to any cybersecurity event. Contact us today to get started.
Earning ISO/IEC 27001 or ISO/IEC 42001 accreditation for a certification body is an impressive feat. It takes time, resources and dedication to meet a high level of quality in an organization’s information security and artificial intelligence management systems program.
However, not all accreditation bodies are created equal. If you’re committing to protecting information and taking steps to improve your cybersecurity posture, don’t you want the highest level of quality from your accreditation body as possible?
Which bodies can oversee ISO 27001 and 42001 accreditations?
There are three major certification bodies in the United States: ANAB, IAS and UAF. The two most prominent bodies for ISO management system certification are the ANSI National Accreditation Board (ANAB) and the International Accreditation Service (IAS).
ANAB was the first management systems accreditation body in the United States. It is the largest multi-disciplinary accreditation body in the western hemisphere, with more than 3,000 organizations accredited in approximately 80 countries. The organization is a non-governmental organization and subsidiary of the American National Standards Institute, a non-profit organization. ANAB accredits organizations in compliance with several ISO/IEC frameworks across industries.
When you are looking for an auditor for ISO 27001 or ISO 42001 certification, make sure you choose a certification body that is accredited by a leading accreditation body. Most auditors have the accreditation body logo on their website, but if you don’t see it – do your due diligence and ask.
Why A-LIGN trusts ANAB for ISO certification
One of A-LIGN’s core values is “do the right thing, always.” That means we do the best thing for our clients as a part of our commitment to quality and don’t shy away from hard things. When it comes to choosing accreditation bodies, that means opting for the highest-quality choice. In the U.S., the gold standard for ISO accreditation is ANAB, which is why they have been our accreditation body of choice since the beginning.
Keep reading to learn about ANAB’s commitment to quality and why they are the superior choice for ISO 27001 and ISO 42001 accreditation.
Why ANAB: Stronger global and regulatory recognition
One of the key advantages of ANAB accreditation is its global recognition within the information security industry. ANAB is a signatory of the International Accreditation Forum (IAF) and Multilateral Recognition Arrangement (MLA), which ensures that ISO 27001 certifications accredited by ANAB are recognized internationally. These memberships are critical for businesses operating across borders, as many global clients require an internationally accepted accreditation.
Why ANAB: More rigorous accreditation process for ISO 27001 and 42001
ANAB’s accreditation process for ISO certification bodies is notoriously stringent, ensuring that only the most competent, well-audited certification bodies can issue certifications.
Key aspects of ANAB’s superior accreditation process include:
- Comprehensive audits of certification bodies, including technical evaluations of their ability to assess ISMS compliance.
- Strong oversight and continuous monitoring, ensuring accredited certification bodies maintain high standards. ANAB regularly looks for quality audits that follow the standards required for certification bodies.
- Alignment with ISO/IEC 17021-1, the key standard for bodies certifying management systems, with enhanced scrutiny for information security assessments.
Industry experts believe that ANAB’s high level of scrutiny results in stronger, more reliable ISO 27001 and ISO 42001 certifications, making it the preferred accreditation body for cybersecurity and compliance-driven organizations in North America. ANAB, trusted by firms including EY and Moss Adams, is associated with ANSI, an organization with more than 100 years of standards experience, which sets the stage for higher quality accreditation processes.
Why ANAB: Market and industry preference for ANAB-accredited certifications
In the cybersecurity and information security industries, ANAB accreditation is the gold standard. Many large enterprises, government agencies, and security-conscious organizations explicitly require ANAB-accredited ISO certification from their vendors and partners because of its high standards and reputation.
Companies in sectors such as cloud computing, fintech, healthcare IT, and SaaS often prefer ANAB-accredited certifications because:
- It enhances credibility with customers who prioritize security.
- It facilitates compliance with regulatory frameworks like GDPR, HIPAA, and SOC 2.
- It ensures international recognition, allowing businesses to operate in multiple regions without accreditation-related issues.
