There are a number of steps that need to take place before an organization can embark on their ISO 27001 certification journey. Perhaps the most important is to determine which certification body to work with. A certification body (CB) is an organization that provides certifications around a chosen standard. They can either be an accredited CB or an unaccredited CB. Although there are admittedly minor differences between the two, the outcome of your ISO/IEC 27001 certification, and how you are able to leverage it, could vary drastically.
In this blog, we’ll explore the different certification bodies, and explain why choosing the right one matters.
What is ISO 27001?
ISO 27001 is a cybersecurity framework established by the International Organization for Standards (ISO), focused on building an information security management system (ISMS) within your organization. An ISMS helps organizations manage the security of all data, ranging from financial information to intellectual property (IP) or other confidential information.
ISO 27001, specifically, is a risk-driven standard that centers on data confidentiality, integrity and availability. Because it’s built around the process of monitoring and improving information security, its intent is to help organizations improve their approach to data security in a more holistic manner.
This is of particular importance for organizations looking to more efficiently reduce risk, optimize operations, and build a culture of information security. In fact, the standard also helps in implementing controls specific to an organization’s unique risks and assets, rather than applying general guidance in a one-size-fits-all approach.
Accredited certification body vs. unaccredited certification body
Accredited certification body
An accredited certification body (CB) must complete an extremely rigorous evaluation process through an accreditation body to ensure the certification audit it conducts is performed in accordance with the audit requirements. The evaluation process reviews the competence of the audit team, the audit methodology used by the certification body, and the quality control procedures in place to ensure both the audit and report are properly completed.
It’s worth noting organizations that use an accredited CB for certification will receive their ISO 27001 certifications with the accreditation body and IAF seal included. This illustrates that the certification body has an accreditation certificate and is accepted worldwide.
Unaccredited certification body
Unlike an accredited CB, an unaccredited CB is not audited to confirm their compliance with IAF certification audit requirements.
In some cases, it will be critically important for organizations to determine their clients’ expectations. If an organization is pursuing an ISO 27001 certification to meet a client need, they should also confirm if the client requires an accredited certificate or if they will accept a certificate from an unaccredited CB.
The ISO 27001 certification process is a detailed and intensive assessment that requires organizations to illustrate conformance to the standard across seven mandatory clauses and 114 Annex A controls. No organization wants to needlessly go through the process twice by working with an unaccredited CB when a certificate from an accredited CB is required.
ISO 27001 Certification bodies
Certification bodies are accredited to issue ISO/IEC 27001certificates. That said, there are many national accreditation bodies that provide accreditation to CBs for ISO 27001. Here is a deeper look into a few major players ANAB and UKAS.
ANAB
The ANSI National Accreditation Board (ANAB) is the largest accreditation body in North America, providing services to more than 75 countries. ANAB’s mission is to be a “leader in guiding the international development of accreditation processes that build confidence and value for stakeholders worldwide.” ANAB aims to do this by “providing high quality and reliable accreditation services with the most professional value-added services for customers and end users.”
Obtaining an ANAB accreditation for CBs has a number of benefits, including assurance of competence and reliability, and increased confidence from suppliers, partners and vendors. These result from the regular, impartial, and independent audits conducted by an internationally respected body.
UKAS
The United Kingdom Accreditation Service (UKAS) is the national accreditation body for the UK. Its mission is to instill trust and confidence in the products and services widely used each day.
The benefits for CBs obtaining UKAS accreditation is that UKAS demonstrates the competence, impartiality and performance capability of the evaluators. Basically, UKAS describes themselves as “checking the checkers,” essentially allowing certified organizations to establish a stronger sense of trust around data security with their customers.
Although there are many accreditation bodies located throughout the world, there is little difference among the primary three. This is because all accreditation bodies follow similar processes to identify CBs based on alignment with various checks-and-balances established by organizations like the IAF.
The IAF
The International Accreditation Forum (IAF) serves as the regulator for national accreditation bodies, including ANAB, RvA, and UKAS. Its primary function is to “develop a single worldwide program of conformity assessment which reduces risk for businesses and their customers by assuring them that accredited certificates and validation and verification statements may be relied upon.”
Basically, the IAF oversees the activities of the accreditation bodies to ensure they maintain the required standards when providing accreditation to CBs.
Most accreditation bodies are represented within the IAF and are committed to upholding the trust and validity of accreditation bodies in their efforts to provide certificates to CBs.
How certification bodies obtain and maintain accreditations
Certification bodies undergo a stringent process of annual office and witness audits. Many accreditation bodies will offer numerous training sessions for both individuals and organizations to not only stay educated on evolving standards, but to also maintain accreditations.
The ANAB, for example, offers a variety of training sessions focused on expanding knowledge of certain standards and mandatory documents.
Next steps
With an ISO 27001 certification, your organization can gain significant benefits, including building a culture of information security and diligence, and meeting additional security compliance requirements. And when you leverage an accredited certification body to help you achieve your ISO 27001 certification, your certification creates a stronger sense of trust and acceptance with customers worldwide.
A-LIGN is an ANAB accredited ISO/IEC 27001 certification body that helps organizations meet their ISO certification needs.
Get started by downloading our ISO 27001 checklist.
What Is HIPAA Compliance? Key Definitions + 7 Step Checklist
HIPAA (Health Insurance Portability and Accountability Act) is a federal law requiring organizations to keep patient data confidential and secure. If you are an organization that handles protected health information (PHI), a HIPAA compliance report will demonstrate you have the required safeguards in place to protect patient information.
There are three major components to HIPAA rules and regulations – the Security Rule, Privacy Rule, and Breach Notification Rule. This article will give background information on these three components and provide a checklist you can use when seeking HIPAA compliance.
What is HIPAA Compliance?
HIPAA compliance is a process for covered entities and business associates to protect and secure PHI in a way that complies with the established Privacy, Security, and Breach Notification Rules. Let’s review what information classifies as protected healthcare information and the professions bound by HIPAA regulations.
