On October 15, 2024, the Department of Defense (DoD) published the final 32 CFR rule for CMMC 2.0 in the federal register. The long-awaited rule outlines the requirements for defense contractors and subcontractors, defines the levels and assessment types, outlines responsibilities for CMMC third-party assessment organizations (C3PAOs), and sets the implementation timeline.
Now that the CMMC program rule is finalized, here are the key takeaways you need to know.
Notable updates on CMMC final rule
Draft versions of the CMMC rule have circulated for months, providing strong indicators of the direction of the program. But, as expected, there are a few notable changes and updates in the final rule.
Program timeline
CMMC began operating on December 16, 2024. In September 2025, 48 CFR was published in the Federal Register with an effective date of November 10, 2025. This marks the official start of Phase 1 of the CMMC roll out, meaning readiness is no longer optional and all new DoD solicitations and contracts include some level of CMMC requirement.
Organizations that get certified ahead of upcoming contractual requirements will be set to meet those requirements without delay. This is one of the many reasons we encourage organizations to get in the queue for certification as soon as possible.
External service provider applicability
The biggest difference between the proposed and final rule has to do with external service provider (ESP) certification. In earlier versions of the proposed rule, ESPs, such as managed service providers (MSPs) were required to obtain CMMC certification. Under the final rule, it is not required for ESPs to obtain their own certification.
However, it is still highly encouraged that ESPs should pursue CMMC certification. If ESPs decide to not pursue CMMC certification, then their assets will be in scope of their client’s assessments by a C3PAO. This means that ESPs could negatively impact their clients’ timelines by adding additional hurdles to review assets. Therefore, it is highly encouraged that ESPs get CMMC certified in order to streamline the process – which many of them were planning to do before the final rule was published.
Assessment staffing
The final rule includes an important update on staffing. The CyberAB, the accreditation body behind CMMC certification, has a program for training and certifying the individuals conducting CMMC assessments. There are two levels, certified CMMC professional (CCP) and certified CMMC assessor (CCA).
The CMMC final rule outlines that three CCAs must be involved in each assessment. Two CCAs will be required on the assessment team and one CCA will be a part of QA review.
This mandate for trained and certified professionals to conduct CMMC assessments will help to set a standard for excellence. However, it may create challenges for smaller C3PAOs with limited staff resources, resulting in longer wait times for assessments.
Requirements for CMMC level 2 compliance
The majority of organizations affected by CMMC will fall into level 2. The final rule defines the requirements for level 2:
- If you store, transmit, or process Controlled Unclassified Information (CUI), then you will need to obtain Level 2 Certification via assessment from a C3PAO
- Organizations Seeking Certification (OSCs) will need to implement the 110 practices outlined in NIST 800-171 and meet all 320 practice objectives
- While the DoD contract requirement rollout will begin likely in 2026, it is possible for primes to begin placing CMMC requirements to their subs before then
Get started with CMMC now
The window to prepare for CMMC compliance is closing, and organizations that proactively align with these standards now will have a competitive advantage.
Don’t wait until it’s too late. Start preparing for CMMC today. Strengthen your cybersecurity posture, secure future business opportunities, and ensure your place in a resilient supply chain that safeguards America’s security.
A-LIGN is a globally recognized cybersecurity and privacy compliance provider that offers a single-provider approach for organizations. With more than 1,000 federal assessments completed, A-LIGN is an accredited C3PAO and FedRAMP 3PAO with extensive experience across NIST frameworks.
Contact us today to secure your spot in line.
The European Union has introduced the NIS2 Directive—an evolution of its cybersecurity strategy to safeguard essential services and networks. Once the directive is transposed into law by the EU member states, the penalties for non-compliance will follow soon after. For businesses operating within the EU, understanding this directive is crucial for compliance and enhancing their cybersecurity posture.
This blog post will guide you through the intricacies of the NIS2 Directive, discussing who needs to comply, its purpose, coverage, requirements, and timeline. By the end, you’ll know how to prepare your organization for this pivotal shift in cybersecurity governance.
What is the NIS2 Directive?
The NIS2 Directive, a successor to the original NIS (Network and Information Systems) Directive, marks a significant step forward in the EU’s approach to cybersecurity. It aims to address the growing complexities and sophistication of cyber threats that can disrupt essential services. While the original NIS Directive laid the groundwork for cybersecurity measures across member states, NIS2 expands on these foundations, introducing more stringent requirements and a broader scope.
The directive establishes a harmonized framework for cybersecurity across the EU, covering 18 critical sectors. It aims to bolster the EU’s resilience against cyber threats. By enforcing higher cybersecurity standards, NIS2 seeks to protect critical infrastructures and sectors vital to modern society’s functioning. From energy and healthcare to transport and finance, the directive ensures that all essential services maintain robust cybersecurity practices to safeguard against potential disruptions.
NIS2 is not just about setting rules but about fostering a cybersecurity awareness and action culture. The directive encourages organizations to take proactive measures in identifying and mitigating cyber risks, ultimately leading to a more secure and resilient European digital landscape.
When and how will NIS2 be enforced?
The deadline for the NIS2 Directive to be transposed into national laws by all EU member states was originally established as 17 October 2024. As of May 2025, the European Commission issued formal warnings to 19 member states for failing to notify full transposition, giving them two months to comply or face potential referral to the Court of Justice of the European Union.
Once transposed, member states are responsible for enforcing the directive through designated national authorities, which must implement supervisory and enforcement measures, including penalties for non-compliance.