Other accreditation bodies do not hold the same influence or trust in the cybersecurity and compliance space. ANAB accreditation is the clear choice for ISO certification in the information security industry. Its strong global recognition, regulatory trust, rigorous accreditation process, and industry preference makes ANAB the accreditation body with the highest standards.
Ready to get started on your organization’s journey to ISO 27001 or 42001? Contact us today to get started with an ANAB-accredited certification body, A-LIGN.
ISO/IEC 27001 is a prominent, globally recognized standard designed to administer and enhance the information security management system. When an organization decides to embark on its ISO 27001 certification journey, it agrees to adhere to a systemic approach to manage sensitive company information, ensuring secure exchange and protection of data. The standard is applicable to businesses across all industries, regardless of their size or the nature of their data. Read on to learn the key ISO 27001 requirements ahead of your organization’s audit.
What are the ISO 27001 requirements?
The ISO 27001 requirements are designed to provide a clear and rigorous framework for protecting and managing valuable data and information assets. These carry inherent business risks if not protected adequately. The standard encompasses key aspects of business, such as risk management, compliance, legal requirements, physical and technical controls around data access, usage, and transmission. All these facets collectively reflect the organization’s commitment to a higher level of data integrity, availability and confidentiality.
If you’re planning on getting your business ISO 27001 certified, the ISO 27001 requirements are more than just getting a badge of honor. Achieving the ISO 27001 certification signals to clients, stakeholders, and regulators that your business has implemented an internationally accepted and independently validated information security management system. Furthermore, it offers a basis for legal compliance, demonstrating your commitment to information security and data privacy.
What exactly are the ISO 27001 requirements? This standard is divided into clauses and annex controls. The former establishes a set of business procedures and processes necessary for managing an organization’s ISMS. The latter consists of 93 controls categorized into 4 groups, which provide guidelines on how to manage specific areas of information risk. Annex A is a comprehensive list of the controls to be considered during risk assessment, applicable based on the nature of the business.
The requirements include, but are not limited to:
Setting up an information security policy
Establishing a clear and comprehensive information security policy is a foundational element to earning ISO 27001 certification. This element of ISO 27001 requirements should outline overarching objectives, principles, and responsibilities for safegaurding sensitive data.
Defining an approach to risk assessment and treatment
A structured approach to risk assessment and treatment is crucial for identifying, evaluating, and mitigating potential security threats. This involves recognizing vulnerabilities, determining their likelihood and potential impact, and implementing appropriate risk treatment measures. By continuously monitoring and updating this process, organizations can adapt to evolving threats and maintain robust information security and meet ISO 27001 requirements.
Implementing data masking and web filtering controls
ISO 27001 requirements mandate implementing data masking and web filtering controls to enhance the security of sensitive information and protect against unauthorized access. Data masking obscures sensitive data elements, reducing exposure during processing or testing, while web filtering restricts access to potentially harmful or inappropriate websites.
Executing training and awareness programs
Organizations must also execute training and awareness programs as part of ISO 27001 requirements. By educating employees about security policies, potential threats, and best practices, organizations can minimize human error and reinforce a proactive security culture. Ongoing awareness initiatives help keep information security top of mind and ensure everyone understands their role in protecting the organization’s assets.
Gathering and analyzing information about threats
Proactively gathering and analyzing information about potential security threats enables organizations to identify and respond to risks before they become a problem. This involves staying informed about emerging vulnerabilities, monitoring threat intelligence sources, and analyzing data to detect patterns or anomalies.
Monitoring systems and implementing incident response procedures
Continuous monitoring of systems and implementing effective incident response procedures are critical components of ISO 27001 requirements. Real-time system monitoring helps detect security incidents promptly, while a well-defined incident response plan ensures swift and coordinated action to mitigate impact.
Deep dive into ISO 27001 requirements
The ISO 27001 standard is a globally recognized information security standard that establishes the best practices for ISMS. Meeting ISO 27001 requirements and earning a certification offers various advantages, from improving efficiency to building stakeholder trust, underscoring the need to grasp and apply these standards.