- PHI is protected healthcare information. This includes items such as paper documents, X-Rays, and prescription information. Electronic protected health information (ePHI) is PHI that includes digital medical records, electronic MRI scans, names, addresses, and dates (birthdays, hospital admission, discharge dates, etc.) stored or transmitted electronically.
- Covered entities are individuals and organizations working in healthcare who have access to PHI. These include doctors, surgeons, nurses, psychologists, dentists, chiropractors, hospitals, clinics, nursing homes, pharmacies, health plans, health insurance companies, HMOs, and company health plans. They frequently work with sensitive health information and are therefore bound by HIPAA regulations.
- Business associates are individuals and entities that perform activities involving the use or disclosure of protected health information on behalf of, or provide services to, a covered entity. This could include, but is not limited to, lawyers, accountants, administrators, and IT professionals.
Compliance with the HIPAA Security Rule
The HIPAA Security Rule requires covered entities accessing or handling ePHI to follow appropriate technical, physical, and administrative safeguards designed to keep the healthcare data confidential and secure.
- Technical Safeguards refers to the following:
- Access Controls. Only authorized persons may have access to ePHI.
- Audit Controls. Records of those accessing ePHI must be kept for auditing.
- Integrity Controls. Measures must be established to confirm ePHI has not been improperly altered or destroyed.
- Transmission Security. Security measures must be established to guard against unauthorized access to ePHI transmitted electronically.
- Physical Safeguards refers to the following:
- Facility Access and Control. Physical access to facilities must be limited to authorized personnel.
- Workstation and Device Security. Policies and procedures must be established specifying the proper use of and access to workstations and electronic media.
- Administrative Safeguards refers to the following:
- Security Management Process. Potential risks to ePHI must be identified and analyzed, and security measures implemented to reduce these risks.
- Security Personnel. The entity must appoint someone from the organization as the designated security official responsible for developing and implementing its security policies and procedures to assure compliance with the Security Rule.
- Information Access Management. Policies and procedures must be established authorizing access to ePHI only when necessary.
- Workforce Training and Management. Workforce members handling ePHI must be trained on security policies and procedures, supervised, and sanctioned when they violate these policies and procedures.
- Evaluation. Periodic assessment must be conducted to evaluate how well security policies and procedures meet the requirements of the Security Rule.
Compliance with the HIPAA Privacy Rule
The Privacy Rule addresses the use and disclosure of PHI by covered entities and outlines an individual’s privacy rights so they can understand their health information and control how it’s used. This rule covers all personal identifiers handled by a covered entity or its business associates in any media (electronic, paper, or spoken word).
With the exception of disclosure of PHI for treatment, payment, or healthcare operations, complying with the Privacy Rule means that PHI is only disclosed when authorization is given by the patient, patient’s legal representative, or decedents, or:
- When required by law
- When in the patient’s or the public’s interest
- To a third-party HIPAA covered entity where a relationship exists between that party
Additionally, the Privacy Rule limits disclosure of PHI to the minimum necessary for the stated purpose.
Compliance with the Breach Notification Rule
The HIPAA Breach Notification Rule requires covered entities and their business associates to provide notification following a breach, or the impermissible use or disclosure of PHI. Patients and the Department of Health and Human Services must be notified of breaches, as well as the media if the breach affects more than 500 patients. Notification must be reasonably prompt and no later than 60 days following discovery of the breach.
Breaches affecting fewer than 500 individuals must be reported to the Office for Civil Rights (OCR) web portal on an annual basis. Breach notifications should include:
- The nature of the PHI and the types of personal identifiers exposed
- The unauthorized person who accessed or used the PHI or, if known, to whom the disclosure was made
- Whether the PHI was acquired or viewed (if known)
- The extent to which the damage or risk of damage has been mitigated
HIPAA Compliance Checklist
Covered entities and business associates can use the following as a guide to help establish or remain in HIPAA compliance.
- Identify gaps in audits and document deficiencies through a HIPAA gap analysis
- Create and document remediation plans to address deficiencies found in audits
- Update and review these remediation plans annually
- Retain records of documented remediation plans for six years
- Ensure staff completes HIPAA training
- Document their training
- Designate a staff member to be the HIPAA Compliance, Privacy, and/or Security Officer
- Maintain policies and procedures relevant to the annual HIPAA Privacy, Security, and Breach Notification Rules
- Ensure staff reads and legally attests to the policies and procedures
- Maintain documentation of their legal attestation
- Maintain documentation for annual reviews of the policies and procedures
- Identify vendors and business associates who may handle PHI
- Establish agreements with all business associates
- Assess the HIPAA compliance of business associates
- Track and review business associate agreements annually
- Sign confidentiality agreements with non-business associate vendors
- Define a process for incidents and breaches
- Ensure you can track and manage the investigations of all incidents
- Ensure you can provide the required reporting of all breaches or incidents
- Ensure staff members can report incidents anonymously
A-LIGN Specializes in HIPAA Compliance
The fines for HIPAA violations are imposed per violation category and can be severe, reaching up to $1,500,000 per violation category, per calendar year. Authorities can even file criminal charges in the case of willful neglect.
To ensure your organization remains in good standing, it’s often best to have professional assistance. With over 850 healthcare assessments completed, A-LIGN helps organizations achieve HIPAA compliance from readiness to report. Click to explore our HIPAA services.
Download our HIPAA checklist now!
On February 15, 2022, the International Organization for Standardization (ISO) released an update to ISO/IEC (International Electrotechnical Commission) 27002:2013 under the name ISO/IEC 27002:2022. The release of this new standard has caused a lot of confusion and anxiety within companies, with many under the mistaken impression that they’ll have to undergo a new certification process in order to achieve compliance. This, however, is not true.
In this blog, I’ll shed light on the new standard and explain what ISO 27002:2022 means for your business.
What Is ISO 27002?
Let’s start by clarifying that ISO 27002 should be viewed as more of a manual as it offers extensive guidance on the Annex A controls and best practices an organization should implement to ensure the confidentiality, integrity, and availability (CIA) of assets.