Who must comply with NIS2?
The NIS2 Directive casts a wide net, encompassing a broader range of sectors and entities than its predecessor. While the original NIS Directive focused primarily on operators of essential services (OES) such as energy, transport, and health, NIS2 extends its reach to include digital infrastructure providers, public administration entities, and other critical sectors.
Organizations that fall under the directive’s scope must comply with its requirements. This includes private and public entities providing essential services or operating critical infrastructure within the EU. Small and micro enterprises are generally excluded, unless they are deemed critical.
Organizations must assess whether they fall within the directive’s scope and understand their obligations. Compliance with NIS2 is not optional. Failure to adhere to its requirements can result in significant penalties and reputational damage. Therefore, organizations must proactively align cybersecurity practices with the directive’s mandates.
What is the purpose of NIS2?
The NIS2 Directive is designed to enhance the EU’s cybersecurity resilience and protect its digital landscape from evolving threats. The directive aims to ensure that essential services and critical infrastructure remain operational and secure, even in the face of cyber threats.
One of NIS2’s primary objectives is to foster a harmonized approach to cybersecurity across EU member states. The directive seeks to eliminate fragmentation and inconsistencies in cybersecurity measures by establishing common standards and practices, ensuring that all member states work collaboratively to address cyber risks.
Furthermore, NIS2 aims to enhance information sharing and cooperation between member states. This collaborative approach enables member states to pool their resources, expertise, and knowledge, strengthening the EU’s cybersecurity posture.
What does NIS2 cover?
The NIS2 Directive covers a wide range of sectors and entities. Its scope includes traditional critical infrastructure sectors, such as energy, transport, and healthcare, digital service providers, public administration entities, and manufacturing industries.
Within these sectors, the directive applies to organizations that provide essential services or operate critical infrastructure. This includes entities responsible for maintaining the security and availability of network and information systems that underpin these services.
The directive also emphasizes the importance of supply chain security. With cyber threats often exploiting vulnerabilities in the supply chain, NIS2 requires organizations to assess and mitigate risks associated with their third-party suppliers and service providers.
What are the NIS2 requirements?
The NIS2 Directive establishes requirements for organizations to achieve their objectives. These requirements cover various aspects of cybersecurity, including risk management, incident reporting, and governance.
Firstly, organizations are required to implement robust risk management practices to identify and mitigate cyber risks. This includes conducting regular risk assessments, implementing appropriate security measures, and continuously monitoring their network and information systems for potential threats.
Secondly, the directive mandates timely incident reporting. Organizations must issue the initial notification to the relevant national authorities within 24 hours, followed by an intermediate report within 72 hours and final report within one month. Timely incident reporting facilitates information sharing and collaboration between member states, enabling a coordinated response to cyber threats.
Lastly, NIS2 emphasizes the importance of cybersecurity governance. This includes appointing a designated person or team responsible for overseeing cybersecurity measures and ensuring compliance with the directive’s requirements.
What are the minimum measures for NIS2?
Beyond the key requirements, NIS2 mandates the following baseline security measures:
- Policies and procedures to assess the effectiveness of cybersecurity risk management measures
- Security in system acquisition, development and maintenance, including vulnerability handling and disclosure
- Risk analysis & Information system security
- Supply chain security
- Policies on appropriate use of cryptography and encryption
- Incident handling
- Basic computer hygiene and trainings
- Business Continuity measures (back-ups, DR, crisis management)
- HR security, access control policies and asset management
- Use of MFA or secured voice/ video/text comm & secured emergency communication
What are the penalties for non-compliance?
Failure to comply with NIS2 can result in financial penalties for an organization. The actual amount will be determined by each EU member state once they transpose the NIS2 Directive into local regulations.
However, the directive offers guidance ass to what those penalties should be. The dollar amount of fines will be based on an organization’s classification. Essential entities are large companies (250+ employees or €50M+) that operate in sectors of critical importance. Important entities are large companies operating in the other sectors or medium-size companies (50-249 employees or €10M-50M) operating in any of the sectors in scope.
For essential entities administrative fines can be up to €10,000,000 or at least 2% of the total annual worldwide turnover in the previous fiscal year of the company to which the essential entity belongs, whichever amount is higher.
For important entities, administrative fines can be up to €7,000,000 or at least 1.4% of the total annual worldwide turnover in the previous fiscal year of the company to which the critical entity belongs, whichever amount is higher.
Conclusion
The NIS2 Directive represents a significant advancement in the EU’s efforts to enhance cybersecurity resilience and protect critical infrastructures. The directive aims to create a safer and more secure digital landscape for all member states by establishing common standards, fostering collaboration, and addressing supply chain security.
For organizations, compliance with the regulations transposed from NIS2 is not just a legal obligation—it’s an opportunity to strengthen their cybersecurity posture and gain a competitive advantage. By implementing robust risk management practices, timely incident reporting, and effective governance frameworks, organizations can protect their operations, safeguard customer trust, and contribute to the overall cybersecurity resilience of the EU.
Organizations should consider engaging with cybersecurity experts like A-LIGN to stay ahead of evolving cyber threats and ensure compliance with the transposed regulations that will follow the NIS2 Directive. Reach out to our team today.
In an era where cybersecurity breaches are increasingly common, the demand for regulatory compliance has skyrocketed. To shed light on how businesses can effectively manage these demands, FTV Capital sat down with Scott Price, the Founder and CEO of A-LIGN—a leading provider of cybersecurity and compliance solutions.