The ISO 27001 requirements are composed of foundational requirements essential for the effective functioning of an ISMS. These requirements, referred to as controls, are derived from ISO 27002 and found within ISO 27001 Annex A, and typically align with the organization’s information security risks. However, the organization retains the liberty to decide which controls apply to their specific circumstances and document the same accordingly.
An imperative component of the ISO 27001 requirements is the set of mandates for logging and monitoring. These stipulations lay the groundwork for detecting, analyzing, and mitigating potential security incidents. ISO 27001 requirements ask organizations to document significant events and continually scrutinize system activities. This continuous monitoring and logging of activities aim to detect abnormalities quickly, allowing for immediate corrective actions.
Starting from security policy and organization of information security to access control and incident management, the ISO 27001 requirements list is extensive and inherently interrelated. Therefore, stringent adherence and a deep understanding of these standards can fortify information security, thereby qualifying the organization for ISO 27001 certification.
Gaining a comprehensive knowledge of the ISO 27001 requirements is pivotal for organizations pursuing robust information security governance and a strong culture of security. The articulated requirements and stipulations, including specifics like logging and monitoring, offer a holistic blueprint for an effective ISMS. Customizing and implementing these requirements, coupled with continuous monitoring, can lead an organization toward enhanced information security and ISO 27001 certification.
AI is here to stay, making it crucial for organizations to build out their AI compliance strategies. Wondering where to start? The answer is ISO/IEC 42001:2023.
ISO 42001 provides a comprehensive framework with clear guidelines and best practices for AI compliance. We’ve created this guide to provide you with everything you need to know about this standard, including a list of questions to ask when choosing the right auditor. Click here to download the guide.
What is ISO 42001?
ISO 42001 is designed to help organizations manage the risks associated with AI and ensure that their AI systems are developed and used responsibly. This standard provides a framework for organizations that design, develop, and deploy AI systems, focusing on aspects like transparency, accountability, bias identification and mitigation, safety, and privacy. It’s not a mandatory standard, but given its significance and recognition, it’s highly likely to become the benchmark for AI management systems in the future.
While implementing ISO 42001, top management is expected to lead and commit to the AI management system (AIMS) and establish policies and objectives aligned with the organization’s strategy. They’re expected to identify and address AI-related risks and opportunities, provide necessary resources and support, establish processes for AI system development and maintenance, monitor and evaluate AI system performance, and continuously improve the AIMS to keep it effective.
To help organizations manage this standard effectively, ISO 42001 has several annexes (Annexes A-D) that give detailed guidance on adoption. These annexes provide direction on system development and implementation, while addressing organizational objectives, risk management, and industry-specific standards to ensure tailored AI management practices.
Benefits of ISO 42001
From driving innovation with responsible processes to mitigating AI risks through lifecycle monitoring, ISO 42001 brings a lot of value and benefits to businesses. Below are some of the key advantages of ISO 42001:
Stay ahead of AI regulations
ISO 42001 provides a unified framework to adapt to a variety of new regulations. Its focus on trust, transparency, and resilience in AI systems goes well beyond meeting regulatory minimums, making it a highly viable standard.
Build trust and transparency
An AIMS built on ISO 42001 demonstrates trust and accountability through clear communication (Clause 7.4) and transparency (Clause 7.5), building confidence in AI systems and fostering stronger stakeholder relationships.
Minimize financial risk
Adoption of ISO 42001 allows organizations to protect themselves from penalties and gain a competitive edge as certifications become necessary. Through its embedded risk management system, this standard will help companies avoid vulnerabilities and prevent costly overhauls down the line.
Boost operational efficiency
ISO 42001 enhances efficiency by identifying and mitigating risks, improving data quality, and enhancing oversight. Its lifecycle monitoring and stakeholder collaboration boost performance and trust, while its structured risk management minimizes disruptions. It’s adaptable to various organizational sizes and AI maturity levels, allowing it to align with innovation goals.