ISO 27001, on the other hand, actually establishes the compliance requirements needed to become certified. This clarification is important, primarily because ISO 27001 has not been updated yet, only its supplemental guidebook ISO 27002 has changed. This is, however, a great time for organizations to implement the best practices found in the revamped guidebook as we expect ISO 27001 will also be updated fairly soon.
Why Was ISO 27002 Updated?
Updates to ISO standards occur periodically. ISO/IEC 27002 has origins that trace back to a 1990’s UK government initiative. It was first a standard developed by the oil company Shell Energy that was donated to the UK and became a British standard in the mid-1990s ISO 27002 was adopted as an ISO standard in the year 2000 and seems to undergo revisions on an eight/nine-year cycle with official updates to ISO 27002 occurring in 2005, 2013, and now in 2022.
This most recent update reimagines the terminology and format of ISO 27002 to make it easier for the layperson to understand. There’s also more focus on cybersecurity and privacy, better aligning the controls to the modern digital era.
What Are the Major Changes?
While ISO 27002:2022 is an exhaustive guide with numerous changes, there are six changes in particular of which organizations should be aware.
1. Reduced Total Controls
There were previously 114 internal controls listed in ISO 27002:2013. Now, 57 of the controls have been consolidated, leaving just 24 controls to eliminate redundancies. It’s worth noting that while the number of controls has decreased, no controls were excluded, only merged for simplicity. And with the addition of some new controls, the total number now stands at 93.
2. 11 New Controls
The 93 total controls include 11 brand new controls that address:
- Information security for use of cloud services
- ICT readiness for business continuity
- Physical security monitoring
- Configuration management
- Information deletion
- Data masking
- Data leakage prevention
- Monitoring activities
- Web filtering
- Secure coding
- Threat Intelligence
3. Domains Have Become Categories
Say goodbye to confusing domains and hello to categories. Now, instead of 14 domains, each of the internal controls fall under one or more of the following four categories:
- Organization
- People
- Physical
- Technological
4. “Objectives” Have Become “Purpose”
Don’t expect to find the word “objective” as you would have in previous versions of the standard. Instead, you’ll find each of the controls have an intended “purpose.” This new framing was done intentionally to help organizations better understand the point of the control and its impact on your assets.
5. New Attributes Tables
ISO created a table of attributes that correspond with each control. The five categories of attributes are as followed:
Control type
What type of effect does the control have?
Preventive, Detective, or Corrective
Information security properties
Which part(s) of the CIA triangle does the control touch?
Confidentiality, Integrity, or Availability
Cybersecurity concepts
What type of cybersecurity action will be taken?
Identify, Protect, Detect, Respond, or Recover
Operational capabilities
Which of the following security specialization(s) does the control belong to?
Governance, Asset management, Information protection, Human resource security, Physical security, System and network security, Application security, Secure configuration, Identity and access management, Threat and vulnerability management, Continuity, Supplier relationships security, Legal and compliance, Information security event management, and Information security assurance
Security domains
Which information security field is involved?
Governance and ecosystem, Protection, Defense, or Resilience
6. Two New Annexes
Although there’s been a lot of consolidations, additions, and renaming of controls, ISO has made it easy to map the controls back to the 2013 version. With Annex B, users can find a 2022 control and then see with which 2013 control it corresponds. The reverse is true with Annex A, which allows users to first select a 2013 control and find the 2022 control with which it corresponds.
Get Ready for Certification
Although no action needs to be taken today, the updates to ISO 27002:2022 present a great opportunity for organizations to start reviewing and updating their internal controls. Doing so now, ahead of the anticipated ISO 27001 update, will enable organizations to more efficiently implement best practices to achieve compliance in the future. Certification bodies will require a shift once ISO 27001 has been updated but as always, being prepared is key to cybersecurity compliance success!
To expand your knowledge on how to achieve compliance, check out what it takes to get certified in 5 Steps to ISO Certification.
Understanding Federal Supply Chain Risk Management
Federal supply chain risk management remains a critical focus as cyber-enabled supply chain attacks continue to evolve in sophistication and frequency. These threats, often used as tools of hybrid warfare, pose significant risks to national security. While the principles of supply chain risk management (SCRM), cyber SCRM (C-SCRM), and federal SCRM share common ground, federal SCRM carries heightened stakes due to its direct implications for the security and resilience of the United States.
To grasp the ongoing efforts to strengthen federal supply chain risk management, it’s essential to first understand how supply chain risk management is defined within the broader context of cybersecurity.
What is cyber supply chain risk management?
Cyber supply chain risk management (C-SCRM) is the continuous process of identifying, evaluating, and mitigating risks associated with an organization’s IT and software supply chains. It’s a critical, organization-wide effort that extends beyond the IT department, embedding security into the entire risk management framework to protect essential systems and data.
C-SCRM best practices
The National Institute of Standards and Technology (NIST) provides foundational guidance for C-SCRM. To build a resilient program, organizations should prioritize integrating C-SCRM across all business functions, establishing a formal and dynamic program, and deeply understanding their critical suppliers. Collaboration, continuous monitoring, and comprehensive resilience planning are also essential components of a strong C-SCRM posture.
Maintaining trustful and transparent relationships with suppliers is crucial, as your security is only as strong as its weakest link. Breaches originating from third parties, and even “fourth parties” (your vendors’ vendors), can dramatically increase the cost and impact of a security incident.
Strategies for effective C-SCRM
To navigate today’s complex threat landscape, organizations must adopt more advanced and proactive strategies.
- Adopt a zero-trust mentality: Operate under the assumption that a breach is inevitable. A zero-trust architecture requires strict verification for every user and device trying to access resources on your network, regardless of whether they are inside or outside the network perimeter.
- Leverage AI and automation: Use artificial intelligence and automation to enhance continuous monitoring. These technologies can analyze vast amounts of data to detect anomalies, predict potential threats, and automate responses, allowing for faster and more effective risk mitigation.
- Enhance vendor risk management: Go beyond initial security questionnaires. Clearly define security requirements in all contracts and RFPs, and demand evidence of compliance, such as penetration test reports or security certifications. Implement continuous monitoring to ensure vendors maintain their security controls over time.