Founded in 2009, A-LIGN was established to align companies’ strategic and compliance objectives, transforming how audits are conducted to save time and reduce costs. With a global presence and over 4,000 clients, A-LIGN offers streamlined services, including compliance assessments and cybersecurity testing.
Scott discussed the pivotal role of external investment from FTV in 2018, which provided financial support, market credibility, and growth opportunities. This partnership facilitated A-LIGN’s expansion and allowed Scott to enhance his leadership skills alongside a board of experienced professionals. Scott also emphasized the importance of innovation and leadership development at A-LIGN, highlighting their Leadership Academy, which fosters a culture of continuous improvement and innovation among employees.
With a commitment to quality, transparency, and continuous innovation, A-LIGN remains at the forefront of helping organizations build trust and confidence in a complex cybersecurity environment.
Read the article: https://ftvcapital.com/insights/a-lign-ceo-scott-price-on-delivering-mission-critical-cybersecurity-solutions-and-nurturing-a-leadership-culture/
According to the HITRUST 2024 #TrustReport, only 0.64% of organizations that received HITRUST certifications reported a security breach in their certified environments over 2022 and 2023. This statistic is a powerful testament to the robustness of the HITRUST framework and its unparalleled commitment to leading the industry in data protection standards.
With such a high success rate, it’s clear that HITRUST’s security assessments, including the new AI Risk Management Assessment, can play a critical role in safeguarding your organization’s AI initiatives. Are you assessing the risks associated with your AI tools before deploying them? Conducting due diligence is crucial to ensure that you have the necessary controls in place to mitigate risks.
Read our blog to learn how this framework ensures your business’s AI initiatives are secure, compliant, and aligned with industry best practices.
What is the HITRUST AI Risk Management (RM) Assessment?
The HITRUST AI Risk Management Assessment is a streamlined self-assessment designed to help organizations evaluate and manage the risks associated with AI.
This framework is built upon the National Institute of Standards and Technology (NIST) AI Risk Management Framework (RMF) and the ISO 23894 standard. HITRUST has consolidated the overlapping controls between these two standards into 51 key controls featured in the AI Risk Management Assessment.
One major advantage of the HITRUST AI Risk Management Assessment is its accessibility. Organizations do not need to be HITRUST-certified or even planning certification in the future to take advantage of this assessment.
Additionally, this framework is not restricted to the healthcare industry. Any company, regardless of the sector, can apply the assessment to measure AI-related risks.
Benefits of the HITRUST AI RM Assessment
The primary benefit of the HITRUST AI RM Assessment is that it offers a comprehensive yet simplified framework for managing AI-related risks.
Without this assessment, organizations would need to navigate hundreds of controls from both the NIST AI RMF and ISO 23247 standards. HITRUST significantly reduces this burden, saving security teams valuable time and resources.
By completing the HITRUST AI RM Assessment, organizations position themselves to meet emerging AI compliance regulations and requirements. This proactive approach ensures that your AI initiatives align with industry standards and best practices, providing your organization with a competitive advantage while saving time and effort in the future.
Moreover, the HITRUST AI RM Assessment helps organizations comply with specific directives outlined in frameworks such as ISO/IEC 42001 and the EU AI Act. These regulations mandate periodic AI risk assessments, and the HITRUST AI RM Assessment ensures your risk management practices are both comprehensive and in compliance with current and forthcoming international standards.
Who should use the HITRUST AI RM Assessment?
The HITRUST AI RM Assessment is suitable for a wide range of organizations. This self-assessment is not mandatory for companies that are HITRUST-certified and utilizing AI in their operations.
However, any business looking for valuable insights into the state of their AI development and usage would benefit from this assessment. It helps organizations identify areas for improvement and ensure they are maintaining compliance as both technology and regulations evolve.
Companies can choose to conduct the assessment internally or hire a trusted third-party auditor, such as A-LIGN, to ensure a thorough and objective evaluation. For organizations lacking internal expertise or resources, working with a trusted audit partner can be particularly valuable.
Achieving AI compliance with HITRUST
As AI adoption continues to grow, organizations are investing heavily in integrating AI technology into their daily operations. In 2024, businesses are projected to spend billions on AI initiatives, with adoption rates soaring across multiple sectors.
HITRUST’s anticipated AI certification, set to be released in November 2024, will further support organizations’ compliance efforts. By completing the AI risk management assessment now, businesses can position themselves for success and be well-prepared for upcoming certification requirements.
Contact us to learn more about how A-LIGN can help your organization complete a HITRUST AI Risk Management Assessment today.
The Digital Operational Resilience Act (DORA) represents a significant step in ensuring financial institutions and other organizations can withstand, recover, and adapt to cyber threats and technological disruptions.
Understanding the Digital Operational Resilience Act
The Digital Operational Resilience Act, or DORA, is a legislative framework introduced by the European Union that went live on January 17, 2025. It aims to enhance the operational resilience of financial institutions by establishing uniform requirements across EU member states. This regulation focuses on safeguarding the financial system from digital disruptions that could have widespread economic impacts.
DORA was developed in response to the growing reliance on digital services and the increasing frequency of cyber incidents affecting financial institutions. By harmonizing regulations, DORA seeks to create a more robust and consistent approach to managing operational risks. It emphasizes the importance of maintaining continuity of critical services even during disruptions.
Who needs to comply with DORA?
Compliance with DORA is mandatory for a wide range of financial entities operating within the European Union, including banks, insurance companies, investment firms, and other financial market participants like fintech companies and payment service providers. Additionally, third-party service providers that offer critical services to these institutions are subject to DORA’s requirements.