Strengthen AI governance
ISO 42001 integrates seamlessly with standards like ISO 27001 and ISO 27701, creating a unified governance framework for diverse compliance needs. This combined approach enhances data security, ensures traceable data inputs and outputs, and addresses privacy risks, strengthening AI governance and operational efficiency.
Understanding the process
Like any certification, achieving ISO 42001 compliance comes with its own unique process. Let’s break it down.
Prepare for ISO 42001 Certification
Organizations should start by getting to know ISO 42001 and its clauses, annexes, critical documents, and policy requirements.
From there, conduct a gap analysis to identify discrepancies between your existing AI governance framework and ISO 42001 requirements. Develop a step-by-step implementation roadmap to address these gaps, prioritizing areas that will have the greatest impact on your business.
Companies should set up training sessions for the new processes and provide a way for staff to give their insights and feedback on the new AIMS. Having a centralized location for all of this feedback will make documentation more organized and efficient.
Pro tip: Utilize ISO 42001 to clearly define the desired outcomes for your AI systems. Align these with business objectives to ensure governance efforts directly support strategic goals.
Engage with auditors
After your organization has prepared for certification, you’re ready to choose an auditor. Look for a quality audit partner that aligns their goals with yours.
While evaluating auditors, come prepared with a list of questions and clarifications regarding the process, and be ready to discuss the scope of the audit in detail. We also recommend conducting a pre-audit checklist review and simulating audit scenarios to prepare your staff for the actual assessment.
Undergo the audit process
Designate a team member as the point of contact to streamline communication with your auditor. Your assessment will include interviews with key personnel and a review of documentation.
After your assessment is complete, schedule a meeting to discuss key findings with the internal team and determine the action plans needed for any nonconformities based on the report.
Ensure continuous improvement
Establish a team designated to compliance improvement and progression post-certification. Engage with customers, investors, and partners to communicate your commitment to responsible AI governance. Use Clause 7.4 (Communication) and 7.5 (Documented Information) of ISO 42001 to ensure transparency and traceability.
Selecting an audit partner
Choosing the right audit partner is a crucial part of the process. Not all auditors are created equal, so let’s dive into what you need to look out for.
Expertise
Choose an auditor, or certification body, that is accredited with a high-quality, reputable Accreditation Body, like ANAB. This guarantees they have the expertise to navigate you through the audit process and uphold their procedures to the highest standards given the thorough review process that the certification body must also go through. It’s important to evaluate how long they’ve been operating, the experience level of their staff, their understanding of ISO 42001 compliance, and their experience with other ISO frameworks. Since there are similarities and overlaps with ISO 27001, choosing an auditor who knows ISO and the ISO process can provide valuable insights and ensure a thorough and effective audit.
Quality
It’s important to choose a high-quality audit partner that will align their goals with your organization’s goals. High-quality auditors have extensive experience and knowledge of ISO 42001, allowing them to address potential compliance issues effectively. This minimizes the risk of failing the assessment and ensures that your organization meets all necessary standards.
Efficiency
Efficiency plays a big role in the time and resources required to achieve certification. The assessment process can be complex, but some auditors offer technology to help streamline the process. This can help save time during the certification process and reduce disruptions to your operations. To boost efficiency even further, consider a firm who can handle additional frameworks like ISO 27001, SOC 2, HITRUST, and more. Using the same firm for multiple audits can streamline the process and allow you to consolidate your audits, saving time, resources and money.
Budget
Budget is an important consideration, and as with most things, you get what you pay for. Beware of auditors that are offering assessments for under-market value. When looking at the budget, you should balance it with other factors that are important to you. Are you willing to pay more to expedite your timeline? Is the auditor you choose known for quality? Is it worth it to spend more to work with a trusted auditor instead of a brand-new firm?
Case study: Synthesia
In 2024, A-LIGN issued its first ISO/IEC 42001 certification to Synthesia, making them the first AI video company to achieve ISO 42001 compliance. Synthesia is the world’s leading enterprise AI video communications platform, with more than 55,000 businesses, including half of the Fortune 100, using it to communicate efficiently and share knowledge at scale using AI avatars.