- Create a comprehensive asset inventory: You cannot protect what you do not know you have. Maintain a thorough inventory of all assets — including hardware, software, data, and personnel — and map out where they interact with third parties to identify potential points of failure.
What is federal supply chain risk management?
Federal SCRM is the process of mitigating risks within the supply chain that could impact national security. While historically focused on the Department of Defense (DoD) and the Defense Industrial Base (DIB), the scope of federal SCRM has expanded.
This expansion is a direct response to the increasing sophistication of our nation’s adversaries. These actors exploit supply chain vulnerabilities to infiltrate systems, steal intellectual property, corrupt software, and surveil critical infrastructure, posing a direct threat to U.S. security.
Key frameworks: NIST 800-171 and CMMC
To counter these threats, the U.S. government has established specific cybersecurity standards. The National Institute of Standards and Technology (NIST) 800-171 provides a set of security controls for protecting Controlled Unclassified Information (CUI) in nonfederal systems. Federal contractors and subcontractors handling CUI must implement these controls to safeguard sensitive data.
Building on this foundation, the Cybersecurity Maturity Model Certification (CMMC) program was created to verify that contractors have the necessary protections in place. The self-attestation approach under the old DFARS Interim Rule proved insufficient, leading to the development of CMMC as a more robust verification method.
CMMC 2.0: The future of federal supply chain risk management
The Cybersecurity Maturity Model Certification (CMMC) is a framework designed to safeguard Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) within the Defense Industrial Base (DIB). With the release of CMMC 2.0 in October 2024, the framework has been streamlined into three levels of compliance, each tailored to the sensitivity of the information being handled:
- Level 1 (Foundational): Focuses on basic cybersecurity practices for organizations handling FCI. Compliance is demonstrated through annual self-assessments.
- Level 2 (Advanced): Designed for organizations managing CUI, this level aligns with the 110 practices outlined in NIST SP 800-171. Critical CUI handlers require third-party assessments every three years.
- Level 3 (Expert): Reserved for the most sensitive programs, this level incorporates additional requirements from NIST SP 800-172 and mandates direct assessments by the Department of Defense (DoD).
The publication of the 48 CFR rule has solidified the implementation of CMMC 2.0, outlining a phased rollout for mandatory compliance in new DoD contracts. However, it is crucial to note that contracting officers have the discretion to include CMMC requirements in their contracts ahead of this schedule. Some organizations are already seeing these requirements appear in Requests for Proposals (RFPs).
The official phased rollout is structured as follows:
- Phase 1 (Starts November 10, 2025): For the first 12 months after the rule’s effective date, Level 1 and Level 2 self-assessment requirements may be included in applicable solicitations and contracts as a condition of award.
- Phase 2 (Starts November 10, 2026): Over the next 12 months, Level 2 third-party assessment requirements (C3PAO Certification) will be widely introduced in solicitations and contracts as a condition of award.
- Phase 3 (Starts November 10, 2027): In this phase, Level 2 C3PAO Certification becomes a requirement for all applicable solicitations and contracts, including the exercising of option periods. Level 3 government-led (DIBCAC) assessment requirements will also be introduced.
- Phase 4 (Starts November 10, 2028): This marks the full implementation of all CMMC requirements (Level 1, 2, or 3) across all applicable DoD solicitations and contracts, including option periods.
This shift underscores the DoD’s commitment to mitigating supply chain risks and enhancing the resilience of federal supply chains. Organizations within the DIB must now be prepared to demonstrate their cybersecurity posture through either independent validation or self-assessment, depending on their assigned CMMC level.
How to prepare for CMMC certification
- Determine your organization’s CMMC level. Level 1 is for contractors and subcontractors processing FCI. Level 2 is for organizations processing CUI. Only organizations working on the DoD’s most sensitive programs will be expected to achieve Level 3 certification.
- Review the assessment guide for your CMMC level. The CMMC Level 1 Self-Assessment Guide and Level 2 Assessment Guide explain how contractors will be evaluated. Unfortunately, there is not yet an assessment guide for CMMC Level 3.
- Work with a tech-enabled organization to secure your data. Cybersecurity solutions like Summit7, Radicl, and CyberSheath can help you secure your FCI and CUI to prepare for CMMC compliance.
- Select a C3PAO and complete a readiness assessment. With a limited number of C3PAOs, it is important to start validating your organization’s readiness as soon as possible, as you will need time to remediate any gaps found.
- Engage a C3PAO for Level 2 Certification early. If your organization requires a CMMC Level 2 certification, engaging a C3PAO is a critical step. These assessors are already in high demand, and their schedules are filling up quickly. Waiting until the CMMC requirement appears in contracts will likely be too late, as you may face significant delays in finding an available C3PAO to conduct your assessment.
Work with a top federal assessor
Federal SCRM is no longer a future concern—it’s a present-day necessity. As the volume and sophistication of global cyberattacks rise, organizations are under increasing pressure to enhance their defenses and gain clear visibility into their supply chains. Third-party risk remains a significant threat, as many businesses unknowingly collaborate with vendors who have inadequate cybersecurity measures, creating vulnerabilities that can be exploited.
Navigating the complexities of federal compliance requires expertise. Whether you need guidance through the NIST 800-171 assessment process or assistance preparing for your CMMC certification, A-LIGN can help you take the most efficient path to compliance. As an authorized C3PAO with over 1,000 successful federal assessments completed, our team has the experience to help you strengthen your security posture and meet government requirements.
What Is Death Master File Certification?
Since late 2016, organizations have faced a stricter certification process to be granted access to the Death Master File (DMF), a computer database created by the United States’ Social Security Administration from 1962 to present day. The DMF is a protected file that includes information regarding the deceased such as their name, date of birth, date of death, social security number, last known zip code, if their death certification was observed, and other personal identifiable information (PII). For organizations who need to access to the PII of deceased individuals, they will need to certify with the DMF. Generally, in the three-year period following an individual’s death, sensitive information is unable to be released.