The purpose behind DORA
The primary goal of DORA is to safeguard the stability and integrity of the financial system by ensuring that financial institutions can withstand and recover from digital disruptions. This includes significant cyber-attacks, technological failures, and other operational challenges that could impact business continuity.
DORA aims to reduce discrepancies in how different EU member states address digital operational resilience by establishing a unified regulatory framework. This consistency enhances the financial sector’s overall security and minimizes the potential for systemic disruptions.
Another critical purpose of DORA is to foster consumer trust in the financial system. By ensuring that institutions are equipped to handle digital risks, DORA helps maintain the integrity and reliability of financial services, ultimately benefiting consumers and investors.
What DORA covers
DORA covers a comprehensive range of areas critical to enhancing operational resilience. These areas include risk management, incident reporting, testing and assessments, and governance of third-party service providers. DORA provides a holistic approach to managing digital operational risks by addressing these essential elements.
DORA’s central focus is risk management, requiring organizations to implement measures to identify, assess, and mitigate digital risks. This involves developing robust risk management frameworks and conducting regular risk assessments to identify vulnerabilities.
Incident reporting is another crucial aspect of DORA. Financial entities are required to report significant ICT-related incidents promptly to competent authorities (e.g. initial notification within 4 hours of classification). This facilitates timely responses to incidents and enables authorities to monitor and manage risks effectively.
DORA requirements explained
DORA sets forth specific requirements for financial institutions and third-party providers to achieve its objectives. Based on the published regulation, key requirements include:
1. ICT risk management framework: Comprehensive system for identifying, assessing, managing, and mitigating ICT risks.
2. Incident reporting: Processes for managing and reporting ICT-related incidents to authorities.
3. Digital operational resilience testing: Regular testing, including vulnerability assessments and penetration testing.
4. Third-party risk management: Managing risks from ICT third-party service providers.
5. Information sharing: Promoting cyber threat and incident information sharing among entities. DORA encourages organizations to voluntary participate in cyber threat intelligence sharing arrangements that can help enhance resilience across the financial sector.
6. Governance and accountability: Clear roles and senior management oversight for ICT risk management.
Preparing for DORA compliance
DORA was introduced in January 2023 and came into full effect on January 17, 2025, meaning organizations must now meet requirements for compliance or risk penalties. This involves conducting thorough assessments of existing systems and processes to identify gaps and areas for improvement. This assessment serves as the foundation for developing a comprehensive compliance strategy.
Organizations should prioritize the development of robust risk management frameworks that align with DORA’s requirements. This includes enhancing incident response capabilities, implementing effective governance structures, and ensuring continuous monitoring of digital risks.
Engaging with stakeholders across the organization is crucial for successful compliance. This includes fostering collaboration between IT, risk management, compliance, and other relevant functions to ensure a coordinated approach to achieving digital operational resilience.
Non-compliance with DORA may result in administrative penalties, including fines and corrective measures imposed by national competent authorities.
Conclusion
The Digital Operational Resilience Act represents a significant milestone in enhancing the resilience of financial institutions in the digital age. DORA aims to protect consumers, maintain economic stability, and foster trust in the financial system by establishing uniform requirements for managing digital risks.
For organizations subject to DORA, compliance efforts should be approached proactively and comprehensively. By prioritizing ICT risk management, incident response, and collaboration with third-party providers, organizations can achieve digital operational resilience and position themselves for success in an increasingly interconnected world.
The path to digital operational resilience may present challenges, but it also offers opportunities for growth and innovation. By embedding resilience into their operational strategies, organizations can thrive in digital disruptions and build a more robust, secure financial ecosystem.
Now that the Department of Defense (DoD) has published 48 CFR, CMMC is enforceable in all new DoD solicitations and contracts. This means that the time to act is now if you want to continue doing business with the DoD. Read on to explore why getting in the queue now is key to your organization’s CMMC success.
The urgency of CMMC 2.0 compliance
CMMC 2.0 is a non-negotiable requirement for all entities engaged with the DoD, including prime contractors and their subcontractors. Contractors must obtain CMMC certification under one of the three trust levels to demonstrate that they have adequately implemented cybersecurity measures. For organizations that fall into CMMC Levels 2 and 3, an audit is not just a recommendation — it is a necessity.
The stakes are high. Because CMMC certification will be required to continue working with the DoD, non-compliance could result in a catastrophic loss of business. Delaying action could jeopardize your organization’s ability to secure future contracts and maintain existing ones.