“A-LIGN’s expertise and attention to detail helped us identify and remediate any gaps in our rigorous processes. Together, we have led the way for the rest of the industry in the adoption of this standard, fostering trust and ensuring the long-term success of AI development and use.”
— Martin Tschammer, Head of Security
This certification sets a new benchmark in the industry, showcasing Synthesia and A-LIGN’s joint dedication to compliance innovation and high-quality security. It also highlights A-LIGN’s unwavering commitment to excellence and its role in empowering clients to achieve and maintain the highest levels of compliance in the ever-evolving AI landscape. Read the full success story.
Checklist: Questions to ask an ISO 42001 auditor
Choosing an auditor is a big step in the assessment process and can impact your audit results as well as your experience. These are the key questions to ask your auditor to ensure you’re choosing the best fit for your organization:
- What is your cybersecurity compliance experience?
- How many customers do you work with and how many audits have you completed?
- How many years have you been in business?
- What is your experience with ISO?
- What is your experience with ISO 42001 assessments?
- How many ISO 42001 certifications have you issued?
- How long have you been conducting ISO 42001 audits?
- How well-versed are your auditors in ISO 42001 requirements?
- Do your auditors have specific certifications or training related to ISO 42001?
- Where are your auditors located?
- Are you accredited to conduct ISO 42001 audits?
- Which accreditation body did you choose and why?
- Can you describe your audit process for ISO 42001?
- How do you ensure the quality and consistency of your audits?
- What kind of feedback and reporting can we expect from your audits?
- How much will the ISO 42001 assessment cost?
- What are your rates, and what do they include?
- Are there any additional fees we should be aware of?
- What is the timeline for the ISO 42001 assessment?
- What is the lead time to begin the assessment?
- How long do you anticipate the entire assessment process will take?
- Do you have references and case studies from satisfied customers?
- Can you provide examples of similar organizations you have worked with?
Ready to take the next step with ISO 42001? Download the guide or contact us to learn more.
With the Department of Government Efficiency (DOGE) in the forefront, questions around the future of FedRAMP have begun to circulate. The future of FedRAMP is a topic of much discussion and one that we’ve had with many customers and partners, and we’re here to help guide you through the state of uncertainty that currently exists in the market. We will continue to keep this article updated as news continues to roll in on changes.
FedRAMP 20x
On March 24, 2025, FedRAMP announced its plans for a new assessment process for cloud service providers that will be designed by FedRAMP in partnership with industry stakeholders and agency experts. The new approach is called FedRAMP 20x.
FedRAMP 20x has five key goals:
- Make it simple to automate the application and validation of FedRAMP security requirements.
- Leverage existing industry investments in security by inheriting best-in-class commercial security frameworks.
- Continuously monitor security decisions using a simple, hands-off approach.
- Build trust between industry and federal agencies by leaning into the direct business relationships between providers and customers.
- Enable rapid continuous innovation without artificial checkpoints that halt progress.
Over the next few months, industry and government will come together in public community working groups to discuss key topics and chart a path forward for a more efficient FedRAMP assessment process.
FedRAMP Rev5 updates
As of March 24, 2025 the current Rev5 agency authorization pipeline will remain open without significant changes. The current agency operation backlog is on track to be cleared by the end of April and then the PMO will continue to process new Rev5 agency authorizations based on demand. Until a new process is defined, FedRAMP Rev5 agency authorization remains the only active path to FedRAMP authorization.
The value of FedRAMP in the DOGE era
We believe that FedRAMP is vital for modernizing Federal technology and software – aligned with DOGE’s vision to improve efficiency in the Federal government. We share the belief that FedRAMP has opportunities to continue improving efficiency, aligned with the vision that FedRAMP itself shared in December to improve authorization capacity designed to meet the demand that exists for authorization and create improved paths to faster and more straightforward review processes.