There are many challenges organizations can face when seeking DMF certification. Let’s review the certification process, what your organization should prepare for, and the standards against which you can certify.
What is the DMF certification process?
To access the DMF, an individual or entity must have a legitimate fraud prevention interest or have a legitimate business purpose to a law, government rule, regulation, or fiduciary duty. If an organization qualifies for DMF certification, they will be required to follow the steps below during their assessment process.
Step 1: Testing is conducted against SOC 2 or NIST 800 series standards.
Step 2: Organizations must go to the National Technical Information Service (NTIS) website to pay the required fees and will receive a processing number. Please note, these fees are in addition to those paid to the Accredited Conformity Assessment Body (ACAB) for attestation.
Step 3: Organizations must obtain the FM100A attestation form from the NTIS website and provide your auditing firm with the processing number to complete the attestation.
Step 4: Your auditor files the attestation documentation with NTIS. Your auditor will notify you that your form has been submitted and reaches out only if an issue arises. If all information is correct, NTIS communicates directly with your organization on approval/certification status.
What should my organization prepare for?
Once you achieve DMF certification, it doesn’t stop there. Your organization will need to be prepared for recertifications, unscheduled audits and more. Below is a list of what you can expect in the next several years following your initial DMF certification.
- Annual recertification by the organization seeking access
- Third-party conformity attestation every three years
- Agreement to scheduled and unscheduled audits, conducted by National Technical Information Service (NTIS) or the ACAB at the request of NTIS
- Fines up to $250,000 per year for noncompliance
The entity wishing to access the DMF must submit written attestation from an ACAB to prove that the appropriate systems, facilities and procedures are in place to safeguard information and maintain the confidentiality, security, and appropriate use of the information.
Subscriber certification must be completed annually. The LADMF Systems Safeguards Attestation Form must be completed every three years.
The U.S. Department of Commerce’s National Technical Information Service (NTIS), the governing body behind the DMF, can conduct both scheduled and unscheduled compliance audits and fine organizations up to $250,000 for noncompliance, with even higher penalties for willful violations. Due to the potential for substantial fines, it is important that entities be able to implement the appropriate systems’ facilities and procedures to safeguard the information.
What standards can organizations certify against?
Organizations can achieve certification by testing against standards such as SOC 2, and NIST 800 series publications.
What is SOC 2?
SOC 2 is a reporting standard that provides clients assurance regarding a service organization’s controls that do not affect the clients’ internal controls over financial reporting. This report is intended for use by stakeholders (customers, regulators, business partners, suppliers, directors) of the service organization to have a thorough understanding of the service organization and its internal controls.
What is NIST 800-53?
Published by the National Institute of Standards and Technology (NIST), NIST 800-53 covers the steps in the Risk Management Framework (RMF) that address security control selection for federal information systems in accordance with the security requirements in the Federal Information Processing Standard (FIPS) 200.
Helping You Achieve DMF Certification
A-LIGN is an ACAB that can attest to organizations’ systems and procedures in place. A-LIGN utilizes various published information security standards, mainly the AICPA SOC 2, to satisfy the rule’s audit requirements.
Since 2015, A-LIGN has been working to help our clients meet their DMF audit requirements and has successfully submitted the appropriate attestation forms to NTIS, resulting in certification for our clients. We have extensive experience testing the controls required by LADMF and can guide your organization through the certification process with ease.
FedRAMP FAQ – Understanding FedRAMP 2022
Any organization seeking to provide cloud products or solutions to a federal agency will need to go through a FedRAMP Readiness Assessment and then a full FedRAMP assessment to receive an Authorization to Operate (ATO) which ensures the security of its hosted information meets FedRAMP requirements. The Federal Risk and Authorization Management Program (FedRAMP) is a government-developed standardized approach to security assessment, authorization, and continuous monitoring of Cloud Service Providers (CSPs). Only Third Party Assessment Organizations (3PAO) may perform FedRAMP assessments.
Rather than needing multiple assessments, FedRAMP is an integrative standardized audit designed to be a common one-stop-shop for CSPs. FedRAMP follows the “do once, use many” methodology. FedRAMP’s myriad of benefits includes efficiency of resources, both cost effective and time-saving.
The goal of FedRAMP is to increase confidence in the security of cloud solutions through continuous monitoring and consistent use of best information security practices and procedures.
As organizations explore their federal audit options, A-LIGN’s experienced assessors have compiled and answered five frequently asked questions to help organizations better understand the assessment process.
1. Does FedRAMP apply to me?
Any Cloud Service Provider (CSP) that is currently or looking to become a third-party vendor for federal agencies must become FedRAMP certified. State government agencies may also require third-party CSPs to become FedRAMP certified. There is also the StateRAMP program for CSPs working with State governments.
2. Do CSPs need an agency sponsor to become FedRAMP certified?
Yes, there are two processes in which CSPs can become FedRAMP certified. The first is through an agency sponsorship when a government entity vouches for a CSP streamlining their approval process. The other option is for CSPs to go through the Joint Authorization Board (JAB) that includes a readiness assessment which reviews controls and upon passing provides joint provisional security authorization.
3. What are the key processes of FedRAMP?
The key processes of FedRAMP include a security assessment, leveraging and authorization, and ongoing assessment and authorization. The security assessment involves a set of requirements from the NIST 800-53 Rev. 4* controls to test security authorizations. In the FedRAMP repository, federal agencies view security authorization packages and leverage these packages to grant authorization. Once granted, continuous assessment and authorization, or continuous monitoring, activities must be in place to uphold authorization.
*FedRAMP will be transitioning to NIST SP 800-53 Rev. 5.
4. Is penetration testing mandatory for a FedRAMP ATO?
Yes, a penetration test is a mandatory part of the assessment process if the CSP is moderate or high-risk level impact. Third-Party Assessment Organization (3PAO) must perform mandated penetration testing.
5. How do I start the process of becoming FedRAMP certified?
The process is dependent on an organization’s current level of compliance with NIST SP 800-53 Rev. 4. If an organization has never written a System Security Plan (SSP), evaluating current security controls against the controls in the NIST SP 800-53 Rev. 4 is recommended.