Why you shouldn’t wait to get in line for a CMMC 2.0 assessment
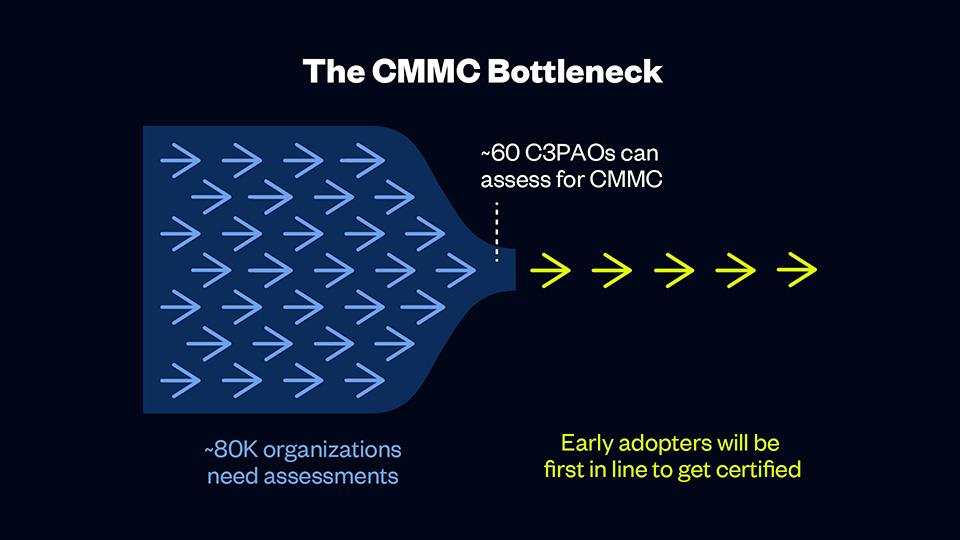
1. Bypass the mad dash to find an available C3PAO.
There are approximately 85 accredited CMMC Third Party Assessment Organizations (C3PAOs) available to assess the roughly 80,000 organizations that will need certification. As the demand for these assessments increases with the November 10, 2025 effective date for 48 CFR, it’s likely that C3PAOs will be overwhelmed with audit requests, creating long waitlists and potential delays. If you secure your spot in the assessment queue now, you can avoid the rush and ensure that your organization isn’t left scrambling to find an available assessor.
2. Pick the best assessor.
Choosing a high-quality assessor will increase the likelihood of a smooth certification process and ensures that your organization’s unique compliance needs are fully addressed. The right partner will have extensive expertise in federal compliance, provide a high-quality final report, and drive efficiencies across your team with technology to streamline the process. Getting started sooner rather than later allows your team to pick the highest-quality assessor. Plus, companies like A-LIGN can provide comprehensive support beyond just CMMC certification, acting as a single provider for all your compliance needs.
3. Lock in a favorable price.
As demand for CMMC assessments rises and the number of available assessors decreases, the ability to negotiate pricing will diminish. By getting ahead of the curve, you can lock in a competitive price for your assessment and avoid the financial strain of last-minute certification efforts.
4. Ensure complete CMMC readiness.
The process of preparing for a CMMC 2.0 audit is complex and time-consuming, potentially taking up to 12 months depending on the current state of your cybersecurity practices. Starting early gives you time to undergo a CMMC readiness assessment. This mock audit allows you to identify and remediate any gaps in your cybersecurity framework before the formal assessment, increasing the chances of passing on the first try.
5. Gain a competitive advantage.
Achieving CMMC 2.0 certification before your competitors not only secures your position within the DoD supply chain but also enhances your reputation as a reliable partner. Prime contractors will likely prioritize subcontractors who have already secured their certification, reducing project risks associated with non-compliance. Early certification can give you the upper hand in winning contracts and retaining existing business.
6. Avoid business disruption and contract losses.
Delaying your certification could lead to significant business disruptions, particularly as CMMC 2.0 becomes a contract requirement with 48 CFR. Prime contractors will begin demanding proof of compliance from their subcontractors, and failure to provide this could result in lost contracts or delays in renewals. Acting now minimizes the risk of these disruptions and ensures that your business remains competitive and compliant.
Get in the CMMC queue with a top federal assessor today
The transition to CMMC 2.0 marks a significant shift in the cybersecurity landscape for DoD contractors. Now that the final rule has been published, the time to act is now.
A-LIGN is here to guide you through the complexities of CMMC 2.0 compliance. As one of the first authorized C3PAOs with extensive experience in federal assessments, we can help you navigate the path to certification.
Contact us today to secure your spot in our CMMC certification queue and learn how we can support all your compliance needs.
The rapid growth of artificial intelligence (AI) has brought many privacy, ethical, and security concerns to the forefront of business operations. ISO/IEC 42001 is the world’s first AI management system standard created to address these concerns, providing the necessary guidelines to safeguard AI systems and ensure ethical AI practices. With many organizations new to the world of AI compliance, we developed an ISO 42001 checklist to help you evaluate your organization’s readiness for certification.
Download the ISO 42001 checklist
Why ISO 42001 and AI compliance matters
With the widespread adoption of AI across numerous industries, the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) developed ISO 42001 in 2023 to provide guidance to organizations providing, producing, or using AI systems.
Ensuring the ethical and secure deployment of AI solutions is critical, so ISO 42001 can be essential for organizations to ensure there are correct controls in place to safeguard sensitive data.
Achieving ISO 42001 certification and upholding the highest AI security practices can help your business demonstrate trust with key stakeholders, gain a competitive edge in the market, and foster a culture of security within your organization.
Understanding the ISO 42001 readiness checklist
Before you start your ISO 42001 compliance journey, it’s imperative you have a comprehensive understanding of the framework to adequately prepare for certification. From there, your security team can start to determine if the proper controls are in place to adhere to the standard and safeguard data.
Follow the ISO 42001 checklist below to demonstrate your dedication to AI compliance and prepare your team for certification.
Getting started with ISO 42001
The first step on the road to AI compliance is to adequately prepare your team by understanding the critical documents and policy requirements highlighted in the standard.
Understand the standard
Buy the standard(s) from ISO and understand each of the annexes needed to meet the object of the certification:
- Annex A: Serves as a control framework for meeting organizational objectives by addressing AI related risk
- Annex C: Highlights AI related risk sources
Understand critical documents
Gain a well-rounded understanding of the required documents outlined in the standard to build a responsible management system that aligns with your business goals.