FedRAMP has provided a standardized approach to security and risk assessment for cloud technologies and federal agencies, reducing duplicative effort, inconsistency, and cost inefficiency by providing agencies with a security platform that can be leveraged once across several agencies. Through the “audit once, use many times” approach, GSA has estimated that the program has saved over $700 million in costs associated with one-time assessment and authorization costs.
Charting your path forward
As a top 3 FedRAMP 3PAO, A-LIGN offers the following guidance to CSPs:
- For CSPs considering FedRAMP: We urge you to stay the course. Security remains of critical importance, and with FedRAMP signed into law, Government Agencies are still required to only use cloud solutions with security authorizations. While we do expect changes in FedRAMP funding to evolve objectives and responsibilities, we also know that national security will continue to be a priority. Although FedRAMP process responsibilities may shift a bit, e.g., from FedRAMP to the Agencies, security authorization remains a requirement for cloud solutions that process government data. As a result, our recommendation is to continue pursuit of FedRAMP authorization to open new routes to market and revenue. We believe DOGE’s mission is to modernize and drive efficiency in the Federal government should drive additional uptake in the use of cloud services and being prepared for that will allow your company to win new business.
- For CSPs who are already authorized: Your number one priority should be ensuring continuous monitoring activities are successfully demonstrated. As the FedRAMP program continues to evolve and in discussions about the future state, we’re hearing more and more focus will be placed on Continuous Monitoring (ConMon). In addition, with greater responsibilities shifting to the Agencies, now more than ever, ensure alignment with all your authorizing agencies to determine the right path forward for your company.
The state of FedRAMP
The GSA’s FedRAMP program, which evaluates the security of cloud computing services for Federal agencies, is undergoing significant changes. Although the support team at the FedRAMP Program Management Office (PMO) within GSA may be shrinking in size, the goals and objectives of the Government-wide initiative remain strong and are a focus area for automation and efficiencies. PMO staffing reductions are primarily affecting private sector contractors, with the number of contractors expected to drop to zero due to expiring contracts. Again, this supports the shifting of responsibilities back to the Agencies who are best poised to ascertain the appropriate level of security risk acceptable for the cloud solution they’re authorizing for use.
Despite these changes, FedRAMP continues to be a priority for the US Government. The program is being revamped to increase throughput and enhance government adoption of modern technology. In fact, a recently discussed goal is to decrease the entry barriers so that small businesses in particular are better able to enter the market. FedRAMP’s codification into Federal law in 2022 ensures its staying power, with ongoing efforts to streamline evaluation and approval processes
The role of 3PAOs
While much has been said in the market about the role of the PMO and its impacts on third-party assessment requirements, 3PAOs are crucial for ensuring the security of cloud products – helping to identify risks to government agencies. 3PAOs are beholden to strict standards such as ISO 17020 and FedRAMP-specific requirements set by the American Association for Laboratory Accreditation (A2LA) in their R311 publication. This includes certifications for assessors, continued education, and participation in activities to ensure the integrity of the program.
These requirements ensure that 3PAOs, like A-LIGN, can perform FedRAMP assessments that are high quality for CSPs. Concerns about 3PAO performance and quality are addressed with A2LA as the independent accreditation body, to step in. A2LA conducts a comprehensive initial audit for every candidate 3PAO, followed by a surveillance audit before a full renewal in year 3.
Currently, the Agencies play a role in continuous monitoring, ensuring that cloud service offerings (CSOs) remain secure and compliant over time. However, with the existing cuts and uncertainty around the future of FedRAMP, there is an opportunity for 3PAOs to provide additional assurance to CSPs, government agencies, and taxpayers, to have 3PAOs conduct continuous monitoring activities in lieu of Agencies to ensure security remains fortified.
Moving forward
FedRAMP remains a critical component of federal technology modernization. As the program evolves, CSPs must stay informed and proactive in their compliance efforts. A-LIGN is committed to helping you navigate these changes and achieve your FedRAMP goals.