Becoming FedRAMP Compliant
If you are a Cloud Service Provider (CSP) currently providing, or seeking to provide, services to federal agencies, A-LIGN can make your FedRAMP process seamless. We will support you during your entire FedRAMP journey, from readiness to authorization.
You may have noticed the United States’ Federal Risk and Authorization Management Program (FedRAMP) is now gaining traction in other parts of the world. It begs the question, “Does my business need a FedRAMP assessment?”
FedRAMP was originally launched in 2011 as a way for the U.S. government to manage security risks as they adopt products and services that store, process, and transmit federal information in the cloud. Although FedRAMP is usually leveraged as a way for cloud service providers (CSPs) to meet Federal Information Security Modernization Act (FISMA) requirements, a growing number of organizations are using this risk-based standard to not only enhance their security, but to also stand out from the competition and win new business.
Let’s take a look at why a European business would want to pursue FedRAMP authorization and the many benefits to their organisation.
Why would a European business pursue FedRAMP Authorization?
There’s one main factor that most often motivates European businesses to pursue FedRAMP Authorization to Operate (ATO) status: They would like to sell a cloud service offering (CSO) to the U.S. government.
FedRAMP was specifically designed to ensure that CSPs with a software as a service (SaaS), platform as a service (PaaS), or infrastructure as a service (IaaS) CSO have adequate information security to do business with a U.S. federal agency. The specific requirements that a CSO must fulfil are dictated by FISMA and its subsequent memorandums.
In other words: If your business is a CSP that would like to sell a cloud-based solution to the U.S. government, you must obtain FedRAMP. Bonus- FedRAMP’s “do once, use many approach” means that when you achieve FedRAMP ATO status, your security package can be reused by any federal agency. You will also be listed in the FedRAMP Marketplace, which is often the first place federal agencies look when sourcing a new CSO.
What are the benefits of FedRAMP for European businesses?
Before we dive into the benefits, it’s worth noting that FedRAMP is not a quick and easy process that your business can sail through without much effort. It is a serious undertaking that requires patience as you work to fill your existing security gaps.
That being said, achieving FedRAMP ATO status comes with several advantages that make the effort required more than worth it. Here are a few to consider:
- The ability to re-use FedRAMP across multiple U.S. government agencies
- More robust security and risk mitigation for your CSO
- Enhanced real-time security visibility
- Improved trust among customers, prospects, and partners
- A marketing proof point that can be used in the private sector
Additionally, the new FedRAMP control baselines using NIST 800-53 Rev 5v uses an evolving, threat-based approach that allows CSPs to keep their information security efforts up to date against new and emerging threats.
How can my business get started with FedRAMP?
There are two options to choose from when looking to authorize a CSO through FedRAMP: a Joint Authorization Board (JAB) provisional authorization (P-ATO) or an ATO issued by an individual U.S. government agency. For more guidance on selecting your authorization strategy, I highly recommend reading through the FedRAMP CSP Authorization Playbook.
Below are the four high-level steps involved in the FedRAMP authorization process:
1. Document
Your business must categorize the CSO being considered for FedRAMP in accordance with NIST FIPS-199. The category (Low, Moderate, or High impact) that applies to your CSO depends on how much harm would be caused by a security breach. See our guide Understanding Federal Compliance for more details about these impact levels.
2. Assess
A federally-accredited third-party assessment organization (3PAO) conducts a security assessment to determine if your CSO meets the baseline controls required for FedRAMP. If they do meet the baseline controls, the 3PAO will submit an assessment package attesting to your compliance.
3. Authorize
The government agency will review the security package and either approve to organization as FedRAMP authorized or request additional testing. A final review is then conducted by the government agency and FedRAMP Program Management Office (PMO) to decide if they will accept the risk associated with the use of the CSO. If approved and accepted, Authorizing Officials will issue an ATO letter.
*For the P-ATO route, this review process will also include the FedRAMP JAB.
4. Continuously monitor
After authorization is granted, you must provide monthly deliverables to the agency (or agencies) using your CSO to demonstrate that your cloud security controls are continuing to operate effectively. You must also have a 3PAO complete an annual security assessment to ensure the system’s risk posture remains acceptable.
Work with a top FedRAMP assessor
While FedRAMP was created to assist the U.S. government to rapidly, rigorously, and consistently assess the security of cloud solutions, it also benefits CSPs. From earning more U.S. federal work to increasing trust among customers and prospects in the private sector, there are several reasons why your European business may want to pursue FedRAMP authorization.
Looking to firm up your plan for FedRAMP? As an accredited 3PAO that is one of the top five FedRAMP assessors in the world, A-LIGN is ready to perform your security assessment. In fact, we are currently a FedRAMP 3PAO for a growing number of European CSPs. If you have already chosen a 3PAO, but could use some guidance throughout the preparation process, our independent team of advisors can help you with control implementation, process documentation, and everything in between. Learn more about our comprehensive FedRAMP services.
As more customers ask for demonstrated SOC 2 compliance, independent cybersecurity control validation and attestation are becoming necessary to compete for high-priority contracts. Beyond customer demand, SOC 2 reports ensure that controls are properly implemented and used within your organization, greatly reducing potential security threats.