- ISO 22989: AI Concepts and Terminology
- ISO 23894: AI Risk Management
- ISO 31000: Enterprise Risk Management
- ISO 42005: AI Impact Assessments
- ISO 5338: AI System Lifecycle Processes
- Others:
- ISO 24368: AI Overview of Ethical and Societal Concerns
- ISO 38500: Governance of IT
- ISO 38507: Governance Implications of the use of AI
Understand policy requirements
Ensure policies are fit for purpose and fit for use in the context of your specific organization and is applicable when needed.
Examples of policy categories include appropriateness, framework for objectives, documentation and accessibility, review and adaptation, and more.
Initial analysis and planning
Once your team understands critical documents and policy requirements, then you can perform an initial analysis of your management system and identify any gaps or corrective actions ahead of the external audit.
Perform a gap analysis
Via self-assessment, independent certification body, or compliance software tool, complete a gap assessment. Make sure to involve various department heads in the analysis to ensure comprehensive coverage.
Develop an implementation plan
Prioritize action items based on the gap analysis findings and assign responsibilities/deadlines for each action item.
Engage with an advisory or consultant partner to ensure your management system is built appropriately in the context of your organization.
Implement management system
Organize training sessions for employees on new processes and controls and set up a monitoring system to track the implementation progress.
Undergo internal audit
Train internal staff to perform audits or hire external auditors for an unbiased review ahead of the official certification.
Conduct management review
Document all management review meetings and decisions for audit purposes, including feedback mechanisms and staff insights on the AI management system.
Identify corrective actions
Develop a standardized form and tracking system for reporting and resolving non-conformities and corrective actions.
Ensure proper documentation
Create, review, and update a centralized repository for all ISO 42001-related documents to ensure ongoing compliance.
Engage with auditors for ISO 42001
Interview and engage a certification body that understands your context to assess and certify your management system so you can offer additional levels of assurance to your customers.
Choose a certification body
Evaluate multiple certification bodies to compare expertise, costs, and reputation and choose a quality audit partner that aligns their goals with yours.
Ensure certification body is compliant with their accreditation body and International Accreditation Forum (IAF) requirements. Check references from other companies certified by the body.
Hold pre-audit meeting
Prepare a list of questions and clarifications regarding the audit process and discuss the scope of the audit in detail to ensure full preparedness.
Ensure audit readiness
Conduct a pre-audit checklist review with the internal team responsible for ISO 42001 compliance. Simulate audit scenarios to prepare staff for the actual audit.
Undergo the external audit process
Designate a team member as the point of contact for auditors to streamline communication. From there, undergo assessment with interviews of key personnel and review of documentation.
Identify follow-up actions
Schedule a meeting to discuss audit findings and plan for immediate, short-term, and long-term actions based on the audit report with your internal team.
Ensure continuous improvement
Establish a continuous improvement team to oversee progress post-certification and integrate ISO 42001 compliance metrics into regular management reviews.
Partner with A-LIGN to achieve ISO 42001 compliance
Obtaining certification and upholding compliance with ISO 42001 is crucial for organizations leveraging AI. By utilizing this readiness checklist and collaborating with quality partner like A-LIGN, organizations can effectively navigate the standard, build brand reputation, and foster trust in your AI systems with key stakeholders.
Be one of the first to achieve ISO 42001 certification and set your team up for ISO 42001 certification success by downloading our readiness checklist now.
Establishing a solid foundation in information security is essential for leveraging artificial intelligence (AI) effectively. ISO/IEC 27001 provides the crucial framework for information security management and sets the groundwork for the new standard for AI, ISO/IEC 42001. By adhering to the principles of ISO 27001, organizations can create robust management systems that not only meet security standards but also pave the way for successful and secure AI implementation. This blog post will explore how ISO 27001 serves as the foundation for ISO 42001, offering a path to compliance.
1. Scope of ISO 27001 and ISO 42001
ISO 27001 focuses on information security management systems (ISMS). It provides a framework to protect sensitive information through risk management processes.
ISO 42001 deals with AI management systems. This standard includes responsibilities specific to AI, such as ethical considerations and impact assessments.
Work required
To align your organization with both standards, build upon your ISMS and create an AIMS. Integrate responsible AI practices to ensure comprehensive scope coverage.
2. Normative references in ISO 27001 and ISO 42001
ISO 27001 references various information security management standards. These guidelines help organizations maintain data integrity, confidentiality, and availability.
ISO 42001 incorporates AI-specific standards, like ISO/IEC 22989. These references focus on ethical AI use, risk management, and system integrity.
Work required
Integrate AI-specific normative references into your compliance framework. Ensure that your organization adheres to both information security and AI-specific standards.
3. Terms and definitions
ISO 27001 includes terms related to information security, such as risk, policy, and controls. These terms are essential for implementing a robust ISMS.
ISO 42001 introduces AI-specific terms, including AI risk, AI policy, and AI objectives. Understanding these terms is crucial for effective AI management.
Work required
Update your organization’s documentation and training materials to include AI-specific terms. This will help employees understand the nuances of both standards.
4. Context of the organization
ISO 27001 requires organizations to understand the context of their information security needs. This involves assessing internal and external factors affecting information security.
ISO 42001 extends this concept to AI. Organizations must understand the specific context of their AI systems, including stakeholder expectations and potential impacts.
Additionally, ISO 42001 requires organizations to understand their role in the AI ecosystem as provider, producer/developer, or user.