One of the most crucial pieces of the compliance puzzle is your auditor. Finding the right auditor can mean the difference between an efficient, smooth audit experience and a long list of costly compliance and brand reputation issues.
A-LIGN’s 2025 Compliance Benchmark Report found that report and auditor quality remain top of mind for compliance teams. Our survey revealed that the most important factors for companies when choosing an auditor are:
- Experienced audit team
- Report quality
- Tech-enabled audit
But what does “experienced” mean? Or a “quality” report? We’ll answer those questions below as we cover the six crucial factors to consider when choosing a compliance auditor. Plus, follow along with our Quality Audit Checklist to make sure you get the most from your audit experience.
1. Experience and credentials
When it comes to compliance audits, experience counts. In fact, it might be the most important factor of all. Here are some specific qualities to look for.
Industry tenure and track record
Look for auditors who have been in business for a substantial period — ideally a decade or more — and have completed many audits for the standard you need. Experienced auditors are less likely to make costly mistakes and are better equipped to handle complex compliance landscapes.
An experienced auditor will also generally have a large team of experts with a wide variety of specialties. Auditors on these teams also generally have experience with an array of company types, making it more likely your audit team will have a deep understanding of your priorities.
Certifications and accreditations
Ensure your auditors hold the certifications, licenses, and accreditations required to perform the audits you need. Here are some examples:
Certified public accounting license and registered with the American Institute of Certified Public Accountants — only independent licensed CPAs can issue SOC 1 and SOC 2 attestation reports
Accredited by ANAB, the ANSI National Accreditation Board as an ISO 27001, ISO 27701, ISO 42001 and ISO 22301 certification body
Accredited by UKAS, the United Kingdom Accreditation Service, as an ISO 27001 certification body
Authorized HITRUST External Assessor
Accredited FedRAMP Third Party Assessment Organization (3PAO)
Accredited CMMC Third Party Assessment Organization (C3PAO)
PCI Qualified Security Assessor Company
Maintaining high standards
Not all accreditation bodies are created equal. It’s important to seek out accreditation bodies that maintain high standards of quality. These groups often have a long track record of success and far-reaching expertise in the frameworks you’re pursuing. Plus, their teams have relevant certifications and deep industry experience.
Industry-specific experience
Auditors with experience in your industry will understand your organization’s unique compliance challenges and requirements better. This insight is crucial for providing relevant and effective audit services. If your auditor has experience in the healthcare sector, for example, they’d be familiar with the overlap between SOC 2 and HIPAA compliance. A combined audit could save you significant time and money.
2. Report quality
According to the 2025 Compliance Benchmark Report, 70% of companies deemed the quality of compliance reports extremely important. Not all reports are created equal, so finding an audit partner who will deliver a high-quality report is essential.
Thorough, actionable reports
If the report you get from your auditor is too short, too vague, or otherwise deficient, you’ve wasted time and money. Ask your prospective auditor detailed questions about how they prepare audit reports. Curious what questions to ask? Download our Quality Audit Checklist. High-quality audit reports should not only confirm compliance but also highlight areas for improvement and risk mitigation strategies that are specific to your organization’s security posture.
Red flags to watch for
Be cautious of audit firms that provide overly brief reports or fail to offer constructive feedback. Cookie-cutter statements that could apply to any company could indicate insufficient investigation into your organization’s security processes and systems. Comprehensive reports that include thought leadership and best practices are indicative of a thorough and professional audit process.
Be sure to ask any potential auditors about their level of success and how often their reports are rejected by external vendors. Rejected reports are a red flag for report and auditor quality.
3. Breadth of services
An auditor with a wide breadth of services can help you combine audits, avoiding duplicate efforts later on. According to the 2025 Compliance Benchmark Report, 92% of companies pursue more than one certification or attestation, making it all the more important to choose an auditor that will grow with you and continue to meet your needs.