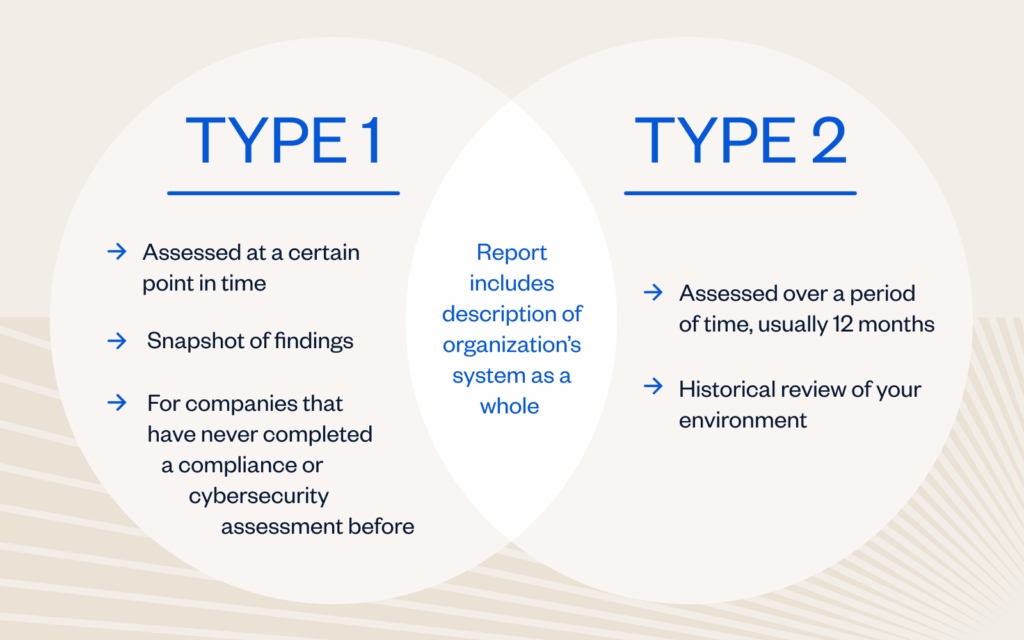
For organizations seeking a SOC 2 report, there are two attestation options available: Type 1 and Type 2. What type is best for your organization to prove compliance? Our experienced assessors break down the options so the path to SOC 2 compliance is clear.
What is a SOC 2 report?
A SOC 2 report highlights the controls in place that protect and secure an organization’s system or services used by its customers. The scope of a SOC 2 examination extends beyond the systems that have a financial impact, reaching all systems and tools used in support of the organization’s system or services. The security of your environment is based on the requirements within a SOC 2 examination, known as the Trust Services Criteria (TSC):
- Common Criteria/Security (required)
- Availability (optional)
- Processing Integrity (optional)
- Confidentiality (optional)
- Privacy (optional)
The difference between Type 1 and Type 2 reports
Which SOC 2 report should your organization choose? Read on to learn the difference.
SOC 2 Type 1 Report
Organizations that select a SOC 2 Type 1 report will evaluate the design and implementation of an organization’s system of internal controls as they relate to the in-scope TSCs. The report will include the management’s assertion, auditor’s opinion on the design and implementation of controls, a description of the in-scope system, and the controls that were independently tested by the auditor. This serves as a snapshot of an organization’s environment to determine if controls are suitably designed and in place.
SOC 2 Type 2 Report
SOC 2 Type 2 reports will evaluate the design, implementation and operating effectiveness of an organization’s system of internal control as they relate to the in-scope TSCs over a defined period of time, typically six to twelve months. The report will include the management’s assertion, auditor’s opinion on the design and operating effectiveness of controls, a description of the in-scope system, and the controls and test results that were independently tested by the auditor A SOC 2 Type 2 report provides a historical view of an organization’s environment to determine if the organization’s internal controls are designed and operating effectively.
What is a readiness assessment?
Now that you understand the difference between a Type 1 and Type 2 report, how can you best prepare for your SOC 2 examination? Consider these options from A-LIGN’s expert auditors:
- Traditional approach: A-LIGN will perform a formal Readiness Assessment that simulates a Type 1 or Type 2 audit and results in a report with recommendations from the auditor. This option is recommended for companies that don’t have many formal procedures or have never been through an audit before.
- Belay approach: This hybrid two-step approach has a smaller high-level gap assessment of key controls prior to the Type 1 SOC 2 examination. This approach saves time and costs and is designed for more mature organizations with formally established and implemented procedures who still have concerns or questions about their readiness for a SOC 2 audit.
Why A-LIGN?
A-LIGN is the leading provider of high-quality, efficient cybersecurity compliance programs. Combining experienced auditors and audit management technology, A-LIGN provides the widest breadth and depth of services including SOC 2, ISO 27001, HITRUST, FedRAMP, and PCI. A-LIGN is the number one issuer of SOC 2 and a leading HITRUST and FedRAMP assessor. The A-LIGN difference is:
- 17.5k+ SOC assessments completed
- #1 SOC 2 issuer in the world
- 200+ SOC auditors globally
Next steps
Ready to begin your compliance journey? Contact A-LIGN today to get started.
Is a Cloud Service Provider (CSP) ready to undergo the extensive FedRAMP authorization process? That’s what the FedRAMP Readiness Assessment Report (RAR) intends to find out.
A Third Party Assessment Organization (3PAO) will leverage the RAR to document and validate a CSP’s full implementation of the technical capabilities required to meet FedRAMP security requirements. Let’s take a look at what’s involved in a FedRAMP Readiness Assessment and the steps outlined in the updated FedRAMP RAR guide.
What Does a FedRAMP Readiness Assessment Entail?
Completing a RAR requires a 3PAO, such as A-LIGN, to:
- Confirm full implementation of the Cloud Service Offering’s (CSO) technical capabilities
- Understand how a CSO works and operates
- Validate what is implemented within the CSO
- Understand the key functionalities of the CSO and document the RAR in a way that is comprehensible by agency customers that may not have a strong technical background
- Verify that the stated authorization boundary of the CSO and the data flows within the system are practical, secure, and logical
While a Readiness Assessment is intended to determine a CSO’s readiness to achieve FedRAMP authorization, it does not guarantee it. CSPs can use the process as an opportunity to discover and remediate any deficiencies in a CSO’s capabilities, as well.
The RAR must specifically, clearly, and succinctly provide an overview of the system as well as a subjective summary of a CSO’s overall readiness. This includes rationale such as notable strengths and other areas for consideration. The 3PAO should answer RAR requirements and questions, stating what they found (observations and evidence) during their review, and, most importantly, how they determined whether a CSP adequately addresses the question area.