Work required
Analyze AI-specific issues and assess stakeholder needs. Document these findings to align with the requirements of both ISO 27001 and ISO 42001.
5. Leadership commitment
ISO 27001 emphasizes leadership commitment to information security policies. Top management must demonstrate their dedication to maintaining a secure environment.
ISO 42001 similarly requires leadership commitment but focuses on AI management. This includes defining roles and responsibilities specific to AI.
Work required
Ensure that your organization’s leadership demonstrates a commitment to both information security and AI policies. Assign roles to manage AI-specific responsibilities effectively.
6. Planning for risks and opportunities
ISO 27001 involves planning to address information security risks and opportunities. This includes risk assessments and treatment plans.
ISO 42001 extends these requirements to include AI risk assessment and impact evaluation. Organizations must identify and mitigate AI-specific risks.
Work required
Implement AI risk and impact assessment processes. Adapt your existing risk management frameworks to include AI-specific considerations.
7. Support resources and competence
ISO 27001 mandates the allocation of resources, competence, and awareness for information security. This ensures effective implementation and maintenance of the ISMS.
ISO 42001 requires similar support for AI management. Organizations must provide resources, training, and communication channels specific to AI.
Work required
Allocate resources for AI management and provide necessary training. Establish communication channels to facilitate information flow regarding AI policies and practices.
8. Operational planning and control
ISO 27001 focuses on operational planning and control for information security. Organizations must have processes in place to manage and monitor security controls.
ISO 42001 extends these requirements to AI systems. This includes planning and controlling AI operations, as well as conducting regular risk and impact assessments.
Work required
Develop operational controls specific to AI systems. Conduct regular assessments to ensure compliance with both ISO 27001 and ISO 42001.
9. Performance evaluation
ISO 27001 requires organizations to monitor, measure, analyze, and evaluate information security performance. This involves regular audits and reviews.
ISO 42001 similarly mandates performance evaluation but with a focus on AI systems. Organizations must establish specific metrics and criteria for AI performance.
Work required
Establish performance metrics for AI systems and conduct regular evaluations and audits. This will help you maintain compliance with both standards.
10. Continual improvement
ISO 27001 emphasizes continual improvement of the ISMS. Organizations must address nonconformities and implement corrective actions.
ISO 42001 also focuses on continual improvement but in the context of AI management. This includes addressing AI-specific nonconformities and applying corrective actions.
Work required
Implement processes for continual improvement of your AI management system. Address nonconformities and apply corrective actions to maintain compliance with ISO 42001 and ISO 27001.
Conclusion
Understanding the overlap between ISO 42001 and ISO 27001 can streamline your compliance efforts. By integrating AI-specific requirements into your existing information security framework, you can ensure comprehensive and efficient management of both systems.
By following the steps outlined in this blog, your organization can stay ahead of the curve with robust security and ethical AI practices. If you need further assistance, experts at A-LIGN can guide you through the compliance process.
The Why Behind Compliance: Building a Culture of Security
Brand reputation is everything in the digital age. Many consumers refuse to do business with brands they don’t trust. One of the sure-fire ways customer trust can be broken? Mishandling or inadequately protecting their data.
It’s no surprise then that corporate compliance teams have become critically important. They identify and mitigate risks for the organization, including risks with direct legal and financial consequences of noncompliance. Additionally, these teams can avoid or minimize the impact of security incidents, safeguarding the brand’s reputation.
Data from A-LIGN’s Compliance Benchmark Report shows that establishing customer trust and validating IT controls are increasingly important drivers of compliance programs. Rather than merely checking off the minimum regulatory requirements, companies are building a robust security-focused culture throughout the organization to stay relevant.
In this post, we’ll dig into the data from this year’s report and share how companies can adapt their compliance strategies in response.
What the data says about the “why” behind compliance
A-LIGN’s 2023 survey data showed pressure from above and on the bottom line when it came to the motivations behind compliance. One of the top reasons organizations pursue a cybersecurity audit was a board-level or C-suite mandate (23%), hinting that team members responsible for compliance saw it as a top-down order rather than an ongoing, continuous process within the organization. Another big driver of compliance in 2023 was increasing revenue and winning new clients (23%). This data points to a reactive approach toward compliance, with companies embarking on a new audit when an executive or prospective customer asks for one.
Beyond mandates: A focus on IT controls
In 2024, executive mandates and new business were the least popular responses to the question, “What is the driving force behind your organization’s compliance program?” On the other hand, the importance of establishing trust with customers and partners rose by 36% from the previous year. Additionally, 55% more companies stated that validating IT controls drove their compliance programs in 2024 compared to 2023.