Multiple frameworks
Look for firms capable of handling a wide range of compliance standards and frameworks. Consider what certifications and assessments are common in your industry, and make sure your potential audit partner can handle those needs. Even if you only seek out one or two audits now, your auditor should be able to scale its services as your business evolves and grows — or new regulations emerge.
Cybersecurity and risk management
Outside of yearly audits, a full-service compliance partner should offer cybersecurity services like penetration testing and vulnerability assessment to help your organization mitigate risk year-round. Ask any prospective auditors how they can support and guide your organization on its journey to improve its overall security posture.
Related content: The Why Behind Compliance: Building a Culture of Security
4. Tech-enabled services
Choosing an auditor who embraces technology isn’t about flashy bells and whistles; it’s about efficiency. An auditor who does everything manually will take longer to finish your audit, and nobody wants to spend more time on an audit than they have to. Download the Quality Audit Checklist to learn what questions can help you understand a firm’s technology
Software and automation
Leverage auditors who use audit management software to streamline the audit process. This technology can simplify evidence collection and streamline communication between you and your auditor, limiting the time and resources needed to complete the audit. It also gives you a more transparent look at the process.
Integration with GRC tools
Choose auditors who can integrate with your existing compliance and trust management software, like Vanta, Drata, or AuditBoard. This integration can enhance the scalability and accessibility of your compliance program, making it easier to maintain high standards over time.
5. Audit process
Selecting a team that has wide-reaching experience and the appropriate certifications is essential, but so is alignment with the audit process. This portion of the process will take up time and resources, so be sure to understand scoping, the steps of the process, and how often you’ll be in touch with the team.
Experienced audit teams will have a clearly defined process to help you achieve your compliance goals. Here’s what to look for in a productive, manageable process:
- Timeline and scoping: There should be a clear timeline and scoping criteria established from the get-go. Be aware that the timeline will vary based on the framework, team availability, level of business complexity, and more.
- Synchronize audit cycles: Identifying overlaps and harmonizing audit cycles is a green flag for an effective audit partner. It takes knowledge and experience to define an audit synchronization opportunity, and those who see it will save you time and resources.
- Streamline the process: You shouldn’t feel like ripping your hair out during an audit cycle. The right partner will streamline the process with technology and other tools to ensure a seamless process with minimal disruptions.
- Team communication: The frequency and style of communication your audit partner brings to the table are high priority. Consider: are you looking for a partner to keep you up-to-date each day? Do you only want periodic updates? Think about what’s important to you and choose accordingly.
6. Reputation and references
A qualified auditor should be well respected by its customers and the industry at large. Avoid companies that cannot back up their supposed reputation with examples and metrics.
Client testimonials and references
Request references from similar companies to gauge the auditor’s reliability and effectiveness. Positive feedback from these references can provide valuable insights into the auditor’s performance and process.
Case studies and success stories
Review the auditor’s case studies, which should clearly demonstrate the auditor’s ability to deliver successful compliance outcomes. These stories can offer concrete examples of how the auditor has helped other organizations achieve their compliance goals.
Industry recognition
Choose auditors who are recognized and respected in the industry. Awards, publications, and active participation in industry forums are good indicators of a firm’s credibility and expertise.
How does A-LIGN stack up?
“I have extensive experience with auditors, and working with A-LIGN has been refreshing. I appreciate their approach, communication, proactive team, and how seamlessly audits are conducted with a no-surprises approach,” said Rashpal Singh, Global Director of Governance, Risk, and Compliance at Menlo Security.
Selecting the right compliance auditor can make a significant difference in maintaining a robust compliance program and building trust with your stakeholders. Combining experienced auditors and audit management technology, A-LIGN provides the widest breadth and depth of services including SOC 2, ISO 27001, HITRUST, FedRAMP, and PCI, among others.
A-LIGN prioritizes delivering best-in-class audits for our clients, providing tailored guidance, practical recommendations, and ongoing support to maintain a successful security posture. Our 96% client satisfaction rating speaks for itself.
Contact us to learn more about why A-LIGN is the leading provider of high-quality, efficient cybersecurity compliance programs.