In a thorough 19-page document, FedRAMP provided updated guidance as well as templates for 3PAOs evaluating CSPs for readiness. Below, you’ll find a summary of the 12 steps 3PAOs should follow when preparing a RAR as outlined in the new guidance.
1. Validate the Authorization Boundary
Assessing any CSO for readiness begins by determining whether the offering has a clearly defined and maintainable authorization boundary. It falls on 3PAOs to perform full authorization boundary validation to ensure nothing is missing from the CSP identified boundary, and all included items are present and part of the system boundary.
This step also extends to the need for 3PAOs to conduct a discovery scan. This is intended to identify operating systems running on the network then map them to IP addresses, identify open ports and services, and gather rudimentary information on targeted hosts.
2. Identify All Data Flows and Stores Within and Throughout the Authorization Boundary
A 3PAO must validate the data flow diagrams (DFDs) and provide a written description of the data flows. Each DFD must be high resolution, reflect the same components as the authorization boundary diagram, and explicitly identify every location where federal data and metadata is in relation to the 3PAO system authorization boundary.
3. Determine Leveraged FedRAMP Authorizations
For a FedRAMP-leveraged CSO, a 3PAO must provide the specific details regarding this relationship. The leveraged offering must be listed on the FedRAMP Marketplace with a status of Authorized (not FedRAMP Ready or In Process). An Authorized status can only be achieved upon approval of a full assessment package by the Joint Authorization Board (JAB) or the Project Management Office (PMO). If a 3PAO is assessing a SaaS then it must ensure that subscriptions to underlying services (IaaS, PaaS) are accurately documented.
4. Determine External and Corporate Systems and Services
Within the RAR, a 3PAO must indicate a CSP’s connections to external systems and services, including corporate systems and services that are not part of the authorization boundary. It must divulge the use of third-party providers and external services / systems lacking FedRAMP authorization at the time of RAR completion. The 3PAO will also need to provide a mini analysis of the RAR external leveraged services and its risks.
5. Application Programming Interfaces (APIs)
While they are connections, APIs have their own category within the RAR. 3PAOs must identify each API a CSO uses.
6. Assess and Describe the Strength of the Physical and/or Logical Separation Measures within the System
A 3PAO must make an assessment of physical and/or logical separation measures based on very strong evidence, such as the review of any existing penetration testing results, or an expert review of the products, architecture, and configurations. In the absence of a penetration test, a 3PAO must provide a rationale for being able to prove that there is adequate segregation of tenants and data. 3PAOs must also analyze all border devices to ensure they provide appropriate segregation from other systems, and describe the methods used to verify the strength of separation.
7. Ensure Federal Mandates Are Met
3PAOs assessing Moderate and High baseline systems must ensure six federal mandates are met.
- Are FIPS 140-2 Validated cryptographic modules (IAW SC-13) consistently used everywhere cryptography is required? This includes all SC-8, SC-8(1), and SC-28 required encryption.
- Does the system fully support user authentication via Agency Common Access Card (CAC) or Personal Identity Verification (PIV) credentials?
- Is the system operating at Digital Identity Level 3?
- Can the CSP consistently remediate High vulnerabilities within 30 days, Moderate vulnerabilities within 90 days, and Low vulnerabilities within 180 days?
- Does the CSP and system meet Federal Records Management Requirements, including the ability to support record holds, National Archives and Records Administration (NARA) requirements, and Freedom of Information Act (FOIA) requirements?
- Does the system’s external DNS solution support DNS Security Extensions (DNSSEC) to provide origin authentication and integrity verification assurances?
The answer must be “yes” for all six questions before submitting the RAR.
8. Ensure DNSSEC Is in Place
It is incumbent upon the 3PAO to verify that the external authoritative DNS server replies with valid Domain Name System Security Extensions (DNSSEC) responses. Additionally, any external domain used to access a CSO must be verified as registered with a DNSSEC signature. The authoritative server is signed by the Top-Level Domain server, which is in turn signed by the root server. The entire signature chain will be checked by the recursive server, so any broken signature breaks the whole chain.
9. Verify FIPS 140-2 Validated Encryption within and throughout the System Boundary
For FIPS 140-2 validated encryption, all Moderate and High-level federal data and metadata must be encrypted for all DAR and DIT within and throughout the system boundary. CSPs or vendors using FIPS 140-2 validated modules are required to have a certified security policy stating how their products must be used to ensure their security.
10. Assess Security Capabilities Sections
3PAOs must conduct assessments of several of the system’s technical, management, and operational capabilities via a combination of interviews, observations, demonstrations, examinations, and on-site visits. The assessment must be done based on an accurate ABD and DFD and should not rely on a CSP’s written documentation and interviews.
11. Complete Executive Summary and Ensure Alignment with Entire Document
The Executive Summary must contain a number of items, including overall alignment with the NIST definition of cloud computing and a self-service portal. This document should also note whether the CSP is pursuing a JAB P-ATO or an Agency ATO, while highlighting the CSPs strengths and weaknesses. The executive summary also asks that 3PAOs describe risks associated with interconnections and with the external systems and services that are not FedRAMP Authorized. Organizations should be sure their final Executive Summary is exact, concise, easily understood and free of any marketing content that promotes their products or services.
12. Complete Each Security Control Capability Statement to Include the 3PAO Test Methodology
To successfully complete a RAR, 3PAOs must complete each security control capability statement in every section of the RAR, and convey the capability, supporting evidence, and any missing elements. The capability cannot simply be a copy and paste from the System Security Plan (SSP) but rather a fully addressed question and then the 3PAO should indicate how they interviewed, examined, and or observed the capability in place. Throughout the security control capability statement, we suggest a 3PAOs only answer “yes” if the answer is consistently “yes.” Partially implemented areas should be answered “no” with a description of what is missing to achieve a “yes”.
A-LIGN Can Help
Does the FedRAMP certification process seem overwhelming? A-LIGN can help by making the process seamless. As a top five FedRAMP assessor, we understand the FedRAMP journey from readiness to authorization.
Get in touch with us to learn how we can guide you to authorization.