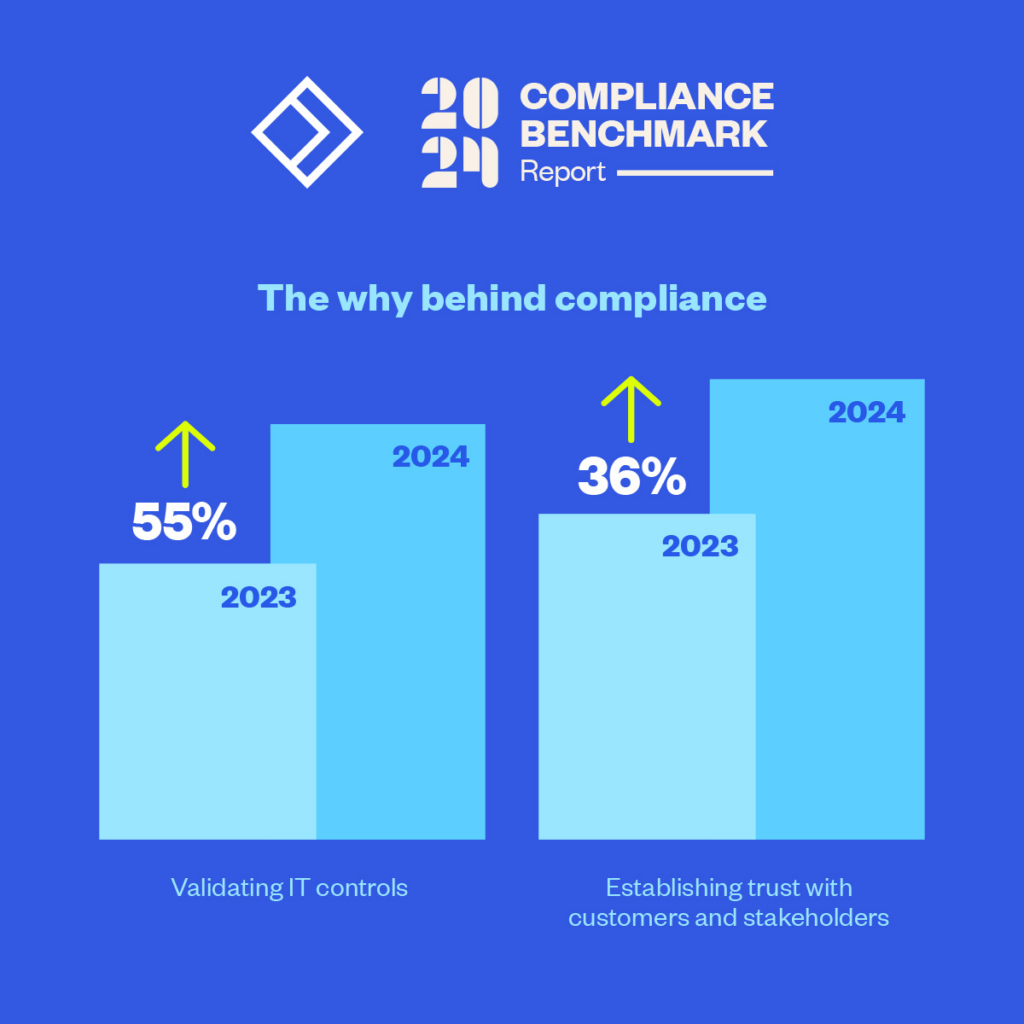
These findings indicate a growing emphasis on trust and security — and an overall maturation in how organizations approach security compliance. Instead of waiting for C-suite mandates to tell them what must be done, compliance teams are taking a more proactive and strategic stance that focuses on what can be done.
Why did this shift occur? As we covered at the beginning of this article, brand reputation is more important than ever. Proactively improving your security posture and publicly sharing your successes can bolster your brand reputation. It’s also possible that businesses have seen — or, worse, experienced themselves — the pitfalls of reactive compliance: lost business, security breaches, and expensive fixes.
How businesses can build a culture of security
As the importance of data security continues to rise, so too will the need for comprehensive and forward-thinking compliance programs. Businesses must prioritize transparency and robust security practices to maintain trust with stakeholders and ensure their internal controls are up to par.
Becoming more proactive toward compliance isn’t easy, but some tweaks to internal processes and attitudes can help get you there. Here are some ways your organization can take steps toward fostering a culture of security.
Regular audits and assessments
- Internal audits and continuous monitoring: Conduct regular internal audits to identify and address vulnerabilities before they come up in external assessments. These periodic internal audits, combined with continuous monitoring of your IT systems, will help you detect and mitigate issues promptly.
- Third-party assessments: Be proactive about engaging third-party auditors instead of waiting until a customer, executive, or investor asks for an audit report. You can also be more strategic about external audits by consolidating all your annual audits into a single compliance event.
A comprehensive compliance strategy
- Leadership commitment and internal collaboration: Leadership should prioritize security and compliance, as they set the tone for the entire organization. The leadership team can then encourage collaboration between IT, legal, compliance, and other departments to create a cohesive approach to security.
- Promote your compliance efforts: When you complete audits and certifications successfully, flaunt them! Celebrate the news internally, and display certifications prominently on your website and in marketing materials to build customer confidence.
Adapting to regulatory changes
- Stay informed: Keep up with changes in regulations, industry standards, and security best practices by subscribing to relevant industry newsletters. Check the websites of governing bodies, like the AICPA Auditing Standards Board (ASB) and the International Organization for Standardization (ISO), regularly for updates. Popular resources for security and compliance news include Infosecurity Magazine, SC Magazine, and Compliance Week.
- Practice agile compliance: Be prepared to adjust your compliance strategies quickly in response to new regulations or emerging threats. If your organization stays sufficiently informed about changes, you can use internal audits and continuous monitoring tools to identify potential gaps and adapt your controls and processes accordingly.
Get more insights in A-LIGN’s Compliance Benchmark Report
What does it really mean to build a culture of security? How many audits are companies doing, and what does that translate to in dollars? The 2024 edition of A-LIGN’s annual Compliance Benchmark Report includes insights like these, gathered from a survey of nearly 700 business leaders and compliance experts. It also offers benchmarks related to compliance audits, enabling companies to assess their existing strategies against industry standards.
See the highlights and download the full report here.